Hi
I setup Site-to-site VPN by IPSec using C2821 and SG115.
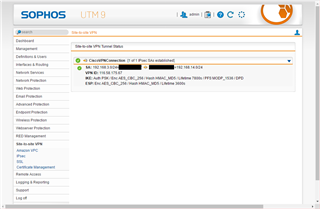
It looks like to be connected from looking Site-to-site VPN Tunnel Status.
but, it can't response by ping ,eachother.
And ,this situation is reproducted when using C2921 instead of C2821.
don't you have any ideas that I should do to solve this trouble? please.
[Base information: IP address]
Cisco's connected Grobal IP adress : 10.10.10.10
Cisco sides Local IP address : 192.168.14.0/24
SG115's connected Grobal IP adress : 20.20.20.20
SG115 sides Local IP address : 192.168.3.0/24
[config of C2800]
crypto isakmp policy 1
encr aes 256
hash md5
authentication pre-share
group 5
lifetime 7800
crypto isakmp key pre-share-Key address 20.20.20.20 no-xauth
!
!
crypto ipsec transform-set TUNNEL1 esp-aes 256 esp-md5-hmac
!
crypto map TUNNEL 10 ipsec-isakmp
set peer 20.20.20.20
set transform-set TUNNEL1
set pfs group5
match address 102
!
interface GigabitEthernet0/0
no ip address
ip nbar protocol-discovery
ip virtual-reassembly max-reassemblies 128
duplex auto
speed 100
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface GigabitEthernet0/1
ip address 192.168.14.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface Dialer0
ip address negotiated
ip nat outside
ip virtual-reassembly max-reassemblies 1024
encapsulation ppp
ip tcp adjust-mss 1398
dialer pool 1
dialer idle-timeout 0
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname ************.net
ppp chap password 0 ***********
crypto map TUNNEL
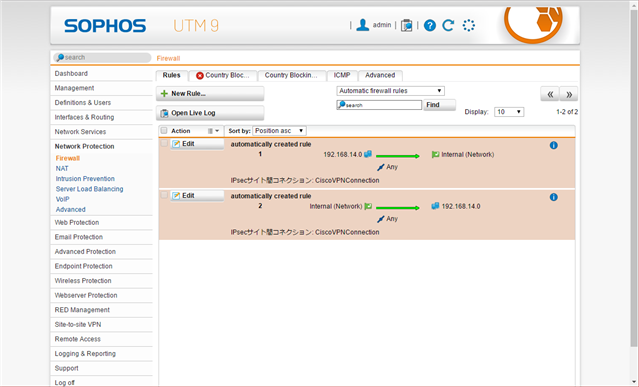
access-list 102 permit ip 192.168.14.0 0.0.0.255 192.168.3.0 0.0.0.255
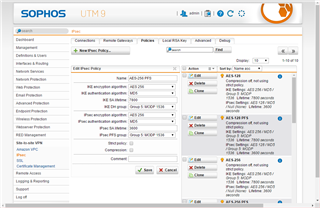
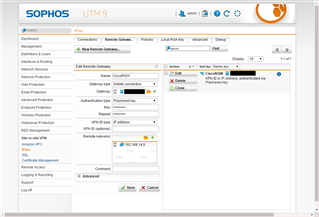
[SG115 Setting]
Using Default policy [AES 256 PFS] and Setting RemoteGateway like this.
[Live Log of SG115]
This thread was automatically locked due to age.