I'm running the current beta firmware and am having problems with the firewall not forwarding LAN to LAN https traffic.
Port 1 LAN 10.0.20.1/24
Remote network - 192.168.99.0/24
Router to remote network 10.0.20.254
I have created a static route and LAN to LAN firewall rule. The firewall rules is a ANY to ANY with ANY service allow rule with malware scanning disabled, and all advanced features such as IPS, Traffic shaping, and web policy configured as None. I also have NAT disabled.
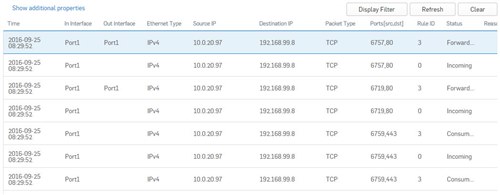
From my computer 10.0.20.97/24 with gateway 10.0.20.1 I am able to successfully connect to the remote web server 192.168.99.8 via ping and view and http web page. The packet capture shows both the incoming traffic on Port 1 and forwarded traffic out on Port 1.
When I attempt to connect via https in either IE, Chrome, or Firefox the page does not appear. The packet capture shows the incoming TCP 443 on Port 1 and the next packet shows as Consumed.
Why is the firewall not forwarding the HTTPS traffic?