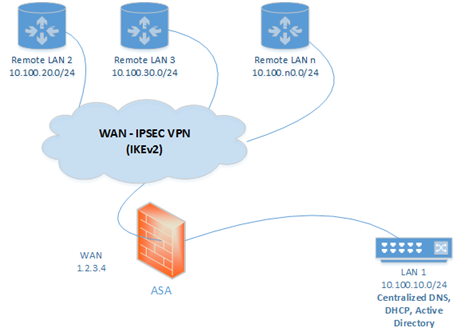
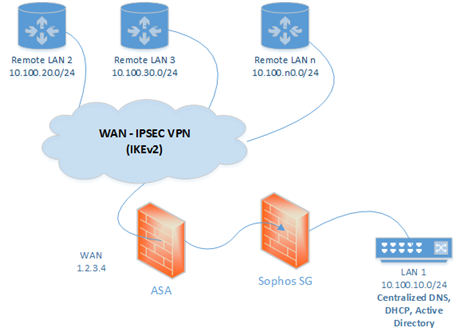
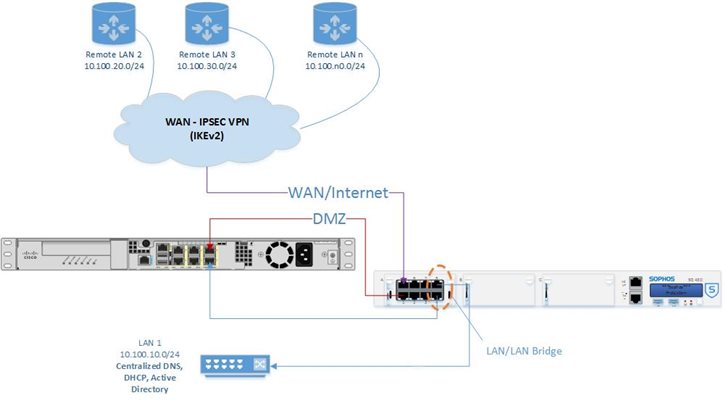
I wish to deploy our UTM inside of our existing ASA. I have many sites connected IPSEC (IKEv2) to our ASA, and all traffic is tunneled from all remote sites to the ASA. I wish for the UTM to perform its security functions (except Site to Site VPN) on all traffic, including the tunneled remote VPN sites and local LAN. Diagrams below. Sophos support tells us that they do not provide deployment assistance, but can help with configuring commands if we know what we want to do. So, I ask you all: how can I scan and protect all traffic from all sites on this spoke and hub setup.
Current State:
Future State:
This thread was automatically locked due to age.