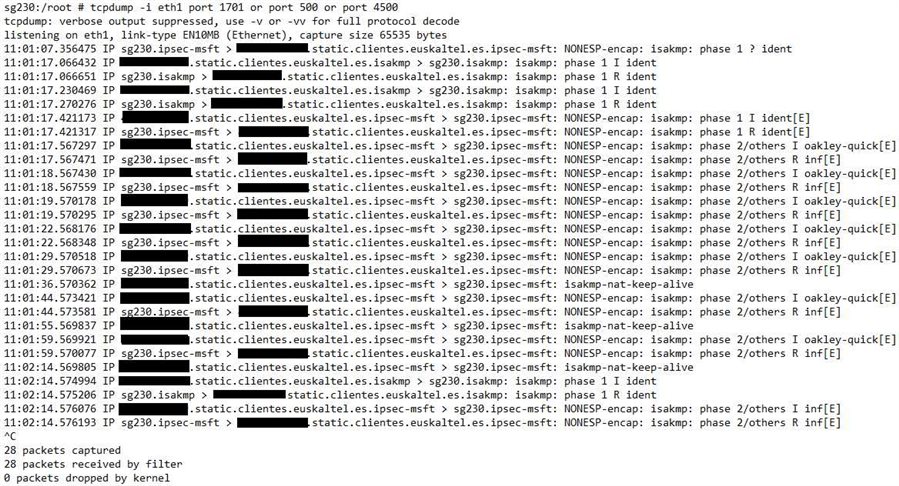
We have an SG230 in a remote facility which we must make VPN connections to, preferably over L2TP/IPsec. The problem is that they haven't provided us with a public IP per se, instead they have given us a private IP which is 1:1 NATed in their firewall and we are able to access ours over the Internet with the "provided" public IP.
As of now it is impossible to establish the said VPN connection. I have tried setting the VPN ID with the true public IP and NAT-Traversal is enabled but with no luck.
Is the UTM incapable of setting a L2TP/IPsec VPN connection when the WAN port is configured with a private IP instead of a public one?
PD: The SSL VPN works, but we need the L2TP/IPsec for our system to work correctly.
This thread was automatically locked due to age.