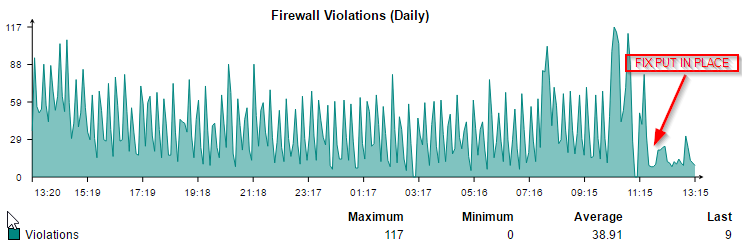
All of a sudden I'm seeing a lot of FW Rule 60001 in the FW log.
What used to be a very quiet FW is now very chatty with spikes of 60001 drops every 5-10 minutes. I haven't made any configuration changes. Any idea where I start to begin troubleshooting?
/var/log/packetfilter.log:2016:12:05-11:55:51 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:51 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:51 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:51 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:51 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:52 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="64.4.54.253" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="102" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:53 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
/var/log/packetfilter.log:2016:12:05-11:55:55 sophos ulogd[4400]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60001" initf="eth1" srcmac="00:17:10:93:fc:96" dstmac="00:0c:29:2a:92:30" srcip="216.58.192.238" dstip="###.##.###.###" proto="1" length="576" tos="0x00" prec="0x00" ttl="58" type="11" code="1"
This thread was automatically locked due to age.