Hi all,
We're currently in the middle of transferring everything across from our old IPCop server to the Sophos UTM (in the hopes of retiring IPCop).
I've copied across the DNAT rules (with automatic firewall rules), put in the static routes and have ensured our public-facing router is configured correctly.
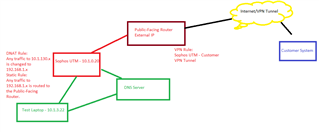
However, we're unable to connect to our customer VPNs. From their perspective, they just need to open up their end to our public-facing router, which is what they've done. But from ours we need to ensure traffic from our UTM is being directed to the correct locations.
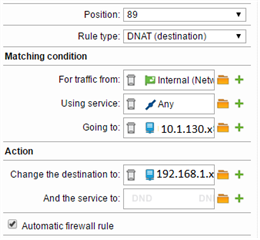
I'm currently testing out one of the VPN connections but none of them are currently working. I've reduced the test to one specific server we often RDP to and have tested it's working on my PC (using the old connection we're trying to replace). On the new connection however, I'm unable to connect to it. I've checked the firewall log and can see the NAT rule I've placed - it shows traffic from the test laptop (which has the UTM set as the default gateway) going to the internal IP address we have for their server (DNS is managed by our Domain Controller). The DNAT rule says any internal traffic (10.1.0.0/21) using Any service going to the internal IP address we have for their server (10.1.130.x) should be changed to an IP on the customer's VPN address (i.e. 192.168.1.x).
We then have a static route saying all traffic for the customer's VPN network is to be routed to our public-facing router. I've then simply added our UTM onto the policies already established so the traffic should be passing from our router into the VPN tunnel.
The only place I can think it's failing is the DNAT rule. I don't actually see anything in the log file that suggests the IP 10.1.130.x has changed to 192.168.1.x. And once the IP has been changed by the DNAT rule, do I need to do anything else to ensure it is forwarded to our public-facing router (like another firewall rule saying to allow traffic from 192.168.1.x to the public-facing router)?
Below is a rough networking diagram to show the set-up.
Any help would be greatly appreciated :)
Regards,
Rob
This thread was automatically locked due to age.