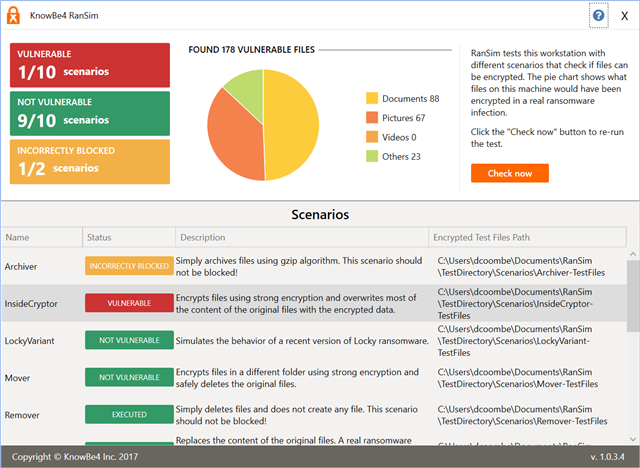
I recently run KnowBe4's ransomware simulator on my desktop. Whilst it appears that Sophos did better than most of their competitors it still missed InsideCryptor. I'm looking for an explanation on how this could happen. Is it a configuration problem? An issue with the simulator or did CryptoGuard drop the ball and Sophos is working on this?
This thread was automatically locked due to age.