Starting tomorrow, we’ll extend the Early Access Program for Enhanced Protection with some new Intercept X features for you to test. Four new mitigation options will be added to endpoints that are participating in the EAP.
All four new mitigation options can individually be switched off or on – but as with other EAP features, they’ll be on by default. However, you will not yet see any detections based on these new features, as we're launching in silent mode first. Next week we'll switch to blocking mode.
We will post information on how to test these features later. Keep an eye on the “Recommended reads” section.
Versions
Devices with an updated endpoint will have the following versions of components and features:
- Core Agent: 2.5.3 BETA
- Sophos Intercept X: 2.0.16 BETA
- Sophos HitmanPro Alert: 3.7.15
EFS Guard
Intercept X can now protect files that are encrypted with EFS from Encrypting File System attacks.
Dynamic Shellcode Protection
Malware authors are increasingly using so called stagers: innocent little programs, that download and execute malware in memory, to avoid detection by traditional anti-malware applications.
Dynamic Shellcode Protection protects against such malware by monitoring the behaviour of applications. When it detects behaviour resembling that of stagers, it will intervene and stop the application.
CTF Guard
A vulnerability in a Windows component, only known as “CTF”, present in all versions back to Windows XP, allows a non-administrative, unauthorised attacker to hijack any Windows process, including applications that are running in a sandbox.
So, the Sophos Threat Mitigation team has developed a system-level exploit mitigation that prevents abuse of the CTF subsystem. This new component intercepts and blocks applications that attempt to exploit CTF.
ApiSetGuard
ApiSet Stub DLLs are DLLs that serve as a proxy to maintain compatibility between older applications and newer operating system versions.
Attackers may place malicious ApiSet Stub DLLs to manipulate its functionality, or bypass tamper protection and terminate anti-malware protection.
ApiSetGuard helps prevent an application from side-loading a malicious DLL that poses as an ApiSet Stub DLL.
Settings
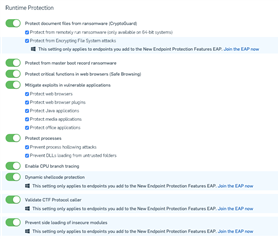
The following screenshot shows the four settings as they can be found in Central:
“Protect from Encrypting File System attacks” (EFS Guard)
“Dynamic shellcode protection”
“Validate CTF Protocol caller” (CTF Guard)
“Prevent side loading of insecure modules” (ApiSetGuard)
Note that although the new individual features are switched on by default, they will not be enabled if their parent feature is off. For example, when you have switched off "Protect document files from ransomware (CryptoGuard)", the new features "Protect from Encrypting File System attacks" will have a checkmark next to it, but will not be enabled.