Hello ,
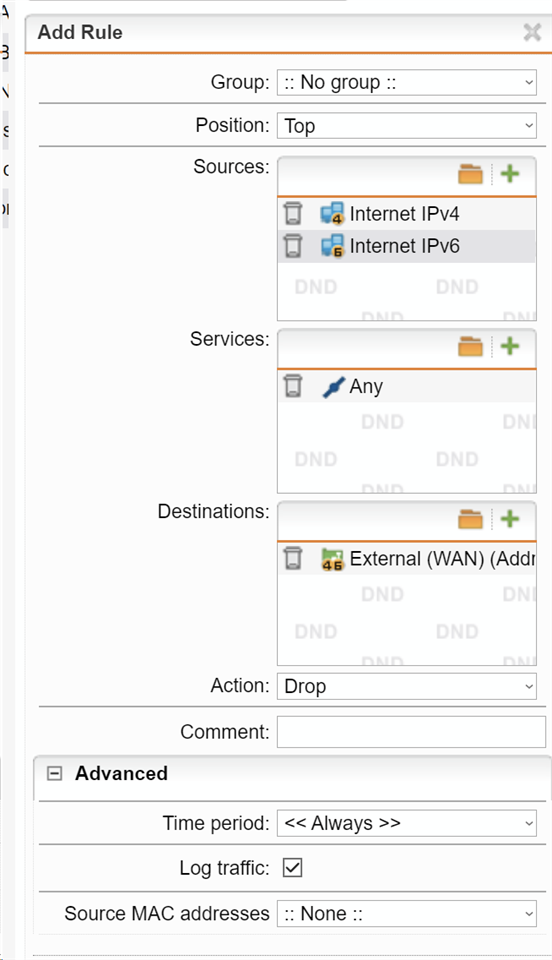
I have a sophos UTM 9.716-2. I can't connect via hostname from noip.com on port 4444. I can't connect via ssl vpn too. My ISP has cg-nat . I think cg-nat is the problem.
I try with success to setup a vps with wireguard to avoid cg nat. Now I got a new IP from vps. If I write on GNU/linux traceroute public ip show that I am not on cg-nat.
I have in Webadmin settings -> General -> Allowed Networks has ANY, Internal (Network), VPN Pool (SSL) but problem not solved.
How can I ascess web admin via wan ???
This thread was automatically locked due to age.