Case:
Client with Sophos Endpoint does DNS Request to XGS as resolver
DNS Response IP is seen in a 3rd Party Threat Feed
Firewall generated ATP Alert and sends red Heartbeat to Sophos Central
The Client is isolated by Sophos Central.
Now, how can I find out which hostname the client requested in DNS request? The IP is from a huge Google IP List.
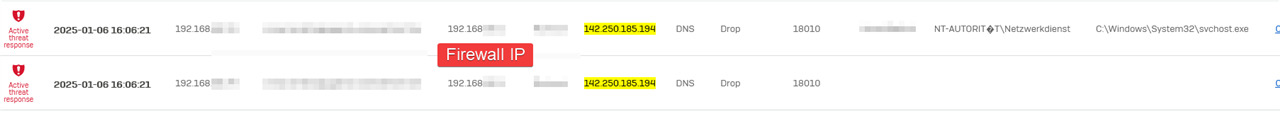
The firewall is not logging DNS requests unfortunately.
Datalake Query was not bringing expected results.
This thread was automatically locked due to age.
