Hi!
The IPS on one of our Sophos XG's is blocking Splashtop from connecting properly, and its being blocked as
Here is what I have done so far, but no luck.
FQDN Host
sn.splashtop.com - resolves 54.204.11.246, 50.19.125.112
splashtop.com - resolves 23.23.164.150, 50.17.197.204
FQDN Host Group
IPS_Ignore - added sn.splashtop.com and splashtop.com
Custom IPS Signature
Name: Splashtop
Protocol: TCP
Rule: srcaddr:54.204.11.246;srcaddr:50.19.125.112;srcaddr:23.23.164.150;srcaddr:50.17.197.204;
Severity: Warning
Action: Bypass
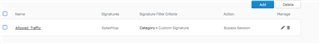
Custom IPS Policy
IPS_Ignore
Rule Name: Allowed_Traffic
Added Custom Signature : Splashtop
Action: Bypass Session
Created Firewall Rule: IPS:Allow
Position: Top
Source: WAN > FQDN HG IPS_Ignore
Destination: LAN > Any > TCP
Intrusion Prevention: IPS_Ignore
Hit save and nothing happens, the IPS log is still filling up with Dropped packets.
This thread was automatically locked due to age.