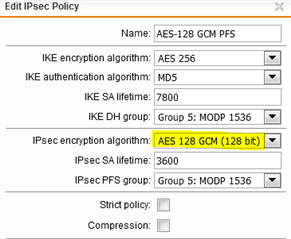
Hi guys , I have implemented an IPsec VPN between an SG230 v2 appliance and a SG115 v3 appliance. RDP and HTTP protocol are a little bit slower, outside the VPN they are much faster
I'm using 3DES policy, do you suggest a policy change?
I also have IPS enabled for Internal Network, all Anti-DoS settings enabled (TCP SYN Flood, UPD Flood, ICMP Flood)
Many thanks!
Ciao, Marco
This thread was automatically locked due to age.