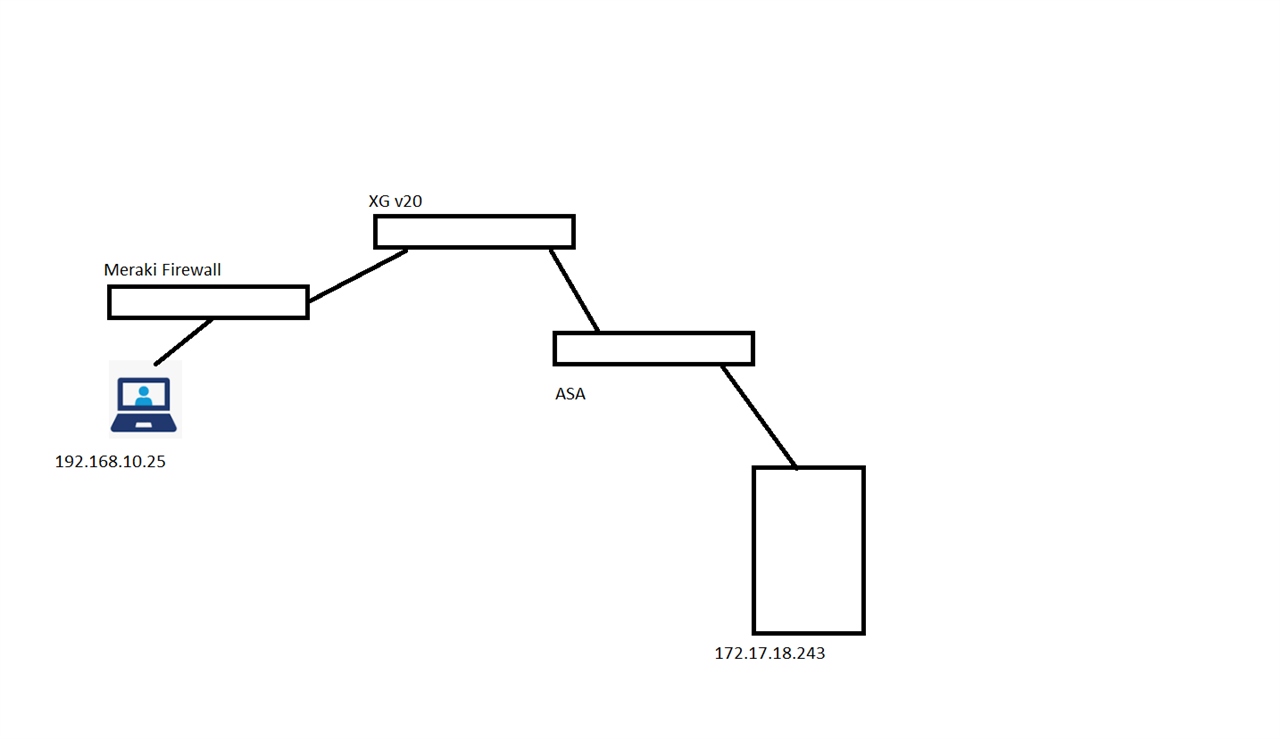
See the image below for the layout. Users behind the Meraki firewall need to reach the server behind the ASA firewall by traversing the Site2Site network between the Meraki and XG, then over the Site2Sit between the XG and ASA.
We know it's possible if we include the Meraki LAN in the config between the XG and ASA, but we would like to avoid that, if possible, for several reasons.
I tried setting up NAT based on these instructions:
In my case, instead of the remote network needing to reach the Head Office DMZ, it needs to reach a network that is across another Site2Site VPN, but it's not working. Maybe I set something up wrong or maybe it won't work because there are 2 VPN connections involved?
This thread was automatically locked due to age.


