Dear Devs,
which is the status of the migration tool?
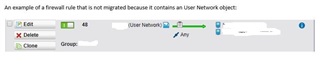
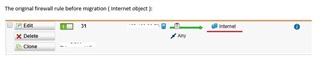
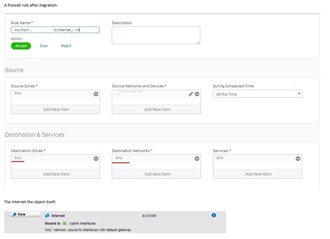
Other vendors are already supporting XG to their brand while in Sophos we cannot even migrate all settings from UTM9 to XG.
I think that v18 is mature enough for most of the UTM 9 users so a tool is needed, guys, to migrate complex installations to XG.
We would like to have an update.
Thanks