Dear all,
Due to the recent update of the ipsec cipher in Macos (11.1.x) and based on my research also on IOS and Android it looks like that the glory times are over to unify windows, android and macos clients with the built-in l2tp over ipsec.
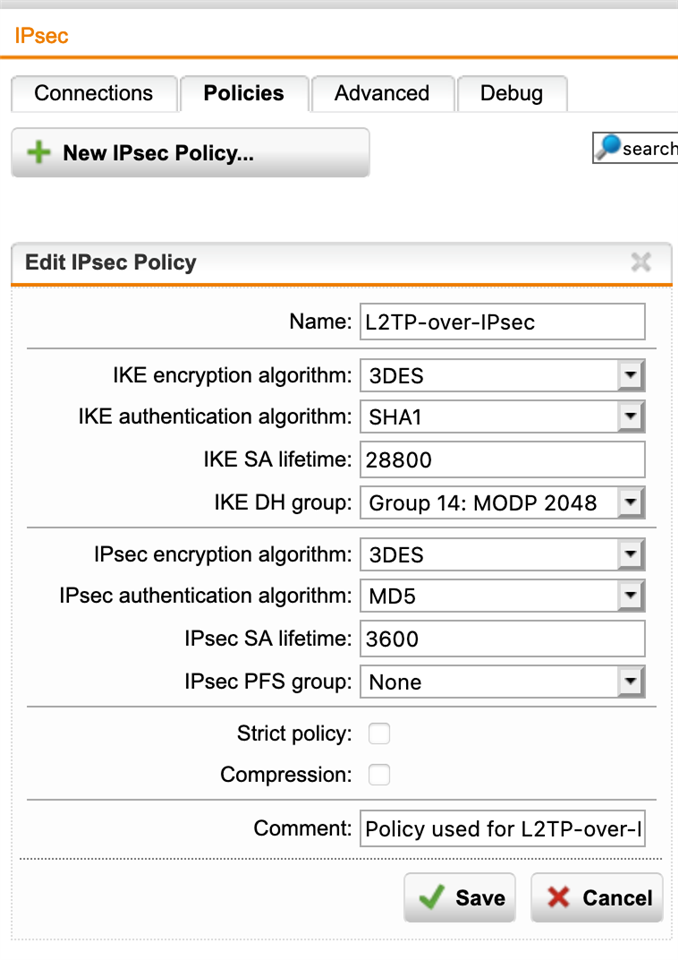
I do only have Macos and Windows 10 Users, however I am not sure If Windows is able to deal with the required changes of the Ipsec Policies which Macos 11.1.x requires ?
Refs.
https://www.reddit.com/r/MacOSBeta/comments/ih22h9/vpn_l2tp_over_ipsec_stopped_working_after/
https://support.sophos.com/support/s/article/KB-000036559?language=en_US
https://community.sophos.com/utm-firewall/f/german-forum/123860/l2tp-ipsec-konfiguration-ios
Furthermore I double checked the default Policies which are really not 2020 /3des, sha1, etc. and because it is a very bad time to start via try and error on Remote settings (u know corona) I would like to know If there is a sophos best practice doc. for this ?
Thanks and stay safe !
This thread was automatically locked due to age.


