Hi guys,
I have searched myself silly and dont get anywhere, so I come before you.
A little preface:
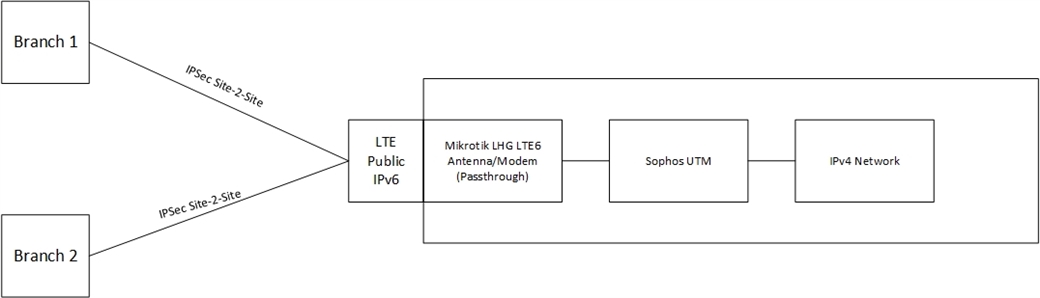
We are a small group of companies (headquarter/main company and 2 daughtercompanies/branches). There are 2 IPSec Site-2-Site tunnels established between the two branches and the headquarter (we, the HQ, are on respond since the branches dont have static IP's yet) - they work on a RDS/Terminalserver in our infrastructure.
We have just the worst WAN connection (Vodafone cable) - atrocious. Its on and off again - major disruptions etc. We are so remote that we dont have any alternatives like fiber (the DSL connection is solely for our VPN connection to the hosted cloud VoIP PBX of Deutsche Telekom), so we are stuck with Vodafone. It wasnt always as bad as now, but I have to provide redundancies now since 3 companies are affected.
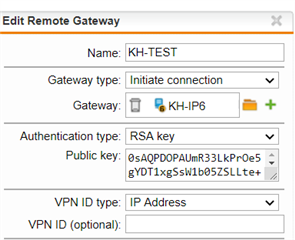
I asked our mobile provider for a data plan and they can offer me a LTE data plan with a static, public IPv6 address. According to the sales rep I spoke to, it will allow incoming connections as well, but I need to verify with one of their technicians directly - lets assume it is.
I planned something like this:
I really dont want to establish a full blown IPv6 network in parallel to the IPv4. I saw here and there some blog posts and comments on the net (and Sophos forum) explaining the translation of IPv6 traffic to IPv4 and vice versa.
How would I realise that on the UTM? With a DNAT rule?
Im eternally grateful for any input.
Thanks!
This thread was automatically locked due to age.