Hello,
today it seems like the RBL Pattern is broken, some E-Mails are getting blocked who are not on the Blacklist.
Anyone else
Greetings Felix
This thread was automatically locked due to age.
Hello,
today it seems like the RBL Pattern is broken, some E-Mails are getting blocked who are not on the Blacklist.
Anyone else
Greetings Felix
Resolution
Issue is not due to Sophos UTM, rather due to Spamhaus' policy regarding lookups from Public DNS providers.
Option 1:
Uncheck "Use recommended RBL" and enter in a custom RBL if necessary.
Do not use cbl.abuseat.org as a custom RBL at present if you use public DNS.
http://www.anti-abuse.org/multi-rbl-check/ Contains a listing of common RBLs
Option 2:
Under Network Services>DNS>Request Routing add cbl.abuseat.org to the domain field and then either directly add the Spamhaus IP or an alternate DNS server to not forward this domain via public DNS.
Resolution
Issue is not due to Sophos UTM, rather due to Spamhaus' policy regarding lookups from Public DNS providers.
Option 1:
Uncheck "Use recommended RBL" and enter in a custom RBL if necessary.
Do not use cbl.abuseat.org as a custom RBL at present if you use public DNS.
http://www.anti-abuse.org/multi-rbl-check/ Contains a listing of common RBLs
Option 2:
Under Network Services>DNS>Request Routing add cbl.abuseat.org to the domain field and then either directly add the Spamhaus IP or an alternate DNS server to not forward this domain via public DNS.
I think you're making it a little too easy for yourselves... .Anyone who relies on the default setting does not initially know why it suddenly becomes a problem. After all, it worked for years and it's not funny if you don't know why emails are suddenly rejected.
Could you please explain why this is a problem with public dns ?
I thought all RBLs would be contacted directly for RBL checks and not via dns forwarder configured in the utm.
We have big problems with our customers because of this problem to explain the root cause.
I completely agree to Christoph!
We had this situation at several customers yesterday and had to help them changing the default settings to a working solution.
This should be clearly communicated to all customers together with a recommendation how to overcome this situation.
Nobody is interested in accusing Sophos wether it's their "fault" or not.
Mit freundlichem Gruß, best regards from Germany,
Philipp Rusch
New Vision GmbH, Germany
Sophos Silver-Partner
If a post solves your question please use the 'Verify Answer' button.
I don't know the technical details, why SPAMHAUS don't like Public DNS Resolver. I believe, that the public Resolver don't deliver the same Information and they are not able to control the use.
However, topic 1.1.3 from the terms of use say:
The network originating the DNS Query must be identifiable. This means you must query the Spamhaus DNSBL Public Mirrors from a recursive resolver run on your own network or from a public resolver which supports ECS.
Source: https://www.spamhaus.org/organization/dnsblusage/
So i set the default DNS resolver to something like Google oder Quad9 and made an additional requesting route only for "cbl.abuseat.org" to the DNS resolver from the "Deutsche Telekom". That's already my Internet provider.
So I believe, if your provider is someone like for example "1 & 1", you have to take their DNS resolvver.
My solutions works for me without any problems.
Hi,
this might work some time I think. The major Problem is, large customer must register with spamhaus. (https://www.spamhaus.com/faqs/) The Barracuda entry.
This seems not to be done by UTM automatically. Using Spamhaus RBL might end in false positives.
UTM seems not to check against the return codes:
| Return Code | Zone | Description |
| 127.255.255.252 | Any | Typing error in DNSBL name |
| 127.255.255.254 | Any | Query via public/open resolver |
| 127.255.255.255 | Any | Excessive number of queries |
may
Astaro user since 2001 - Astaro/Sophos Partner since 2008
It's clear if you read the usage terms (https://www.spamhaus.org/organization/dnsblusage/)
Look at 1.1.3
I think forwarders like Quad9 produce excessive load to Spamhaus so they are rate-limited or even blocked because the original source of a query can't be identified. So Spamhaus can't differentiate if the queries came from 1 or from 100000 diffrent users.
It's possible to get a subscription. With a subscription you get a key to query the Spamhaus servers and they can clearly identify the query source.
Looks to me like Sophos is using the free Spamhaus DNSBLs but the customer pays Sophos for E-Mail security??
Wouldn't it be maybe also a (better) solution to use the "Request Routing" function of the UTM? Under "Network Services" -> "Request Routing" specific routes for zen.spamhaus.org could be added to have their NS servers be queried when the resolution is being tried. I think such an entry would be a beginning (there are waay more NS servers from spamhaus):
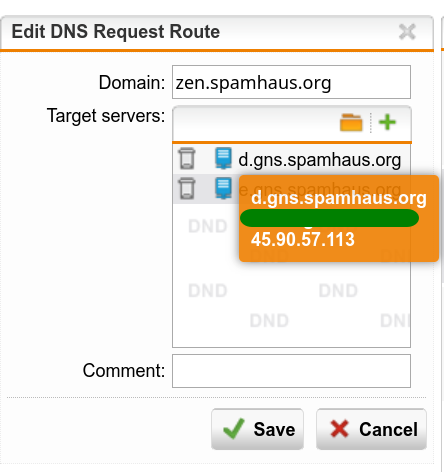
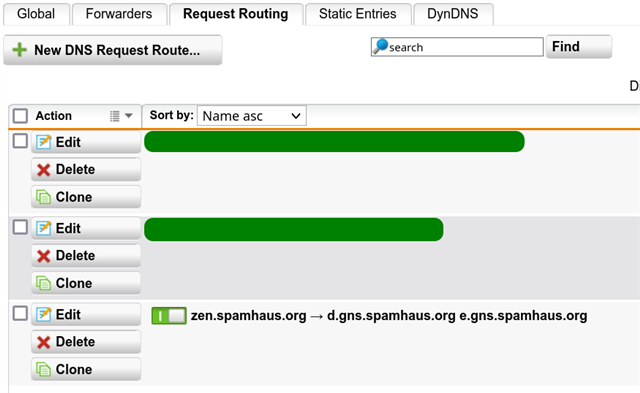
Wouldn't it be a nice if Sophos pais for the RBLs? We wouldn't have this problem if Sophos does. We pay for E-Mail security.