Hi there,
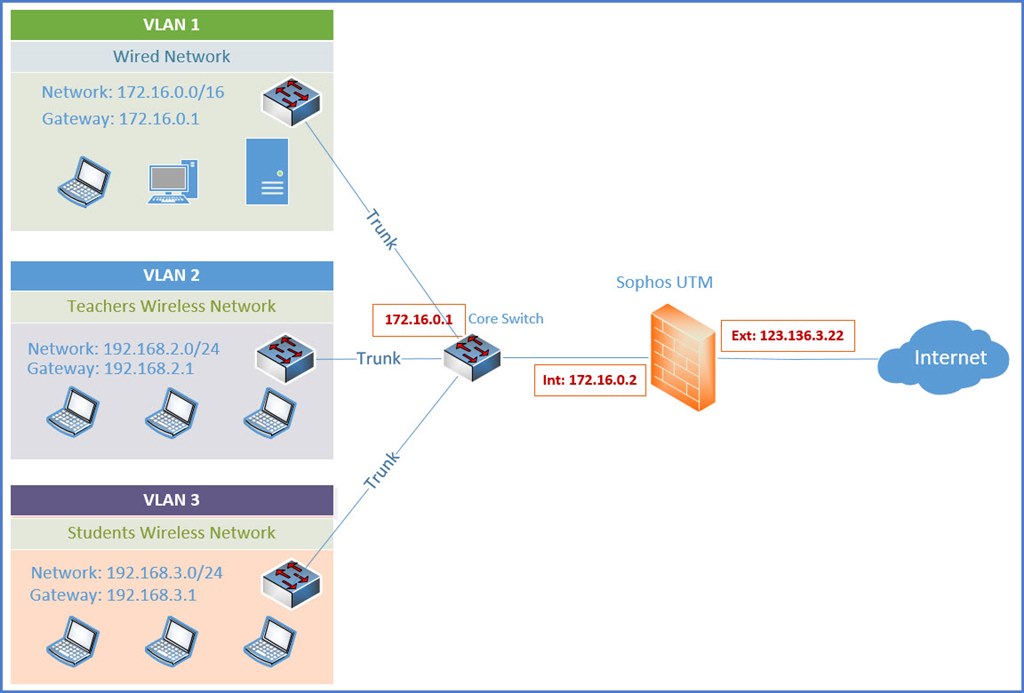
During the installation of Sophos UTM I chose IP address for an internal interface from the VLAN-1 network (172.16.0.2) and IP address for the WAN interface (123.136.3.22), which was given to us by our ISP. Please refer to the diagram below.
Right now computers from VLAN-1 (172.16.0.0/16) can browse Internet through Sophos UTM.
We also have two additional VLANs for wireless computers.
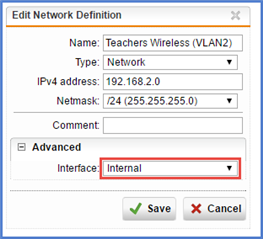
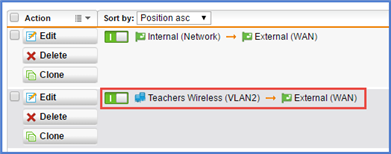
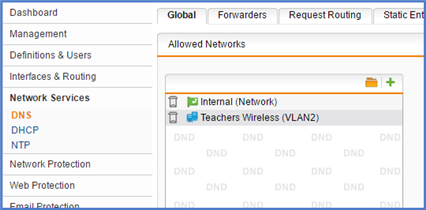
Could you please advice on what exactly needs to be added in Sophos UTM so that the users from wireless network (VLAN-2 and VLAN-3) could browse the Internet too?
I would assume that the static routes need to be added in Sophos UTM. A bit confused with the option of the route type - interface/gateway route?! Have no idea what blackhole route is, so I might not need to use it for my topology.
Besides the static route, do I need to create any firewall rules, NAT or masquerading rules?
My Sophos UTM has few spare interfaces. Would you recommend creating new dedicated interfaces for VLAN-2 and VLAN-3?
Thanks in advance.
This thread was automatically locked due to age.