Short of enabling logging for all firewall rules, is there some way of seeing which rule allowed or blocked certain traffic? Something in console/command line?
This thread was automatically locked due to age.
My network topology is;
ONT (wan) -- UTM -- Vlans
The ONT is hardcoded to a 192.168.1.254 ip. UTM has an additional address defined for the wan interface (in addition to dhcp).
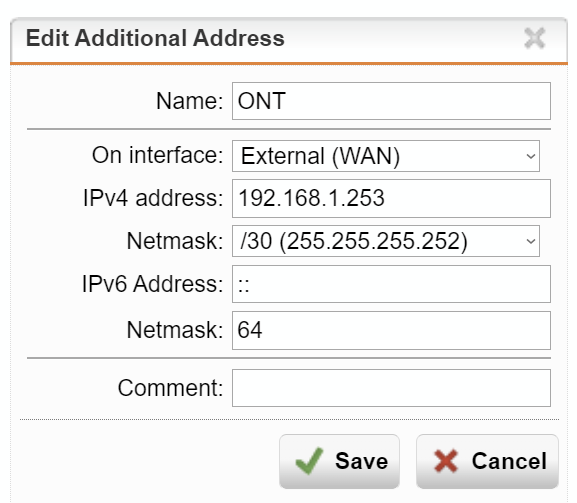
I set this up 3 years ago so I could access the ONT from one of the vlan interfaces. Was trying to remember if I did it as a DNAT rule or just a firewall rule. Turns out it's the latter. BUT, I couldn't find an explicit rule that allowed such access. It wasn't the web proxy either as disabling that still allowed access. There's about 60 active firewall rules in place. One of them is responsible for allowing this traffic.
You'll need to grow a thicker skin if you considered my response an attack.
I was simply responding to your reply which didn't make much sense in the context of what I posted just above it. Sure, I can go back and edit each of the 60+ active rules to enable logging. This type of logging is not enabled by default. Then the firewall log should show which rule is allowing the traffic to pass. Doing this is quite inefficient and time consuming. Was hoping there was another mechanism that would reveal this information.
You'll need to grow a thicker skin if you considered my response an attack.
I was simply responding to your reply which didn't make much sense in the context of what I posted just above it. Sure, I can go back and edit each of the 60+ active rules to enable logging. This type of logging is not enabled by default. Then the firewall log should show which rule is allowing the traffic to pass. Doing this is quite inefficient and time consuming. Was hoping there was another mechanism that would reveal this information.
In response to your comment I offer my whole-hearted apologies. It was never my intention to inflict any emotional or mental suffering on you. As a person of great compassion and empathy, I was gravely concerned with your explanation that you felt victimized by my post, as my intention was only pure, without malice and totally devoid of aggression or intention to degrade, insult or dishonor you as an individual who deserves respect.
Platitudes to you for maintaining communication after feeling attacked. When feeling attacked, one should always express one’s emotional experience to the opposition, thereby conveying the fact that a simple discussion has morphed into a aggressive polemic, and in doing so, the air can be cleared and resolution provided. However, in future communications I shall carry no ill will and nary a negative comment will be written. To put it succinctly, let us proceed with respect and common decency, let me offer my greatest apologies to the offense, and let us join in unity and peace going forward.
Sincerely and with respect,
Jay