Greetings everyone,
I've been working hard on a company network problem and need some advice.
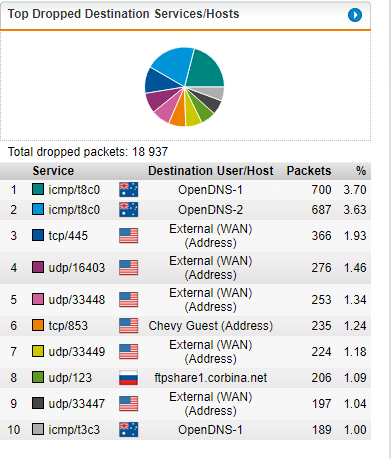
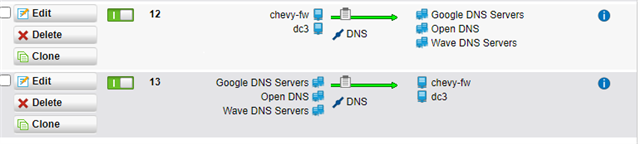
Our clients are experiencing random drops off the Internet. It's like DNS stops resolving websites. When a client experiences this I can ping inside the network, and also the LAN interface of the UTM, but not out to the Internet. Something is randomly blocking them from getting online.
This sometimes affects all users... but mainly randomly one or two at a time.
Any advice would be greatly appreciated.
This thread was automatically locked due to age.