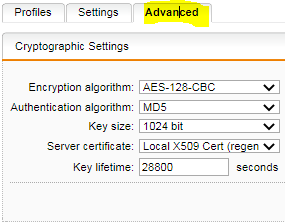
So far, SSL VPN under the UTM has worked without any problems with the OpenVPN client.
In the meantime, OpenVPN 2.6RC1 has been released, which requires AES-GCM ciphers. Only with a change in the config file the OpenVPN client can still connect.
e.g.
---
data-ciphers AES-128-CBC
data-ciphers-fallback AES-128-CBC
---
It is a pity that the ciphers are not unlocked under SSL VPN.
Under IPSec they are available. So it is probably a purely strategic decision by Sophos not to enable them under SSL VPN.
This thread was automatically locked due to age.