Hello,
We have to log all accesses to certain client systems from now on "for reasons". And actually in such a way that these accesses can be assigned to specific employees.
Question 1:
This should be done for http accesses via the WebProxy (running in transparent mode) as well as all other protocols, especially https and SSH.
Can the UTM do this and if so, how do I set it up?
Question 2:
In perspective, I would like to have a resolution of IP addresses to persons, as I can hardly reconstruct retrospectively who got which DHCP address at what time with which device. There is an extremely loose BYOD policy here :-(
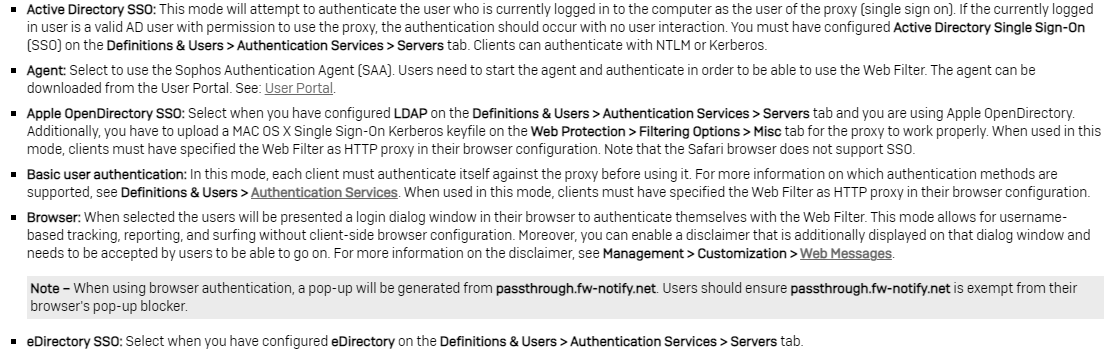
Is there a possibility that access to the customer networks is only allowed after logging on to the UTM?
This should work from OSX, iOS, Windows and Android, from the LAN and from the VPN.
Many thanks for your ideas!
lg - Chris
This thread was automatically locked due to age.