Hello,
I found this 12 year old thread,
Block certain mac address to get ip from dhcp pool
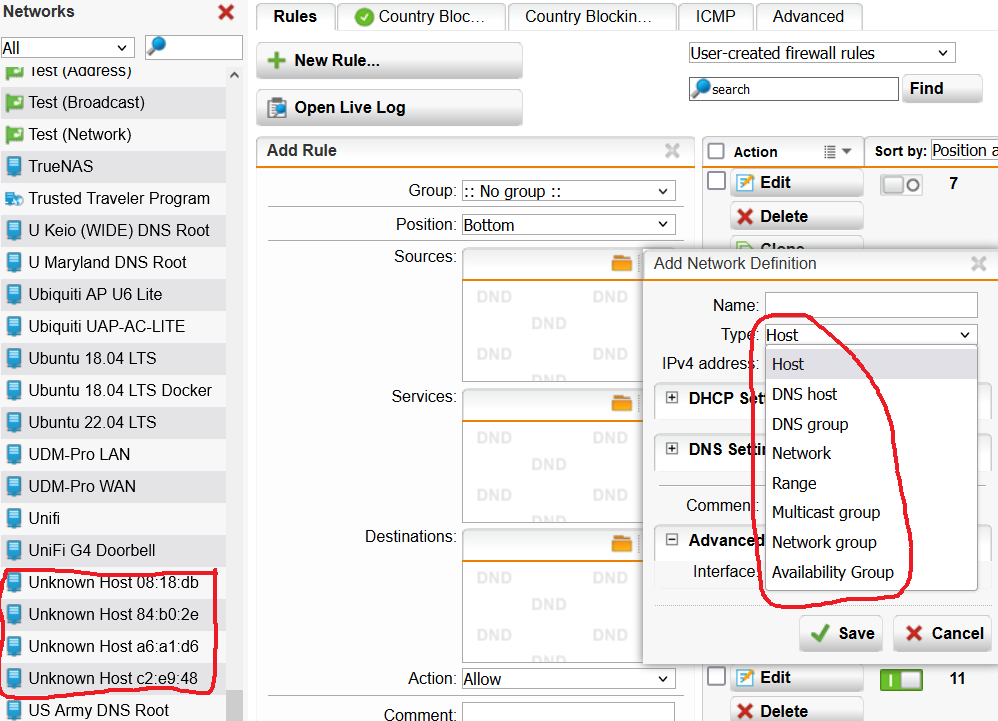
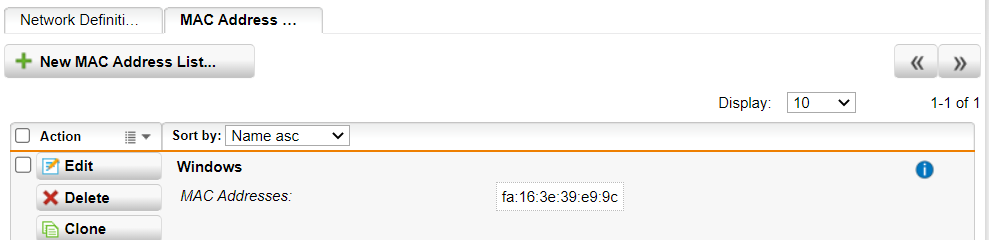
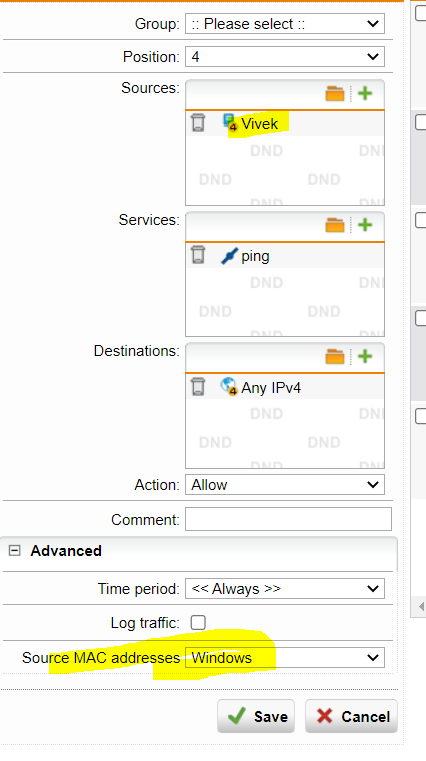
and would like to know if it is now possible to prevent the assignment of IP addresses to specific MAC addresses.
Thanks
This thread was automatically locked due to age.