Hello.
Now that everyone is working remotely I've encountered a few issues accessing things outside our network from the SSL VPN. SFTP (SSH on port 22) is the main one of these. It connects fine from inside the office but not via the SSL VPN.
When I run a traceroute to something outside our network on the VPN it uses the UTM as the 1st hop then everything else times out, as if it doesn't have a route out.
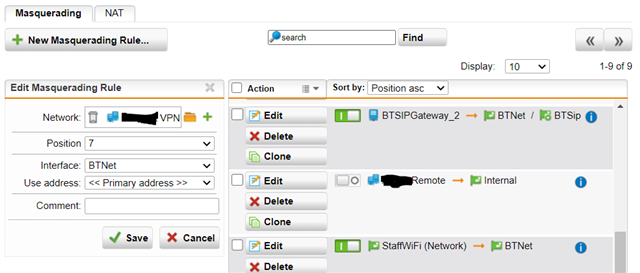
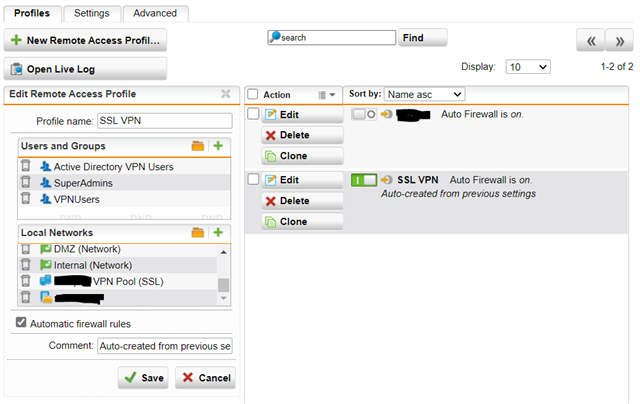
What am I missing? I've looked in the firewall logs but there isn't a single entry for the SSL VPN subnet despite me creating firewall rules and enabling logging. I've also ensured there is a masquerading rule but still no luck.
Any tips appreciated!
This thread was automatically locked due to age.