Hey there,
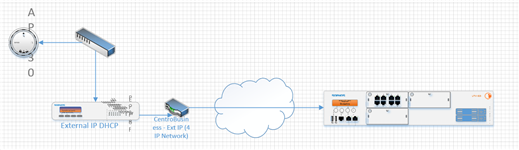
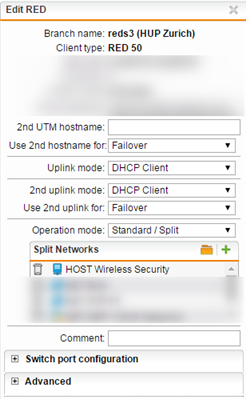
i have 3 REDs deployed and one HQ Firewall with 5 other branches connected through managed MPLS.
After exchanging the internet router at one RED branch the wireless authentication for the notebooks stopped working. This is only happening in this office.
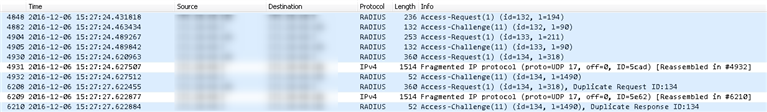
I already working with a partner and Sophos on this but it does not seem that there will be a solution. We traced the packages to and from the RADIUS (Windows 2012 R2 NPS), which i migrated from a Win 2008 because Sophos said it has something to do with the RADIUS Server (how can it be the radius server if it works for 7 other offices?), but it just gets no accept.
There is also no log entry in the event log. The accounting log says "Everything OK! Access granted"
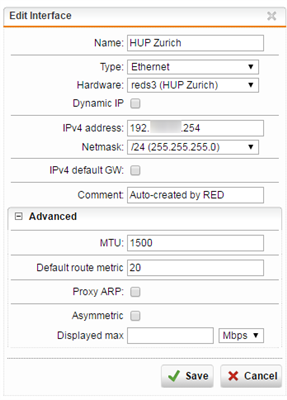
The RED has (now) an external IP from the router. The router has no firewall and the connection is stable.
We have the same configuration in another office in Vienna and there the wireless works fine.
I now have set up a Wireless with PSK but this cannot be the solution.
Anyone can help me with this?
Best regards
Stephan
This thread was automatically locked due to age.