Short of enabling logging for all firewall rules, is there some way of seeing which rule allowed or blocked certain traffic? Something in console/command line?
This thread was automatically locked due to age.
My network topology is;
ONT (wan) -- UTM -- Vlans
The ONT is hardcoded to a 192.168.1.254 ip. UTM has an additional address defined for the wan interface (in addition to dhcp).
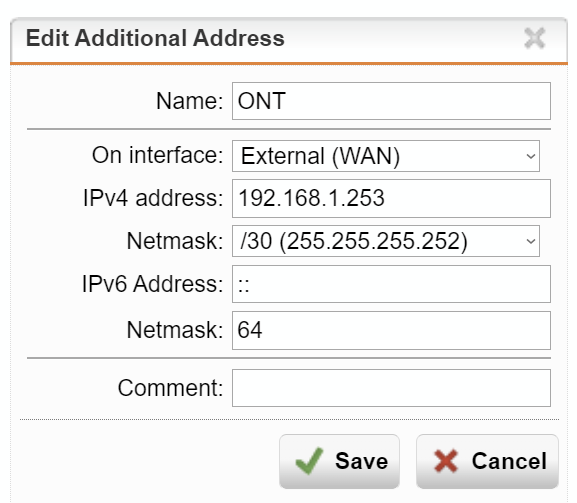
I set this up 3 years ago so I could access the ONT from one of the vlan interfaces. Was trying to remember if I did it as a DNAT rule or just a firewall rule. Turns out it's the latter. BUT, I couldn't find an explicit rule that allowed such access. It wasn't the web proxy either as disabling that still allowed access. There's about 60 active firewall rules in place. One of them is responsible for allowing this traffic.
Could you try a Policy Test (available as the other tab when you View Logs)? It's mainly to test web policies, hence the name, but does give information on firewall rule matches.
Or maybe Diagnostics > Connection List with appropriate filtering? (I just tried this and in my particular use case it unfortunately shows "No Rule" for the Rule ID, so maybe not foolproof.)
Or maybe Diagnostics > Packet Capture? That seems to show Rule ID.
The only Policy Test I see is under the web protection/policy helpdesk. This becomes disabled when webfiltering is turned off. I'm on a home license if that makes a difference. Maybe I'm not looking for it at the right place... What's the exact path?
I don't see diagnostics/connection list either.
Are you in UTM or XG? I'm using UTM.
You'll need to grow a thicker skin if you considered my response an attack.
I was simply responding to your reply which didn't make much sense in the context of what I posted just above it. Sure, I can go back and edit each of the 60+ active rules to enable logging. This type of logging is not enabled by default. Then the firewall log should show which rule is allowing the traffic to pass. Doing this is quite inefficient and time consuming. Was hoping there was another mechanism that would reveal this information.