hi there,
since we upgraded our XG to 18.0.4 we have an issue with the traffic (e.g. DNS / icmp) originated from the firewall itself.
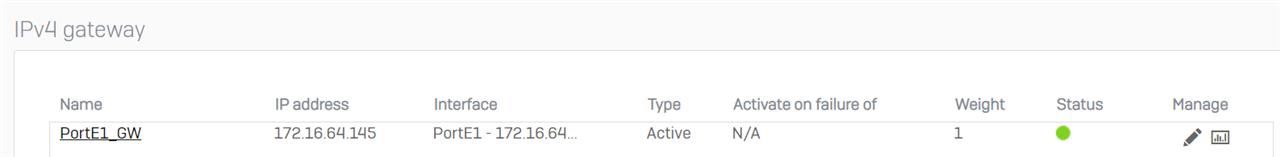
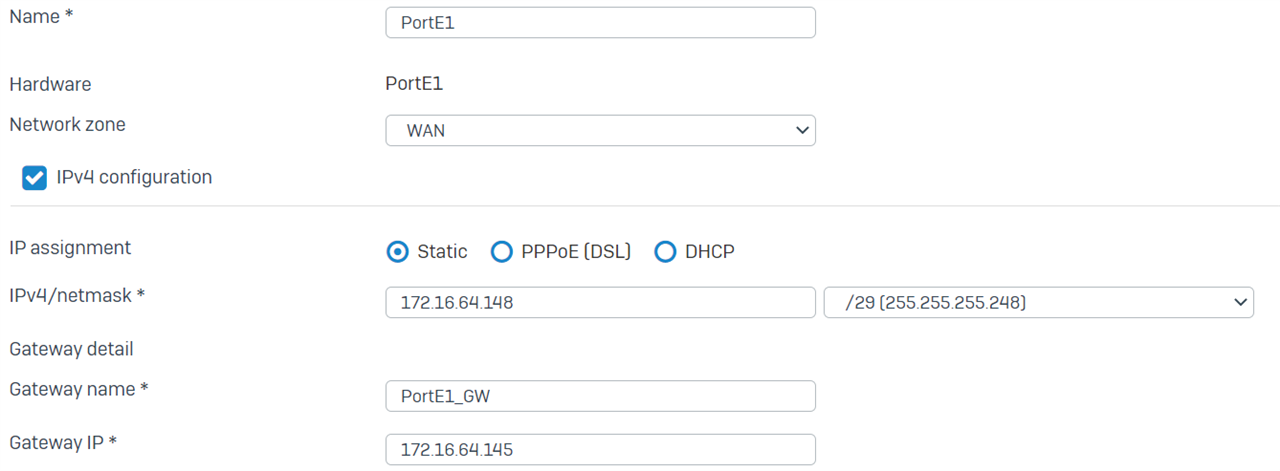
We have a full-tunnel IPsec VPN configured for all client subnets to our data center and it seems that routing for the firewall itself is broken now.
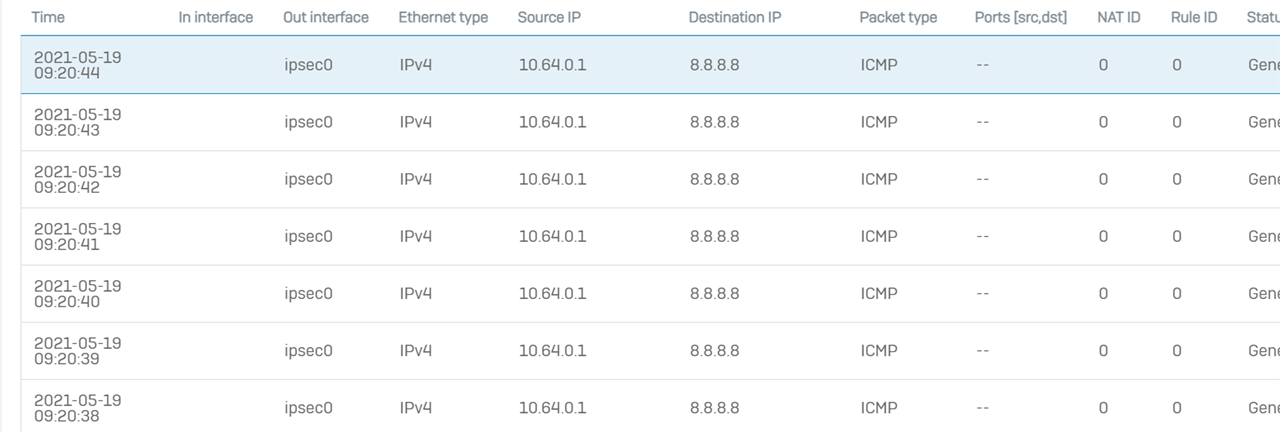
SG230_WP02_SFOS 18.0.4 MR-4# ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
^C
--- 8.8.8.8 ping statistics ---
10 packets transmitted, 0 packets received, 100% packet loss
------------
SG230_WP02_SFOS 18.0.4 MR-4# traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 46 byte packets
1 x.x.x.x (IP of Remote VPN-Gateway) 11.644 ms * *
2 * * *
3 * x.x.x.x (IP of Remote VPN-Gateway) 11.576 ms 37.854 ms
------------
SG230_WP02_SFOS 18.0.4 MR-4# nslookup www.google.de
;; connection timed out; no servers could be reached
------------
I know there is a KB article (Sophos XG Firewall: How to Route Sophos Firewall Initiated Traffic Through an IPSec VPN tunnel), but my issue is the exact opposit.
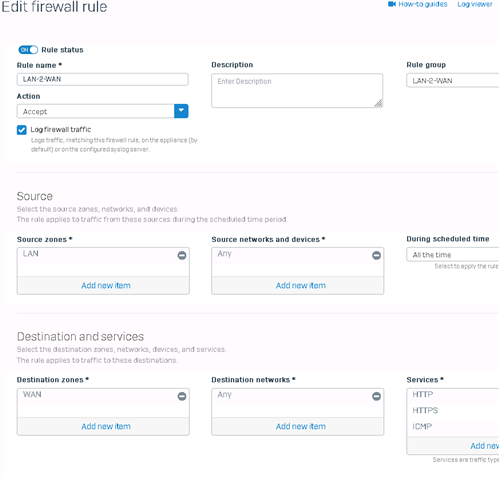
i do not have any rules like described configured.
------------
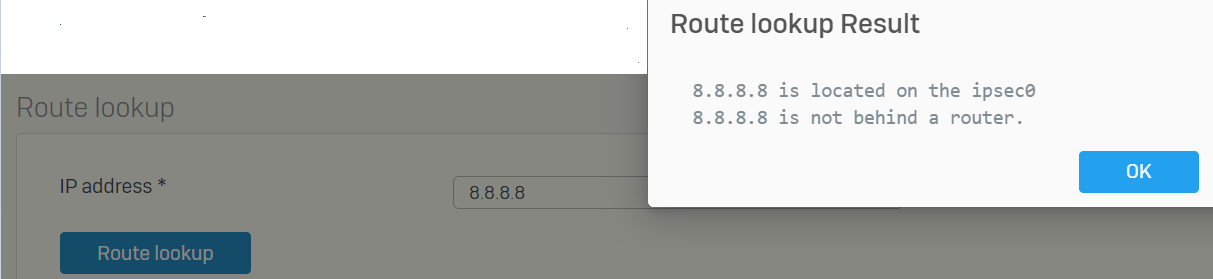
edit: Output of route lookup:
8.8.8.8 is located on the ipsec0 8.8.8.8 is not behind a router.
------------
Anybody had similar issues or any idea how to solve this?
Thanks
This thread was automatically locked due to age.