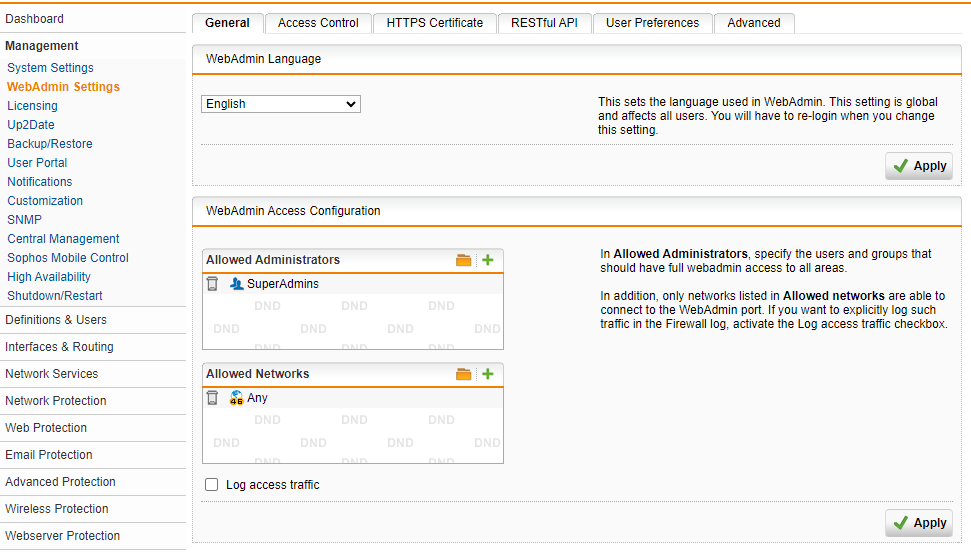
I've had some clown this morning in the last 7 hours attempt multiple times to gain entry to the web admin panel on our Sophos UTM9 firewall. I didn't think Sophos would be silly enough to put the web admin panel login ability on red (interface), good thing it's a decent password.
We use the Sophos VPN client to gain internal access so don't actually need anything really on the external side and whilst I've looked I can't find anywhere that would lockout the admin login to red.
Could someone please tell me if it's possible and where the setting would be located. I've upped the lockout to 2 tries / 2 hours lockout / drop locked out packets but I'd rather have a cure than prevention.
This thread was automatically locked due to age.