Hi all,
Since days we have the following entries in the Advanced Thread Protection
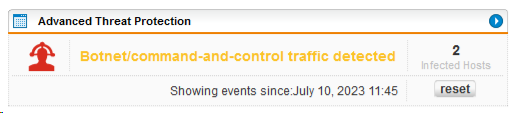
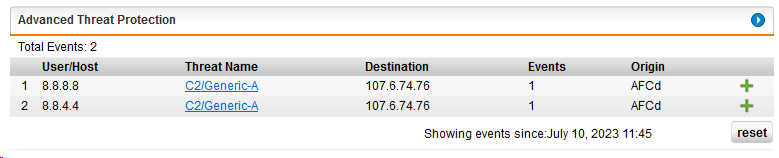
One physical site a) Sophos UTM, other physical site b) Sophos XG
Assumed it is an Advanced Persitance Thread, how we can get rid of it?
KR
Olli
This thread was automatically locked due to age.


