Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
- Overview
- 1. How STAS works
- 2. Limitation
- 3. Lab environment
- 4. Configure Sophos Firewall
- 5. Configure Windows AD GPO
- 6. Install and configure STAS
- 7. Verify STAS is working
- 8. Troubleshooting
- a) STA Collector shows no Sophos Firewall IP address
- c) STA Collector shows no live user
- c) Sophos Firewall has no STAS live user, although STA Collector has them
- d) STA Collector keeps removing live user
- e) Sophos Firewall has some STAS live users missing
- f) Group policy of audit logon events is not updated on AD computer
- g) STAS service did not start due to a logon failure
- 9. Known issues
- 10. Appendix
- 11. Edition History
Overview
This Recommended Read describes the best practices for STAS.
Sophos Transparent Authentication Suite (STAS) enables users to automatically log into Sophos Firewall when logging on Windows AD workstation.
STAS requires software installation on AD severs only, and no need to install any software on workstation.
This article provides best practices to configure STAS on Sophos Firewall v18.5 and v19.0.
The configuration example provided in the article is quite simple, but it explains how STAS works.
It covers Windows AD GPO and Windows Firewall rules needed for STAS, and also provides basic troubleshooting guides.
If you notice any errors in the article or improvements can be made, please let me know.
1. How STAS works
STAS is to authenticate users on workstations, not servers.
STAS consists of an agent and a collector.
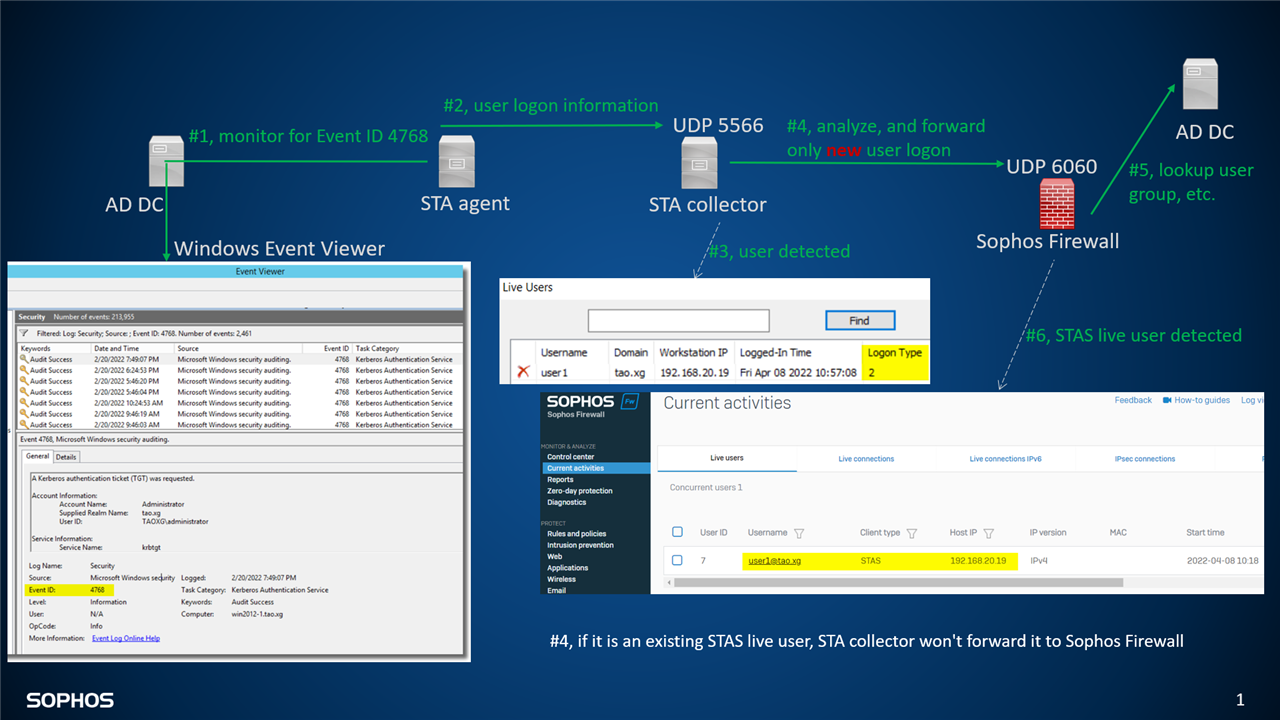
The agent monitors AD domain controller for user logon event, which is Windows Event ID 4768, and sends it to the collector UDP port 5566 (#1, and #2 in diagram logon.type2.png)
The collector analyses the logon event, and sends it to Sophos firewall UDP port 6060, if a user isn’t an existing STAS live user. (#3, and #4 in diagram logon.type2.png)
Sophos Firewall lookups the username in AD domain controller to retrieve group, email address, and more details of the user. (#5 in diagram logon.type2.png)
Then the user will be displayed on Sophos Firewall as STAS live user. (#6 in diagram logon.type2.png)
User detected in such way is known as STAS logon type 2.
Diagram: logon.type2.png
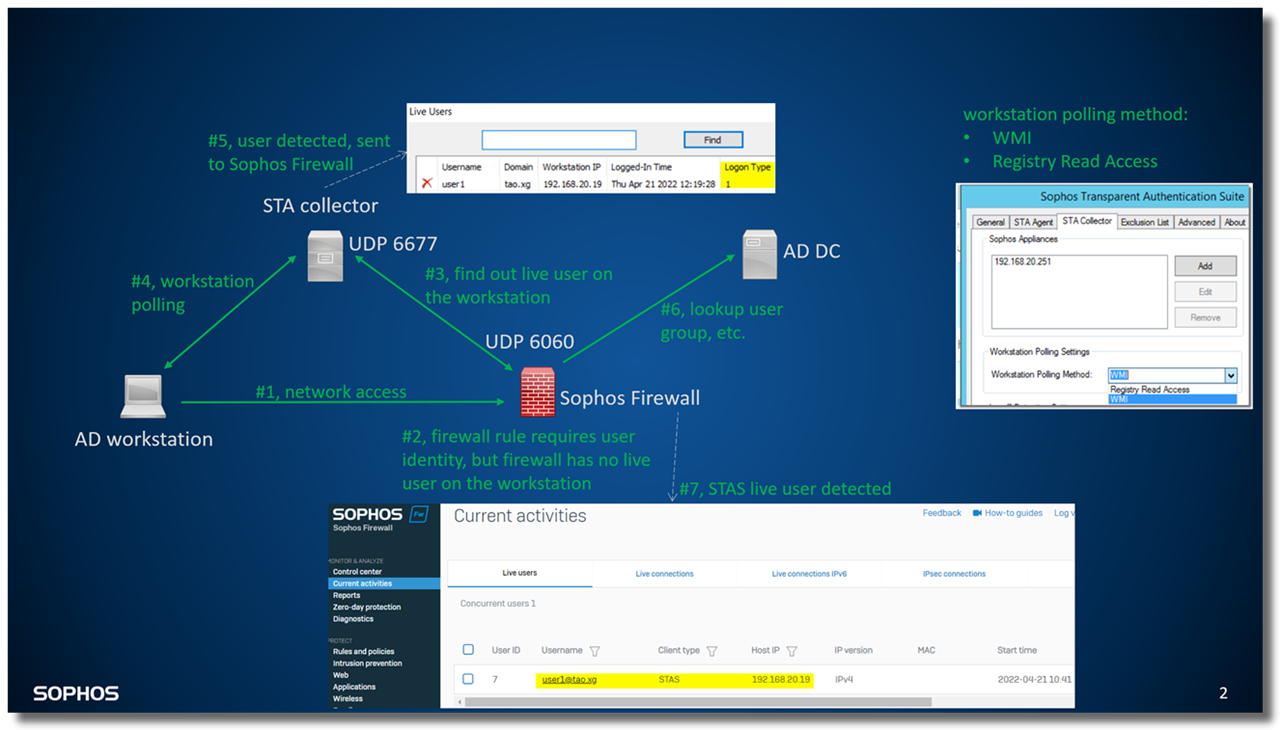
The collector can also help Sophos Firewall to get user logged on an AD workstation.
For example, Sophos Firewall doesn't have live user on an AD workstation, but firewall rule requires user authentication for traffic from the AD workstation. (#1, and #2 in diagram logon.type1.png)
In such situation, Sophos Firewall sends a query to the collector UDP port 6677, asking for username on the workstation. (#3 in diagram logon.type1.png)
The collector talks to the workstation via methods defined in Workstation Polling Method, such as WMI. (#4 in diagram logon.type1.png)
Workstation replies with username in WMI,
then the collector records the live user, (#5 in diagram logon.type1.png) and sends it back to Sophos Firewall on UDP port 6060
Sophos Firewall lookups the username in AD domain controller to retrieve group, email address, and more details of the user. (#6 in diagram logon.type1.png)
Then the user will be displayed on Sophos Firewall as STAS live user. (#7 in diagram logon.type1.png)
User detected in such way is known as STAS logon type 1.
Diagram: logon.type1.png
STA Agent and Collector support to change the default communication ports.
UDP port 6060 on Sophos Firewall for STAS cannot be changed.
a) Deploy STA Agent and STA Collector
- STA Agent can run on AD DC (domain controller), or Windows AD member server.
- STA Collector is not recommended to run on DC, as it generates a high volume of traffic, according to Sophos Firewall Online Help. It is recommended to run on member server.
- STA Agent can serve single or multiple STA Collectors.
- STA Collector can serve single or multiple Sophos Firewalls
[ Note: Member server is a computer that runs an operating system in the Windows Server family, belongs to a domain, and is not a domain controller. ]
b) STA Collector group on Sophos Firewall
- Sophos Firewall can have multiple STA Collectors in a single Collector group, but it communicates only with the primary collector in the Collector group. The primary collector is the one on top of the list.
- If the primary collector doesn't respond, Sophos Firewall will communicate with the 2nd collector.
- STA Collectors for the same AD domain is recommended to be configured in the same Collector group. 2 Collector groups should be enough for an AD domain, when redundancy is needed.
- When there are multiple AD domains, need to create a Collector group for each AD domain.
c) Deployment example
For AD domain with 1 DC, my recommendation is
- install STA Agents on the DC,
- install STA Collector on member server,
- configure STA Agent to serve the Collector,
- configure the Collector to serve Sophos Firewall,
- on Sophos Firewall, put the Collector into a Collector group
For AD domain with 2 DC, my recommendation is:
- install STA Agents on those 2 DC
- install STA Collectors on another 2 member servers
- configure each STA Agent to serve both Collectors
- configure the Collectors to serve Sophos Firewall
- on Sophos Firewall, put those 2 Collectors into same Collector group, since they are in same AD domain
d) Summary of ports
- STA Collector open TCP port 5566 for STA Agent to upload user logon information
- STA Collector open UDP port 6677 for Sophos Firewall to connect
- Sophos Firewall open UDP port 6060 for STA Collectors to connect
- STA Collector sends packet to STA Agent UDP port 50001 for Test connection,
- STA Agent sends packet to STA Collector UDP port 50001 for Test connection,
- STA Collector sends packet to Sophos Sophos Firewall UDP port 6060 for Test connection.
2. Limitation
a) Max number of live users
Sophos Firewall v17.5 and later supports 12,288 live users, by default.
That can be verified as below
- Log on Sophos Firewall SSH terminal as admin. Once authenticated, you will be presented with the Sophos Firewall console menu.
- Go to 5. Device Management > 3. Advanced Shell, and run the following commands
cish
system auth max-live-users show
The limitation can be lifted with the Device Console command with the following command, but make sure your Sophos Firewall is up to sizing.
system auth max-live-users set <8192-32768>
b) Computers must be in AD domain
STAS can only detect users on AD domain workstation.
If a workstation is not a member of the AD domain, STAS won't be able to detect live user on it.
In such a scenario, Sophos Client Authentication Agent is the solution. Details of Client Authentication Agent is available at https://support.sophos.com/support/s/article/KB-000038465
c) NAT is not supported
Traffic between AD workstation, STA Agent/Collector and Sophos Firewall must be routed/switched, not NATed, because original IP address is needed for STAS to work.
d) Windows server core edition is not supported
STAS application requires GUI to work. Windows Server core edition has no GUI enviroment installed by default, so STAS won't work on it.
Kevin Kuphal has provided a workaround:
You can run STAS on a member server and point it at a Windows Core domain controller and it will work just fine.
3. Lab environment
a) Network Topology
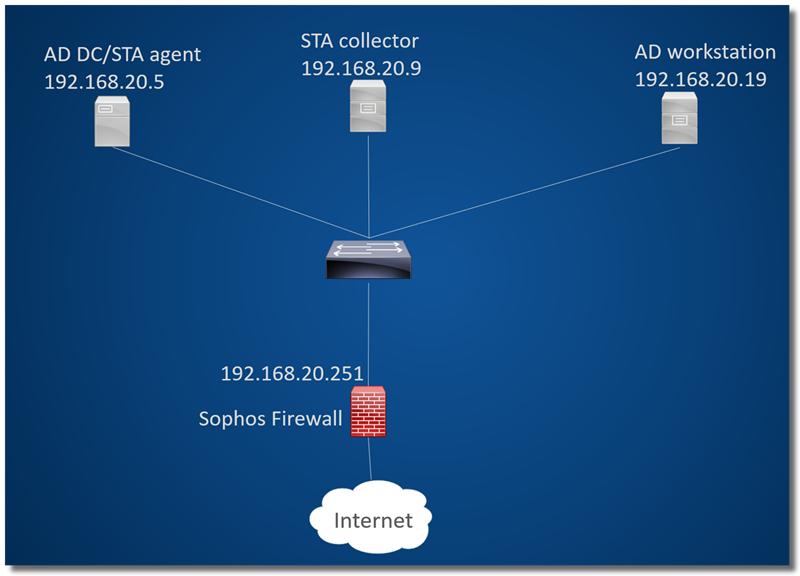
- 192.168.20.5 is AD DC, and STA Agent will be installed on it
- 192.168.20.9 is a member server, and STA Collector will be installed on it.
- 192.168.20.19 is AD workstation
- 192.168.20.251 is Sophos Firewall LAN interface IP
b) Find out the NetBios Name, FQDN, and Search DN
You can find out AD NetBIOS Name, FQDN, and Search DN as described below.
- Log in to your Windows AD DC as a user with Administrative privileges.
- Go to Start > Programs > Administrative Tools > Active Directory Users and Computers.
- Right Click on the required domain and go to the Properties
In this example, FQDN is tao.xg, and NetBIOS name is TAOXG
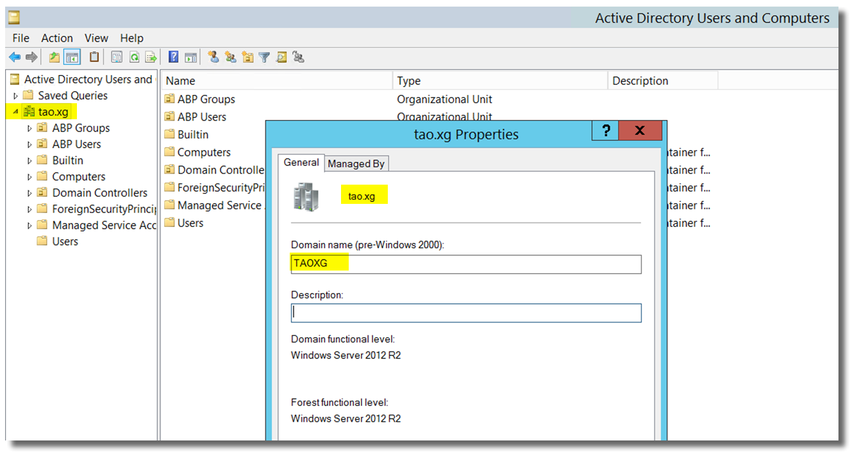
Search DN is required when we configure the authentication server on the Sophos Firewall.
To find out Search DN, run the command dsquery user in Windows CMD, as shown below.
C:\Users\Administrator>dsquery user
"CN=Administrator,CN=Users,DC=tao,DC=xg"
"CN=Guest,CN=Users,DC=tao,DC=xg"
"CN=krbtgt,CN=Users,DC=tao,DC=xg"
"CN=One User,OU=ABP Users,DC=tao,DC=xg"
"CN=Two User,CN=Users,DC=tao,DC=xg"
"CN=AD Admin,CN=Users,DC=tao,DC=xg"
"CN=User Super,CN=Users,DC=tao,DC=xg"
C:\Users\Administrator>
Search DN for "Two User" is "CN=Users,DC=tao,DC=xg"
Search DN for "One User" is "OU=ABP Users,DC=tao,DC=xg"
Later, we’ll configure search DN "DC=tao,DC=xg" in the authentication server on Sophos Firewall.
4. Configure Sophos Firewall
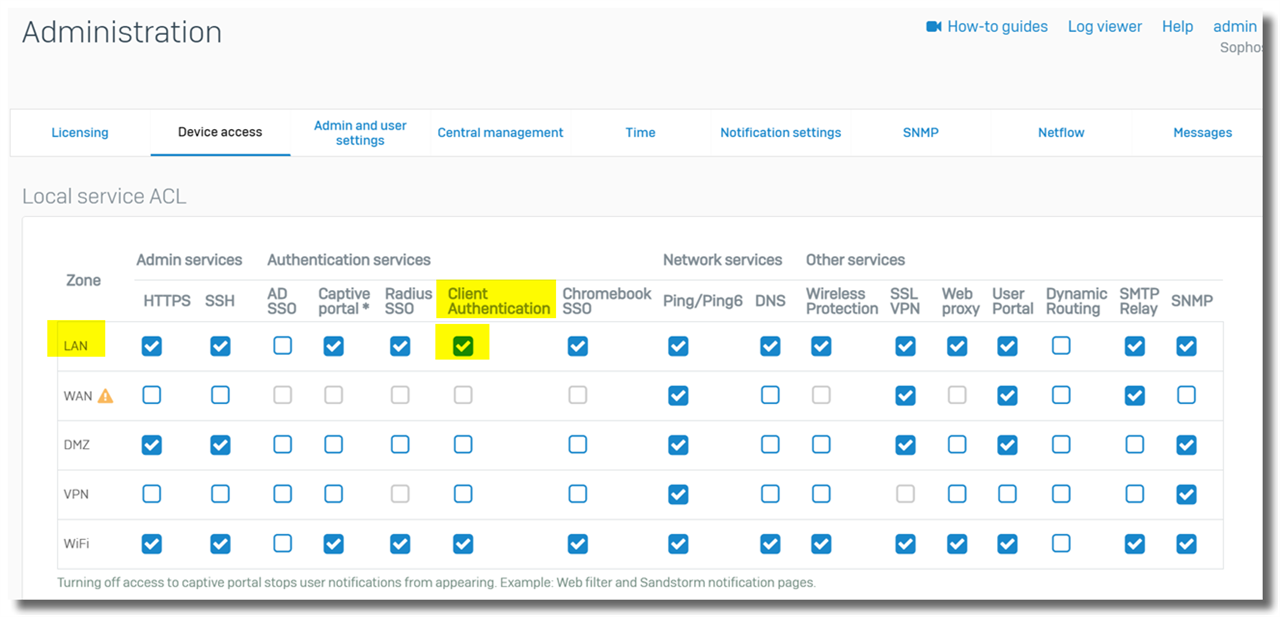
a) Enable Client Authentication in Device Access
Log on to Sophos Firewall webadmin, go to Administration > Device access, enable "Client Authentication" on the zone where STA Collector and user workstation locate. In this example, it’s the LAN zone.
b) Configure authentication server
1) Authentication Server
We need to configure Windows AD DC as an authentication server on Sophos Firewall, so that Sophos Firewall can fetch group and other information of STAS live user from AD DC.
Sophos Firewall Online Help: Configure Active Directory authentication
Log on to the Sophos Firewall webadmin, go to Authentication > Servers, click on the "Add" button.
Configure authentication server as below
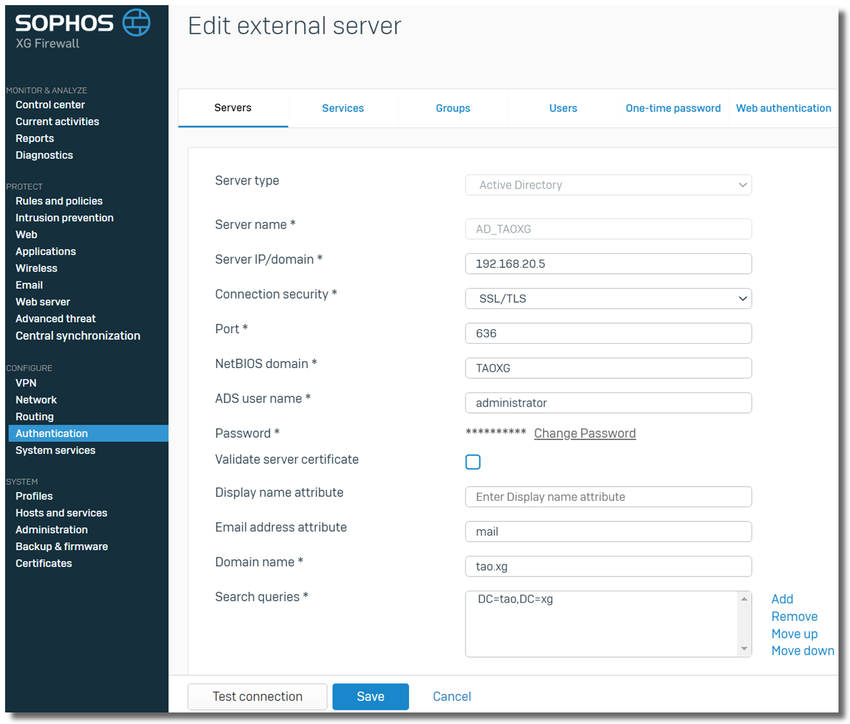
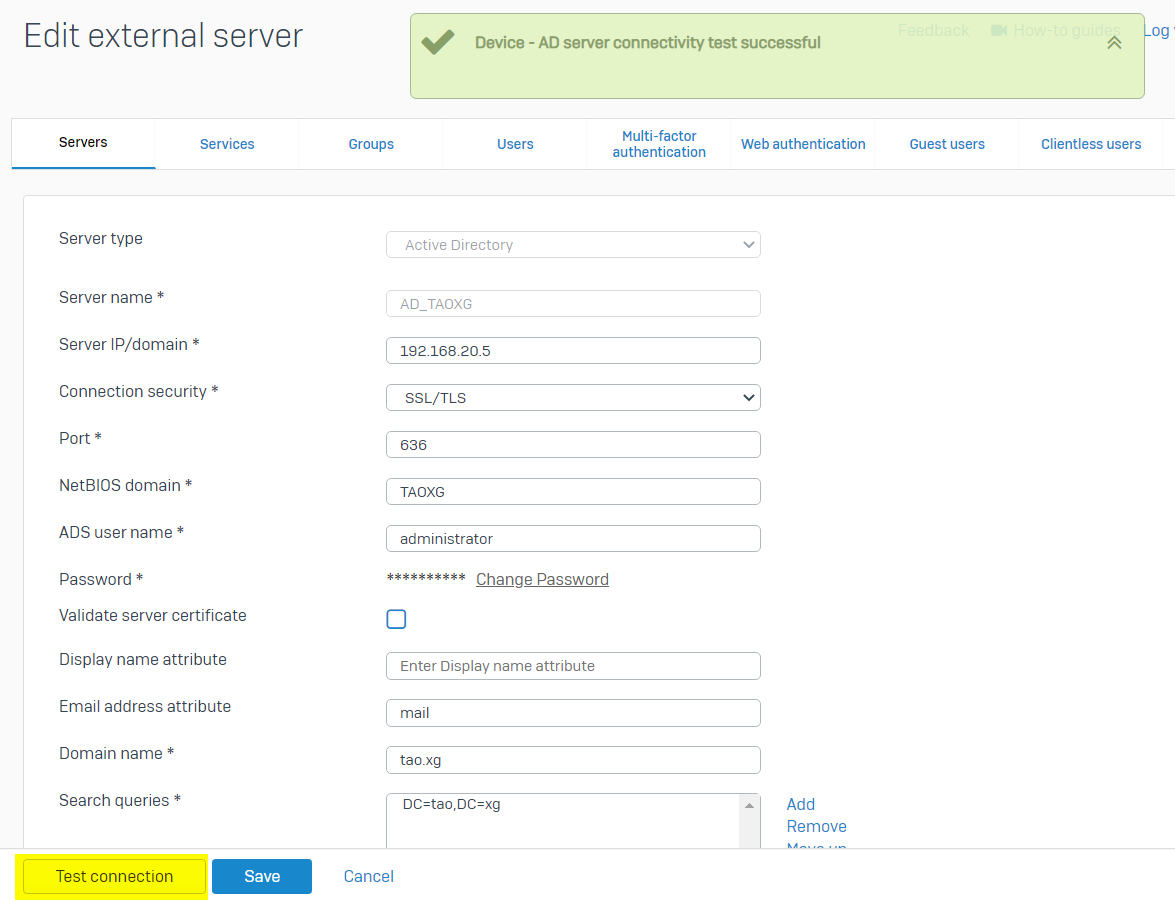
-Server Type: Active Directory
-Server Name: any name for the AD DC
-Server IP: IP address of the AD DC
-Connection security: SSL/TLS, by default
-Port: 636, default TCP port for LDAP service on SSL/TLS
[ Note: To enable SSL on Windows LDAP service, just need to generate a CA on AD DC, reboot DC, DC would automatically assign the CA to LDAP service, and accept LDAP traffic on TCP port 636. Details in the section "10. Appendix > a) Enable SSL on Windows LDAP service ]
-NetBIOS Domain: TAOXG, as discovered above
-ADS username: an AD user with AD administrator privilege
-Password: password of ADS username
-Display Name Attribute: leave it blank. If you need to use another AD attribute for Name, please refer to Microsoft KBA docs.microsoft.com/.../attributes-all
-Email Address Attribute: mail, by default. If you need to use other AD attribute for Email, please refer to Microsoft KBA docs.microsoft.com/.../attributes-all
-Domain Name: tao.xg, as discovered above.
-Search Queries: "DC=tao,DC=xg" as discovered above.
Once the configuration is completed, click "Test connection" to make sure the Sophos Firewall can communicate with AD DC via LDAP.
2) Import AD user group
This step is optional, however, it’s recommended to import AD user groups, to simplify user management on the Sophos Firewall.
To apply firewall rule on specific AD user groups, those AD user groups need to be imported into the Sophos Firewall.
Go to Authentication > Server, click the "Import" icon next to an AD server, as shown below
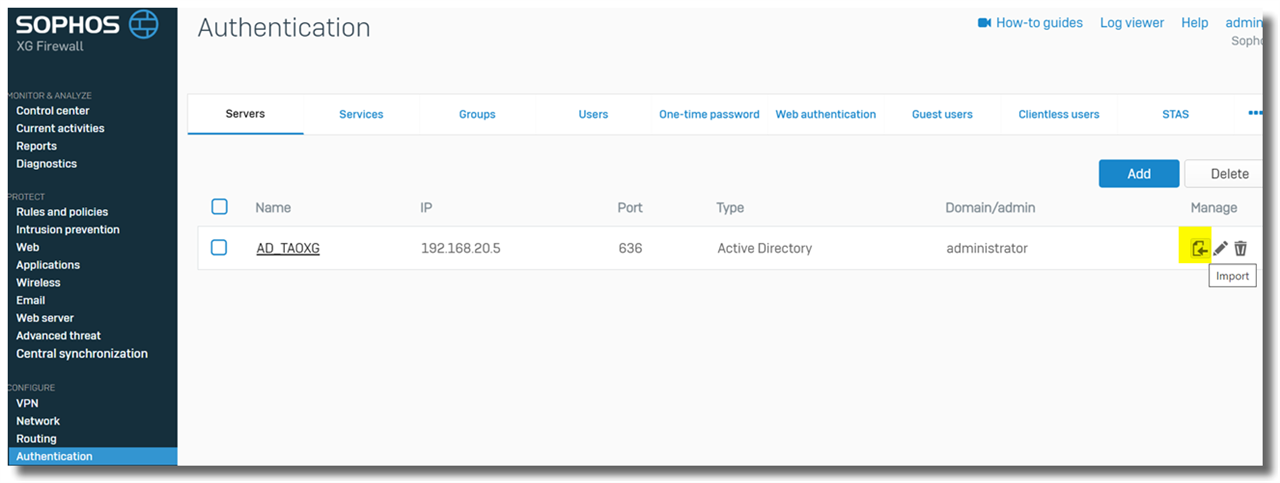
Set Base DN to "DC=tao,DC=xg"
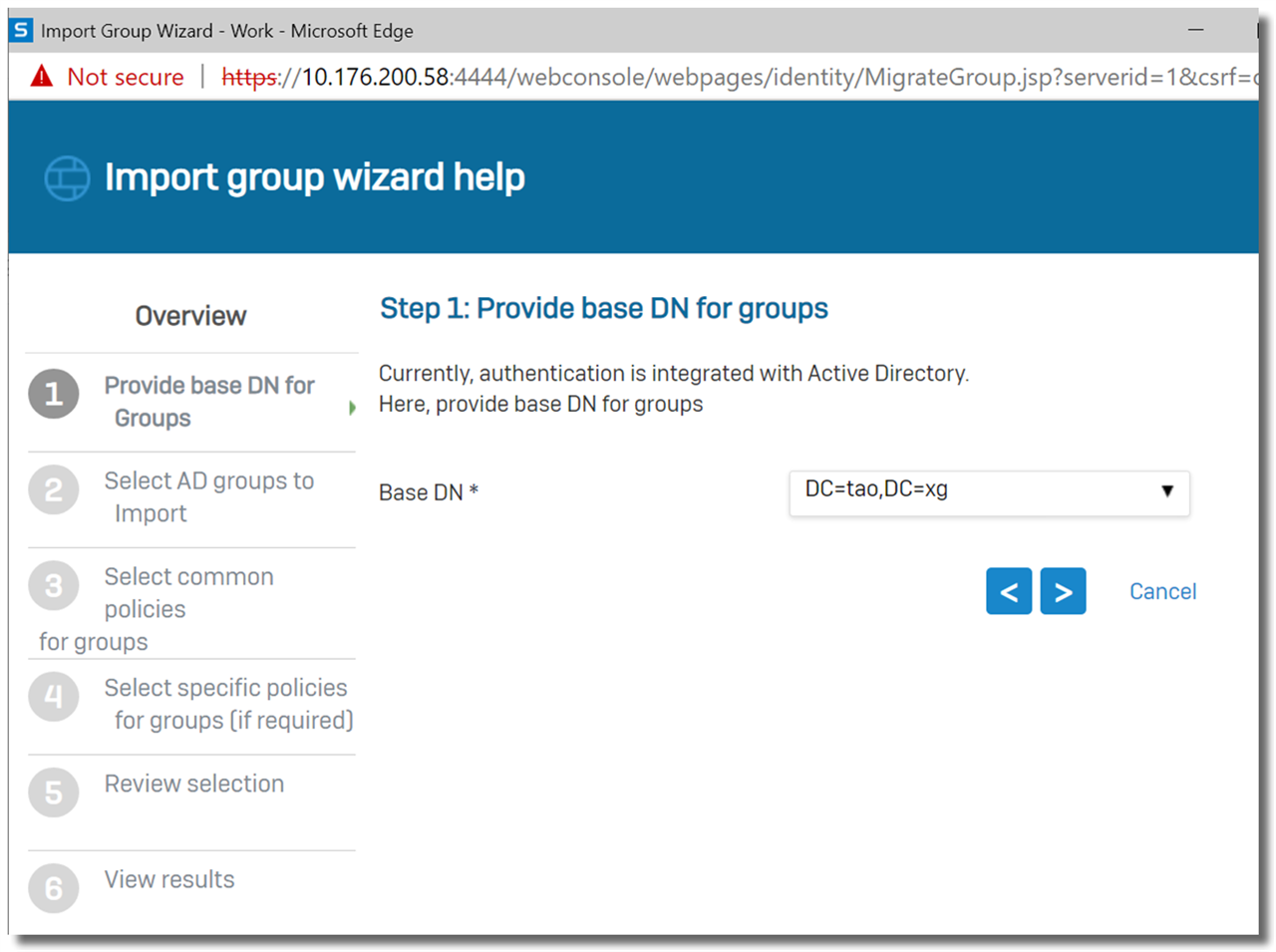
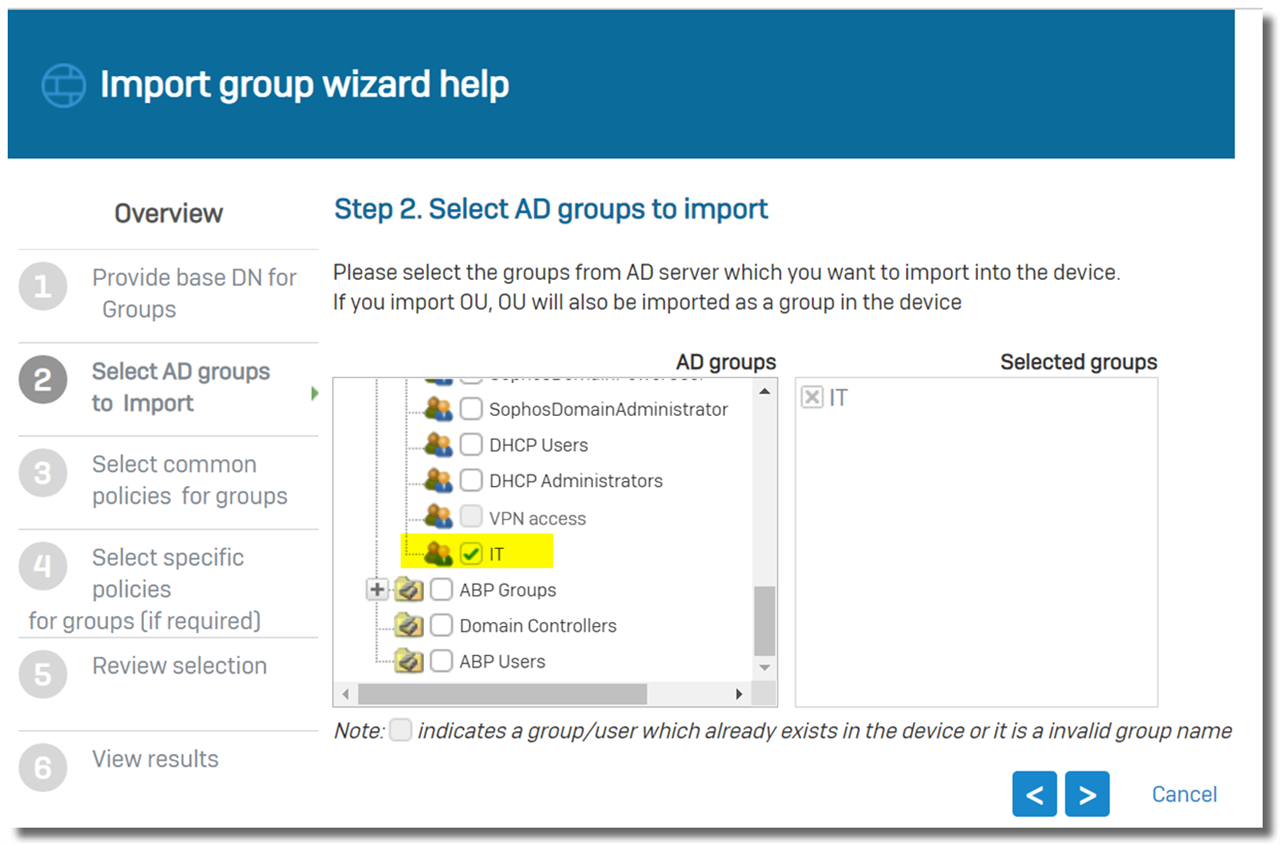
Check the desired groups
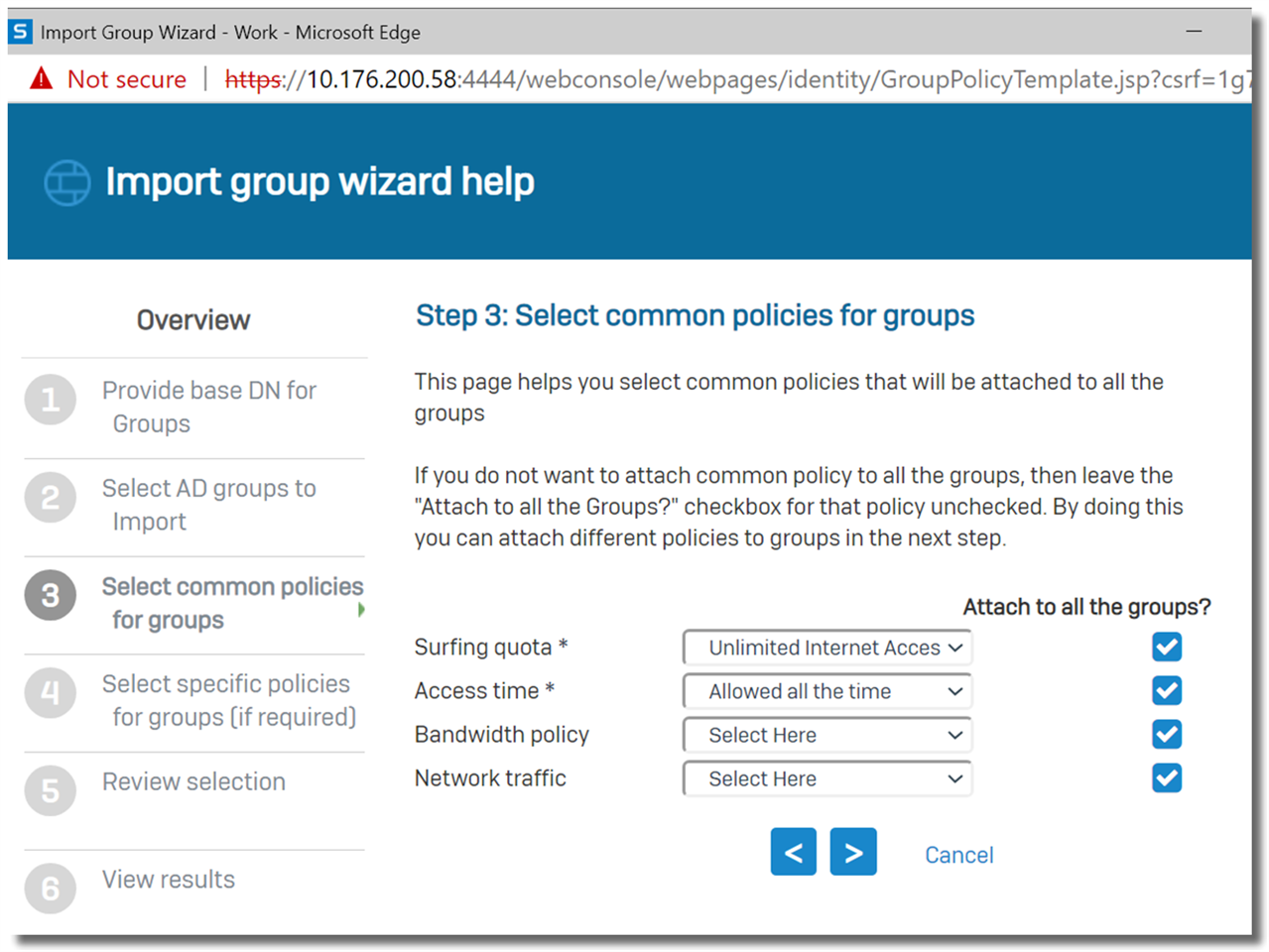
Set common policies for those Groups. Normally we leave it as default during the initial setup.
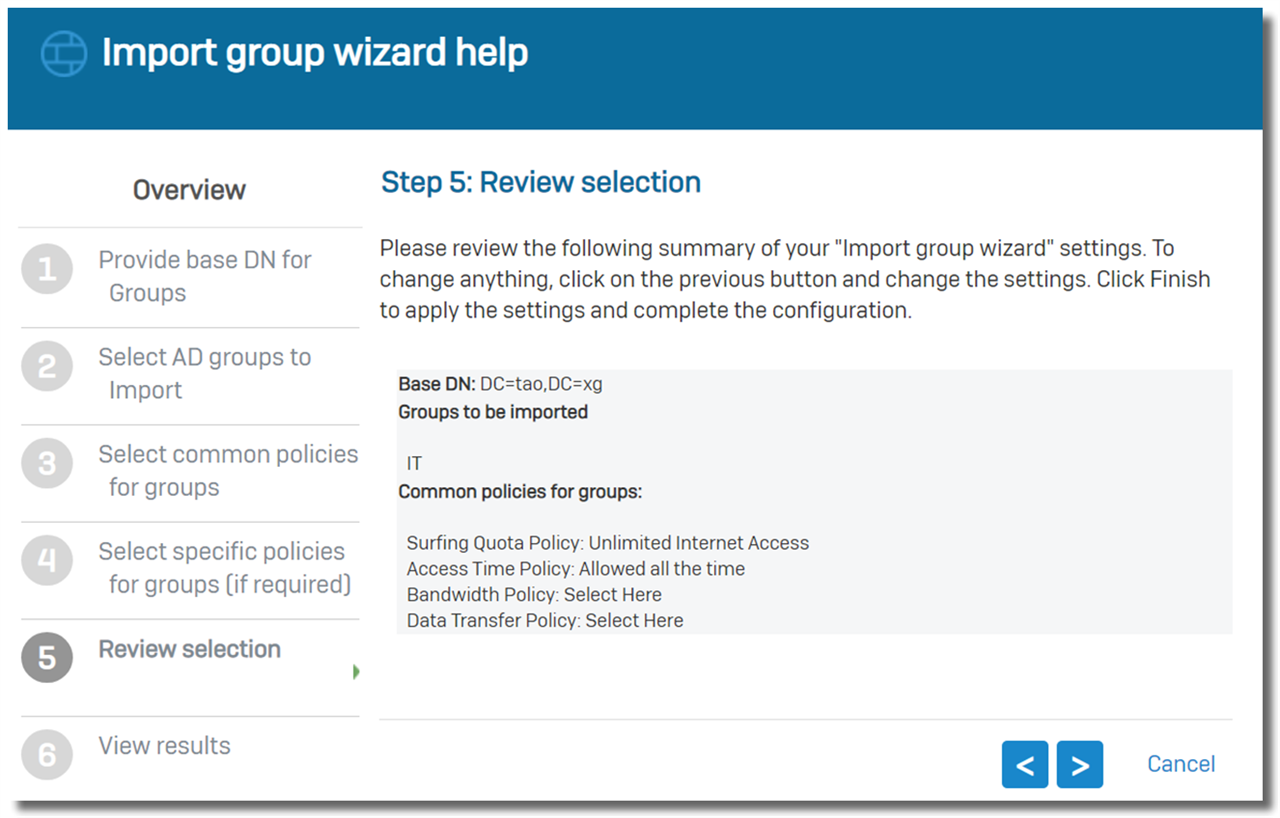
Click on Next to import the group.
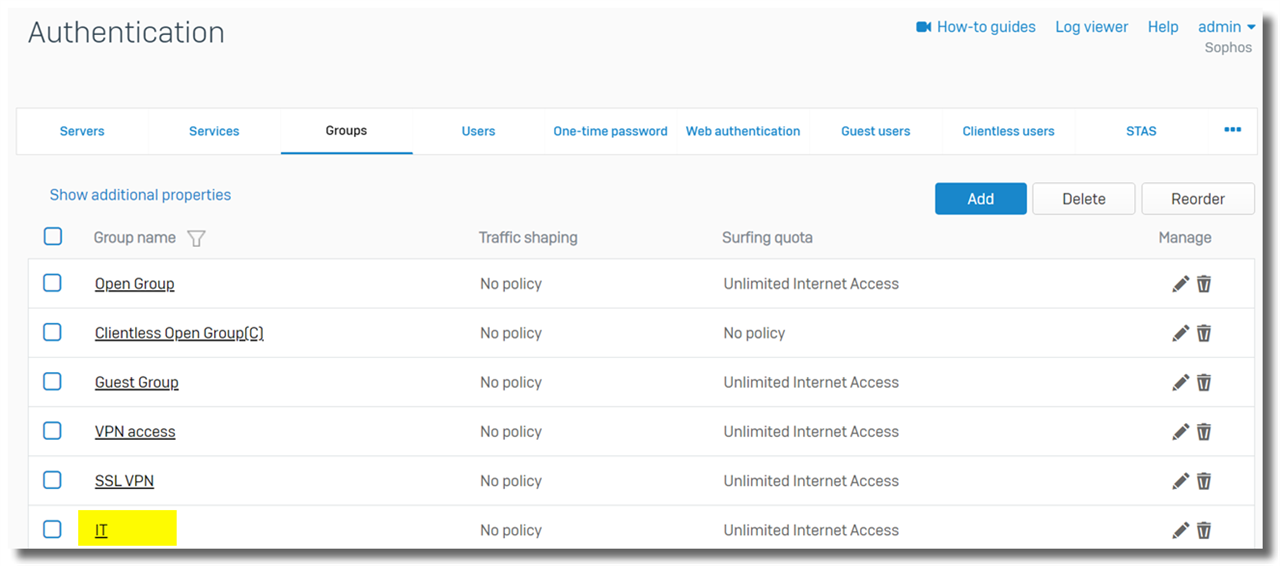
Go to Authentication > Groups, verify the AD group has been imported, as shown below
3) Authentication Service
Go to the Sophos Firewall webadmin > Authentication > Services, choose the Windows AD DC as the first server for "Firewall Authentication Methods", as shown below.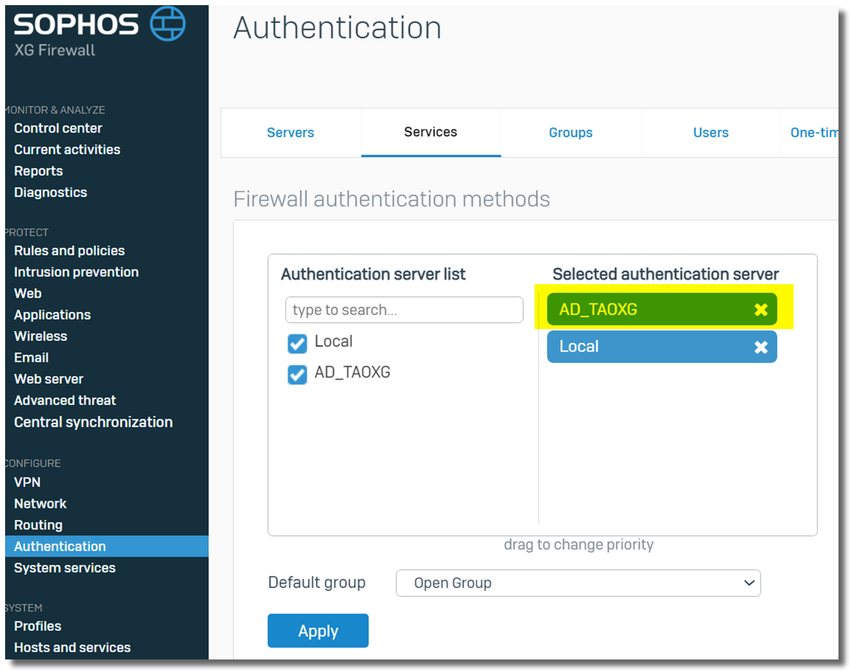
c) Enable STAS
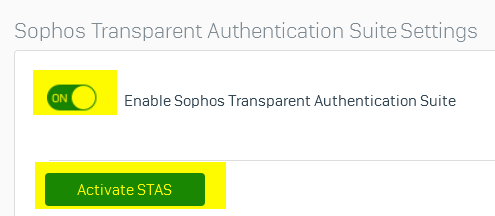
Go to Sophos Firewall webadmin > Authentication > STAS, turn on "Enable Sophos Transparent Authentication Suite", and then click "Activate STAS" button, as shown below
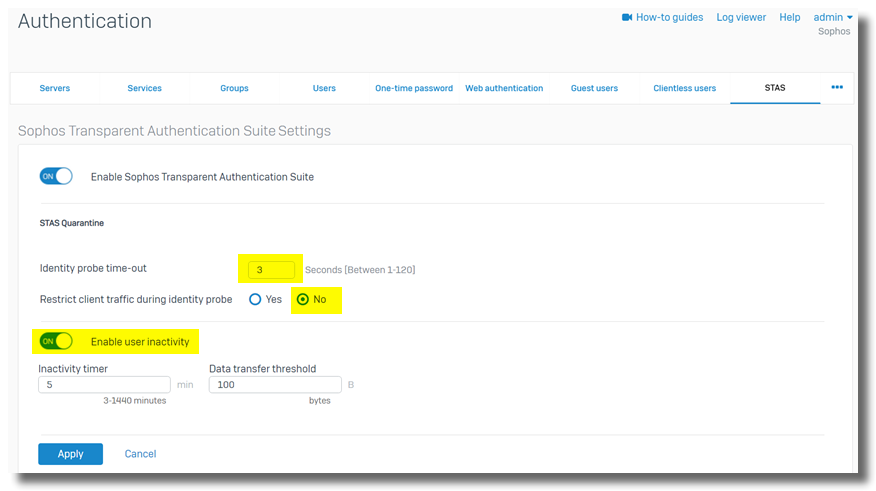
Change default settings,
- Identity probe time-out: 3 seconds
- Restrict client traffic during identity probe: No
- Enable user inactivity: enabled
Note:
- With the default settings of "Identity probe time-out": 120 seconds, and "Restrict client traffic during identity probe": Yes, AD workstation experiences 2-minute network outage every hour once STAS is enabled on Sophos Firewall.
- Details about "Restrict client traffic during identity probe" can be found in section "Drop timeout in Learning Mode" of Sophos KBA https://support.sophos.com/support/s/article/KB-000035730
Next step is to add STAS server.
Click the "Add new collector button", and add the IP address of the STAS server. In this example, it is 192.168.20.9
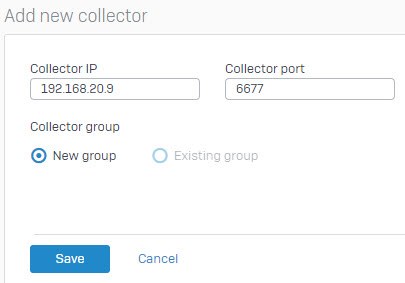
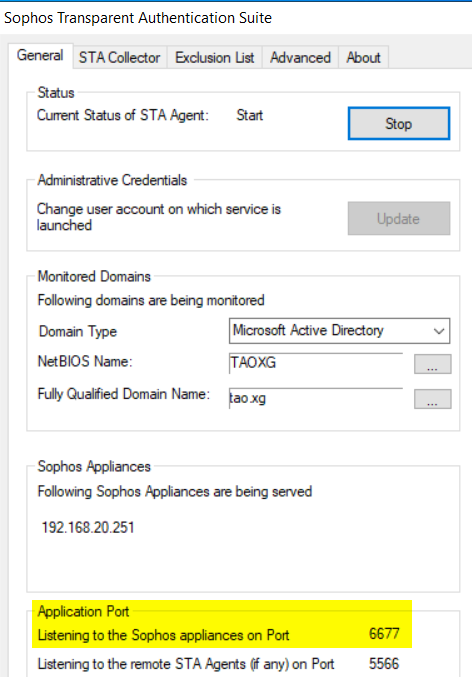
Collector Port can be checked on STAS Suite> General tab > Listening to the Sophos appliance on Port, as shown below
5. Configure Windows AD GPO
a) Enable audit logon events on AD computers
- Log on to Windows AD DC as a member of the Administrators group.
- Open Administrative Tools, and then click Group Policy Management.
- In the console tree, open Forest: YOUR_FOREST > Domains > YOUR_DOMAIN_NAME, right-click on Default Domain Policy, and then click Edit.
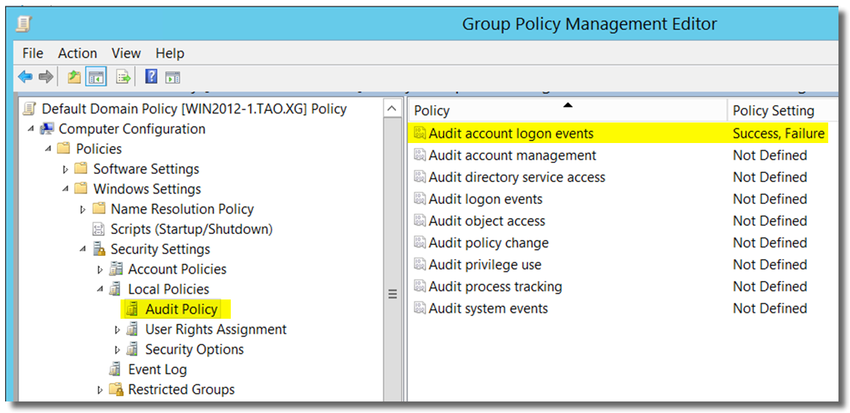
[ Note: You can also edit other group policy as needed. ] - In Group Policy Management Editor, open Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policies.
- Double-click on Audit account logon events, and enable "Define these policy settings: Success and Failure"
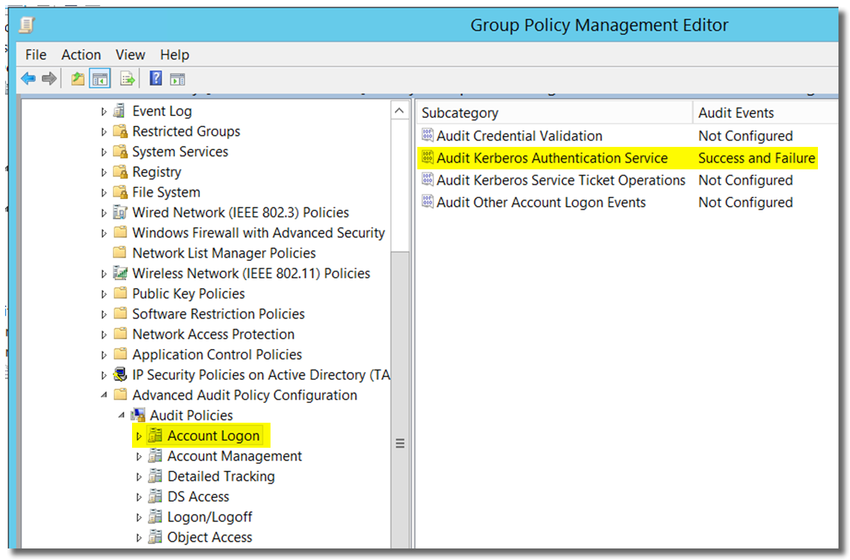
- Open Computer Configuration > Policies > Windows Settings > Security Settings > Advanced audit policy configuration > Audit Policies > Account Logon
- Double-click on Audit Kerberos Authentication Service, and enable "Configure the following audit events: Success and Failure"
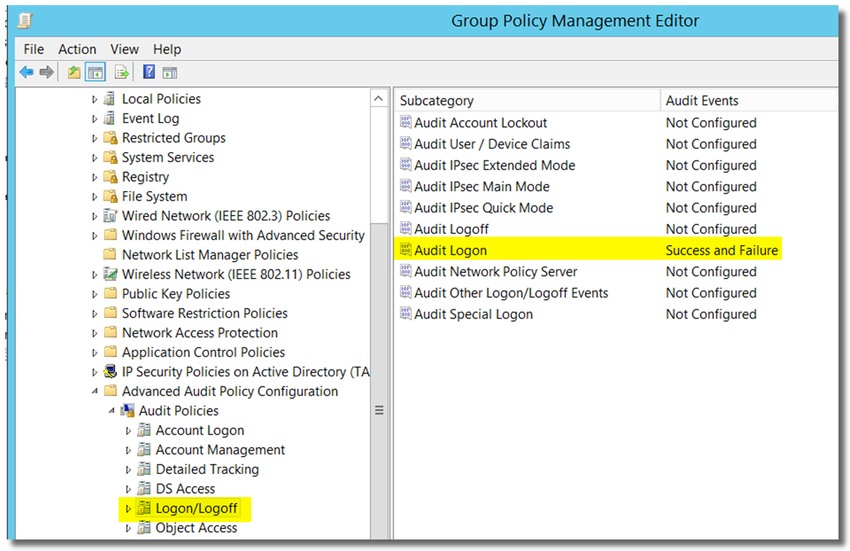
- open Computer Configuration > Policies > Windows Settings > Security Settings > Advanced audit policy configuration > Audit Policies > Logon/Logoff
- Double-click on Audit Logon, and enable "Configure the following audit events: Success and Failure."
b) Allow inbound WMI on AD computers
Make sure Firewall rule on AD workstation allows incoming WMI.
- Log on to Windows AD DC as a member of the Administrators
- Open Administrative Tools, and then click Group Policy Management.
- In the console tree, open Forest: YOUR_FOREST > Domains > YOUR_DOMAIN_NAME, right-click on Default Domain Policy, and then click Edit.
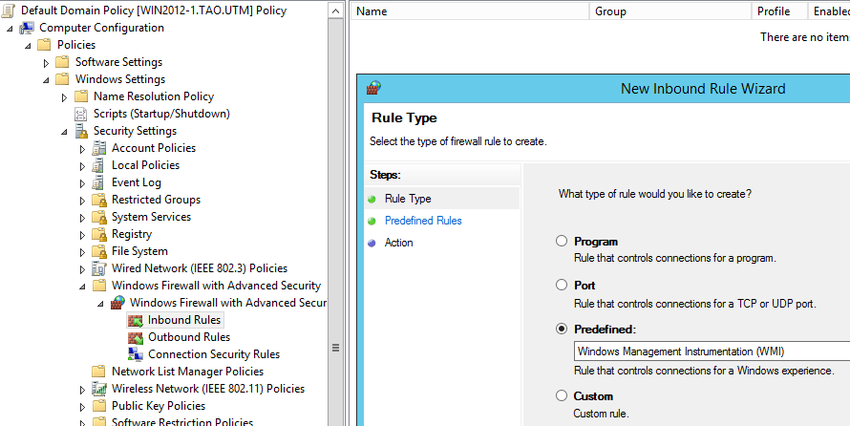
[ Note: You can also edit other group policy as needed. ] - In Group Policy Management Editor, open Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security > Windows Firewall with Advanced Security, right-click on Inbound Rules > New Rules
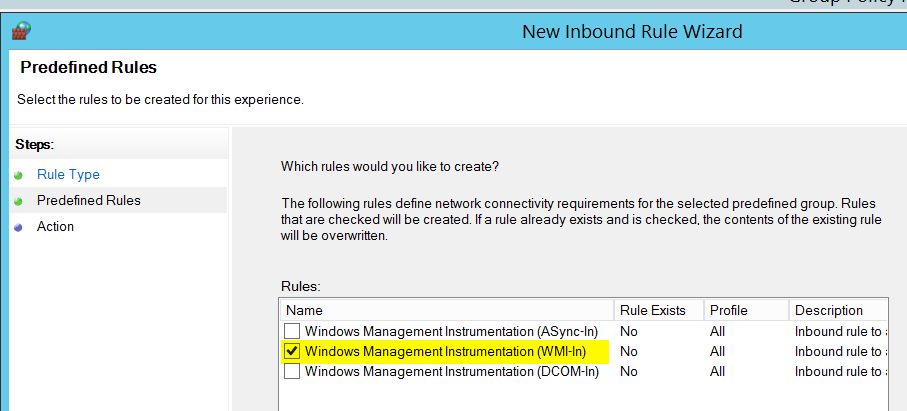
- set Rule Type to "Predefined: Windows Management Instrumentation (WMI)"
Check WMI-In
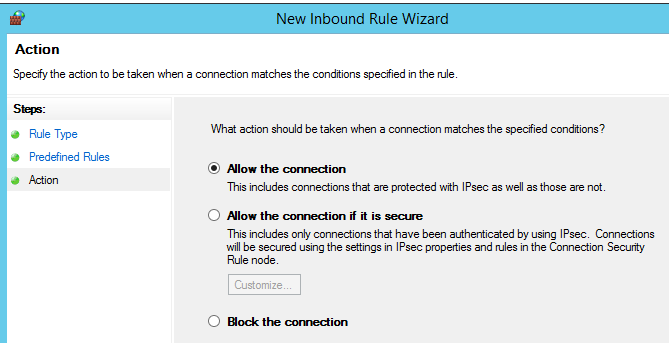
Action: Allow the connection
c) Update Group Policy settings
- On an AD computer, click Start, point to All Programs, click Accessories, right-click on Command Prompt, and then click "Run as administrator".
- If the User Account Control dialog box appears, click Yes to continue.
- Type
gpupdate /force
and then press ENTER.
Once group policy is updated, you can continue to the next step to verify audit policy settings were applied correctly.
You can also wait for the group policy to be updated as per the Windows schedule.
d) Verify audit logon events were applied correctly
- On AD computer, click Start, point to All Programs, click Accessories, right-click Command Prompt, and then click Run as administrator.
- If the User Account Control dialog box appears, click Yes to continue.
- Run the following 2 commands.
auditpol.exe /get /category:"Logon/Logoff"
auditpol.exe /get /category:"Account Logon" - Make sure Success and Failure is enabled for "Logon" and "Kerberos Authentication Service", as below
C:\WINDOWS\system32>auditpol.exe /get /category:"Logon/Logoff"
System audit policy
Category/Subcategory Setting
Logon/Logoff
Logon Success and Failure
Logoff No Auditing
Account Lockout No Auditing
IPsec Main Mode No Auditing
IPsec Quick Mode No Auditing
IPsec Extended Mode No Auditing
Special Logon No Auditing
Other Logon/Logoff Events No Auditing
Network Policy Server No Auditing
User / Device Claims No Auditing
Group Membership No Auditing
C:\WINDOWS\system32>auditpol.exe /get /category:"Account Logon"
System audit policy
Category/Subcategory Setting
Account Logon
Kerberos Service Ticket Operations No Auditing
Other Account Logon Events No Auditing
Kerberos Authentication Service Success and Failure
Credential Validation No Auditing
C:\WINDOWS\system32>
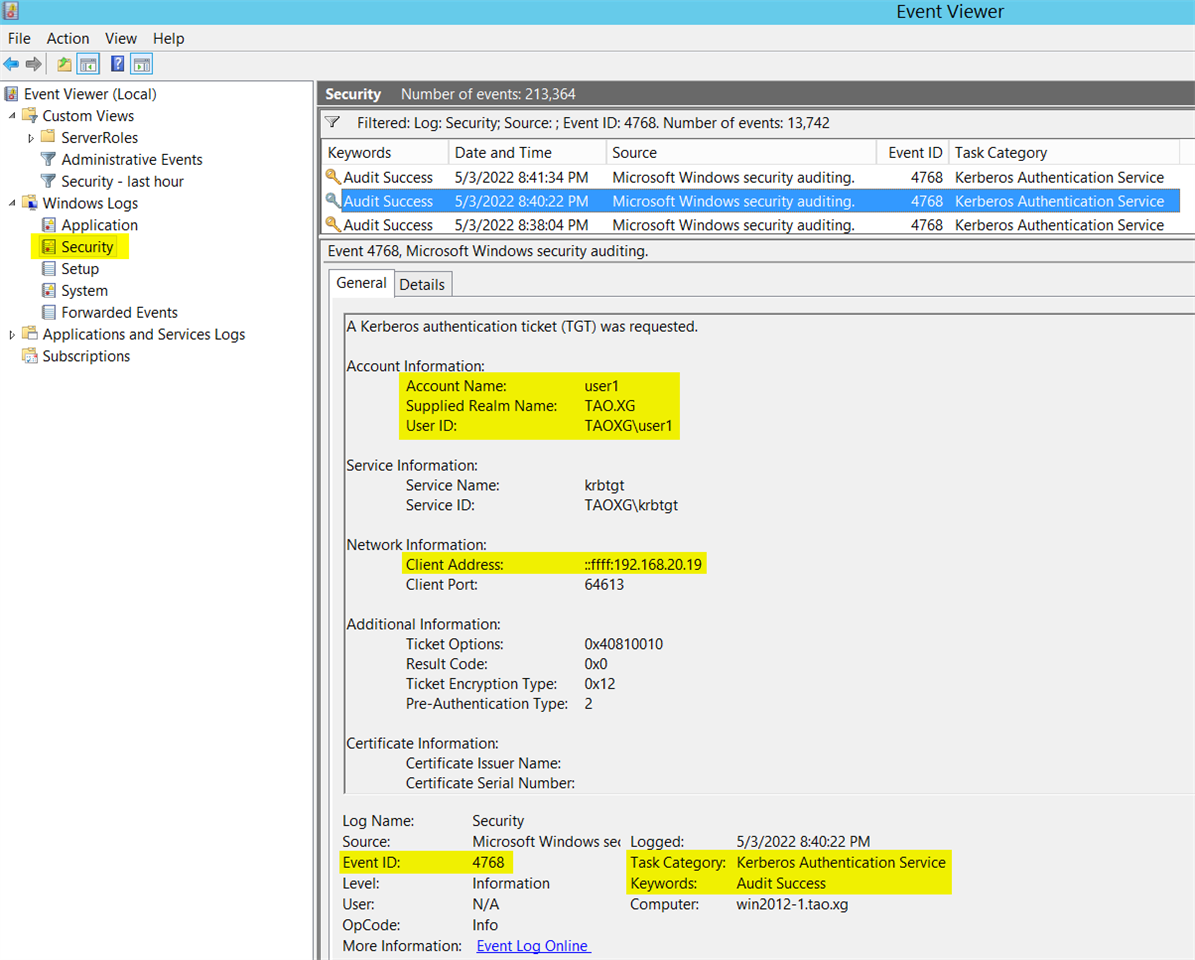
e) Verify event ID 4768 was generated for user logon
Event ID 4768 is for user logon.
If AD DC doesn't generate event ID 4768 in Windows Event Viewer, the STA Agent cannot detect any user logon activity.
Once event ID 4768 is generated, STA Agent forwards that information to the STA Collector UDP port 5566.
Please check Windows Event Viewer to make sure Event ID 4768 is generated when a user logs on a workstation.
The following screenshot shows user1 logged on AD domain tao.xg from workstation 192.168.20.19.
6. Install and configure STAS
a) Install STAS
Sophos KBA for STAS https://support.sophos.com/support/s/article/KB-000035732
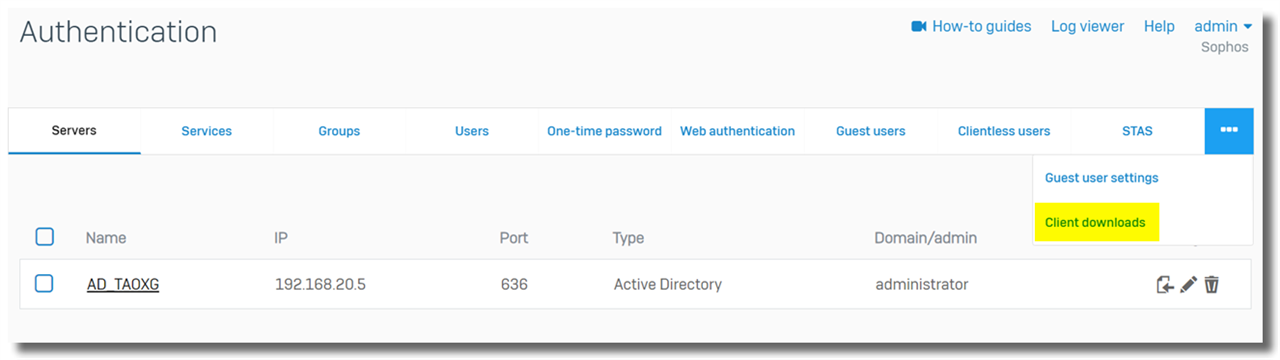
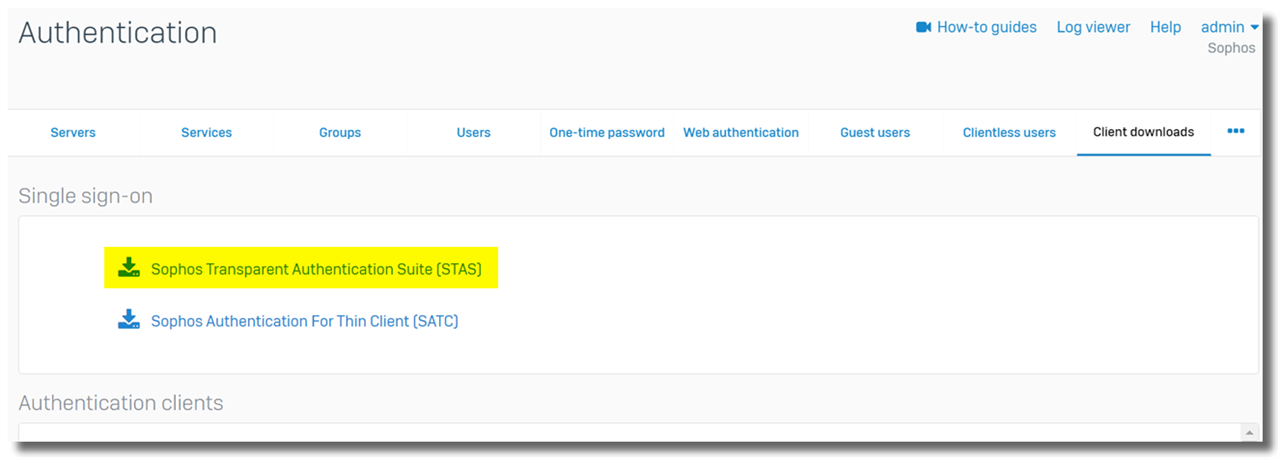
Latest STAS can be downloaded from Sophos Firewall webadmin > Authentication > Client downloads, as below
In this example, STA Agent was installed on a Windows AD DC 192.168.20.5. STA Collector was installed on a member server 192.168.20.9.
Please install STAS by right click on installation file > 'Run as administrator' to prevent any potential permission issue on Windows.
For STA Agent, choose "STA Agent"
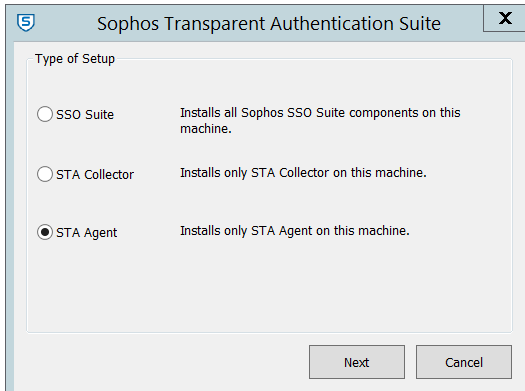
For STA Collector, choose "STA Collector"
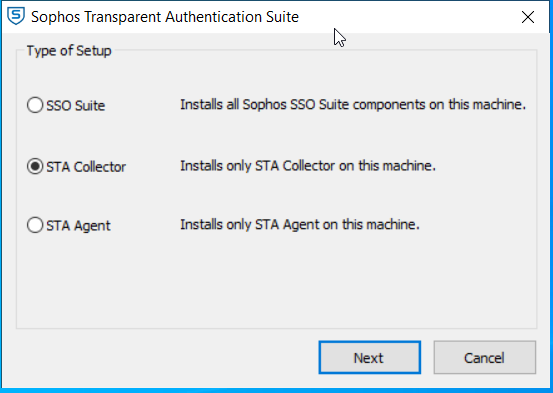
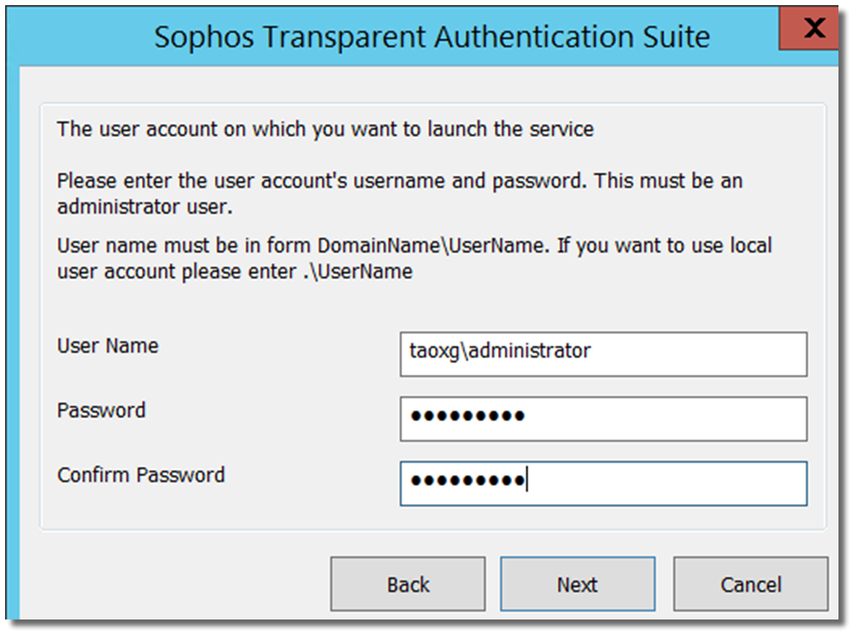
Enter Windows AD administrator credentials, as shown below. The account is needed to
- query Windows Event Viewer on AD DC for Event ID 4768,
- start/stop "Sophos Transparent Authentication Suite" service, and
- send Windows WMI query to AD workstation to perform workstation polling
It is not necessary to be administrator, but it must be a member of group Domain Admins.
b) Configure STA Agent
Open STAS on domain controller 192.168.20.5.
1) In "General" tab, put in NETBIOS name of AD domain, together with Fully Qualified Domain Name
And then click on Start button to start agent
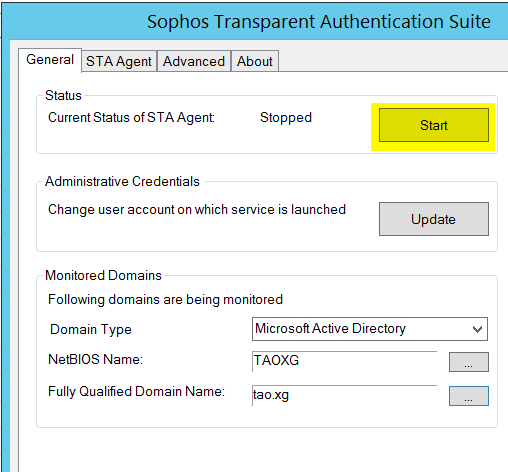
2) Wait for Current Status of STA Agent to be "Start"
If STA agent cannot be started, please double check Administrator Credentials, NetBIOS Name, and Fully Qualified Domain Name.
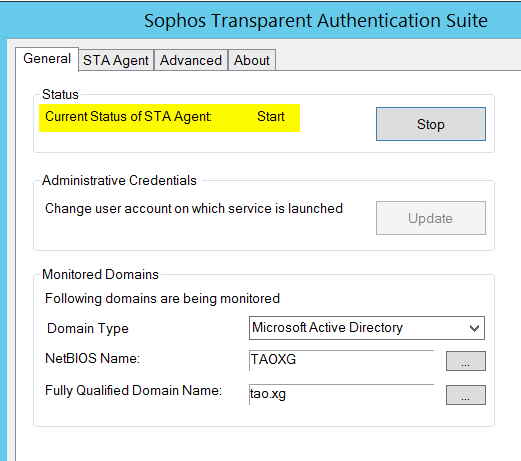
3) Go to "STA Agent" tab, and specify the subnet where all Windows AD users belong to, as shown below.
"STA Agent Mode": EVENTLOG is recommended.
"Domain Controller IP": It is only needed when STA Agent is installed on a member server. It must be blank if STA Agent is installed on an AD DC. Otherwise, STA Agent can't read local Windows Event logs.
“Monitor Networks”: 192.168.20.0/24 for the example
"Collector List": In the example , it is 192.168.20.9
"Domain Controller Polling" is available for configuration if STA Agent Mode is set to NETAPI. In the example, I set STA Agent Mode to be EVENTLOG, therefore, no need to configure the option.
Remember to click on "OK" to save configuration on STA agent.
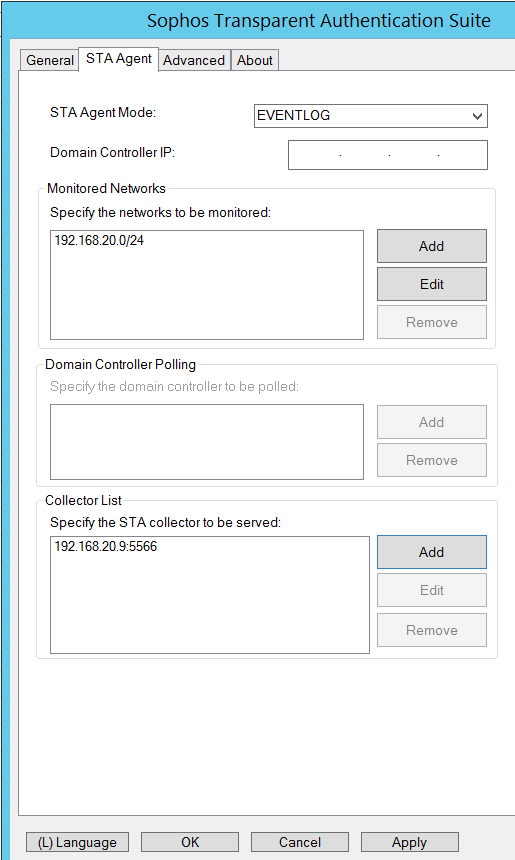
c) Configure STA Collector
Open STAS on member server 192.168.20.9.
In "General" tab, put in NetBIOS Name and Fully Qualified Domain Name of AD domain.
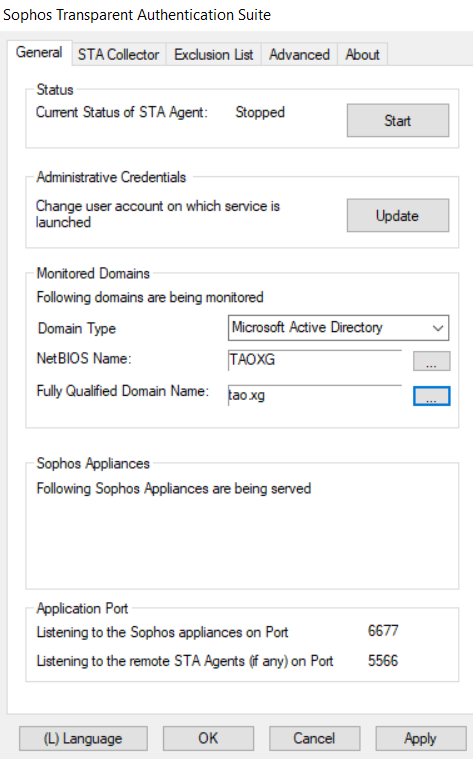
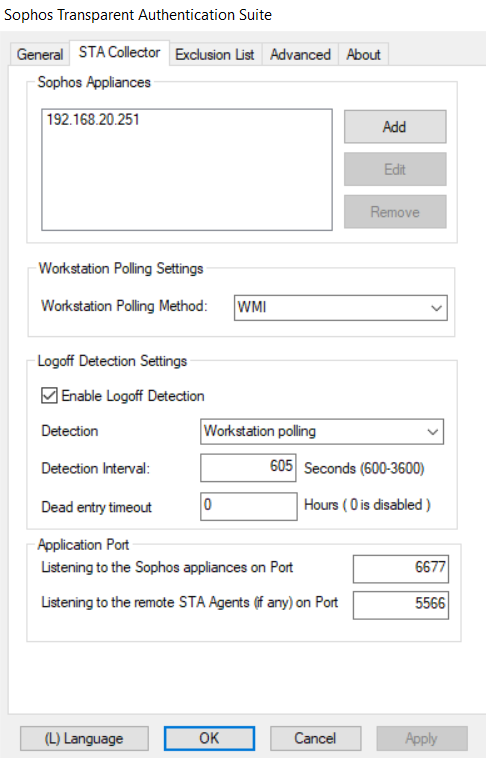
Go to "STA Collector" tab,
- "Sophos Appliances": the internal IP address of the Sophos Firewall, 192.168.20.251. If Sophos Firewall is in HA, please use interface IP address, not HA peer administration IP.
- "Workstation Polling Method": WMI is recommended
- "Enable Logoff Detection": checked
- "Detection Method": Workstation polling
- "Dead entry timeout": must be 0. Details in section "9. Known issues".
d) Configure Exclusion List
Go to "Exclusion List",
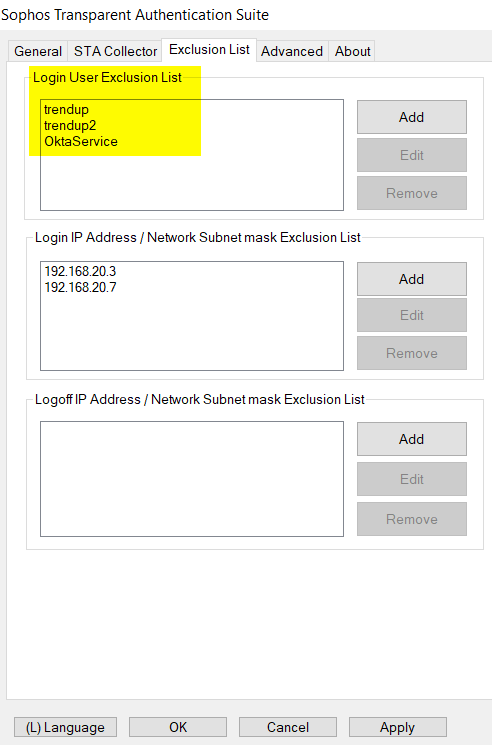
1) In "Login User Exclusion List": we put in any background service accounts, for example trendupd, trendupd2, OktaService, and more, depending on software installed on workstation.
That prevents STAS live user to be logged off when a background service account logs in to start background tasks.
Note:
- "Login User Exclusion List" only supports "username", and doesn't support "username@domain.com", nor "domain\username".
- Username in "Login User Exclusion List" is case insensitive.
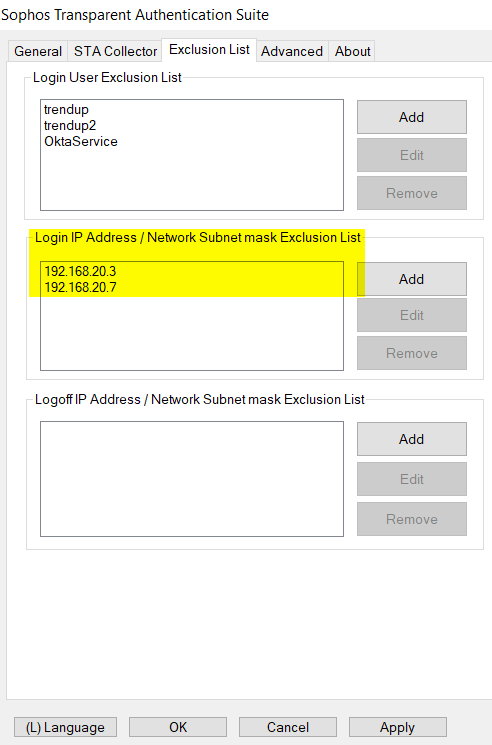
2) In "Login IP Address/Network Exclusion List", add IP addresses of any server, for example Citrix terminal server, Microsoft RDS server, DNS server, web server, to prevent frequent user logon/logoff.
The reason is STAS is to authentication users on workstation, not servers.
In the example, I put IP address of DNS server and web server into Login IP Address Exclusion List.
e) Advanced
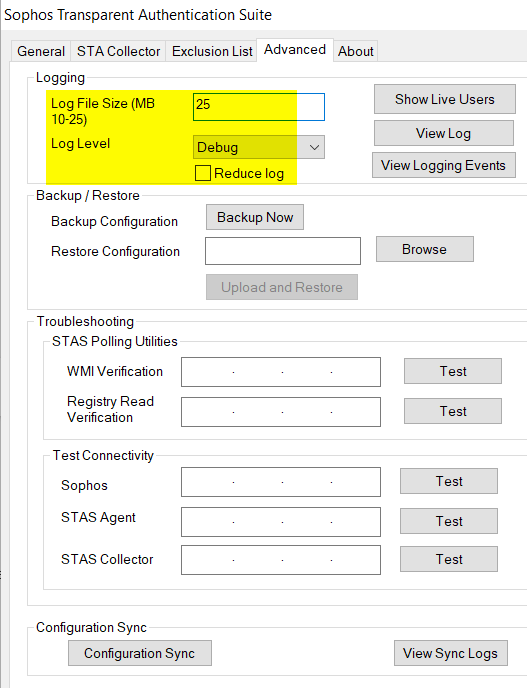
The following is recommended, in case STAS troubleshooting is needed.
- STAS log file size: 25
- Log level: Debug
- Reduce log: disable
STAS log files, stas.log, and stas.log1, are located on the Windows server installed with STAS in the directory of C:\Program Files (x86)\Sophos\Sophos Transparent Authentication Suite, by default.
stas.log and stas.log1 get rotated at every 25 MB (or as defined by Log File Size).
Remember to click on "OK" to save configuration.
f) Start STA Collector
We have completed configuration of STA Collector.
Click "Start" to start STAS service.
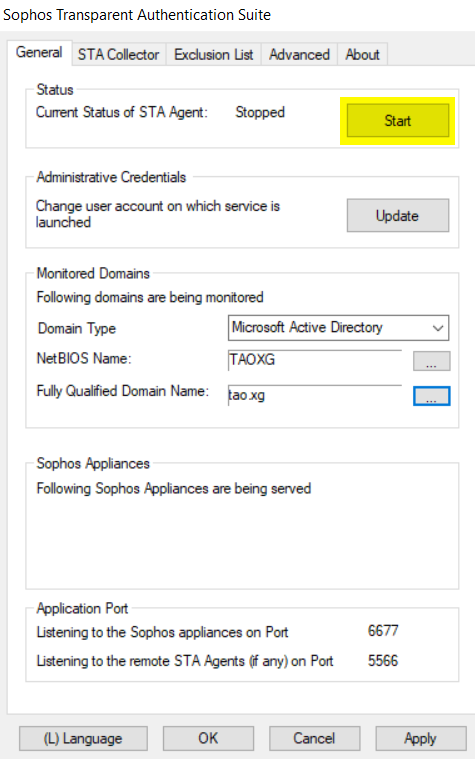
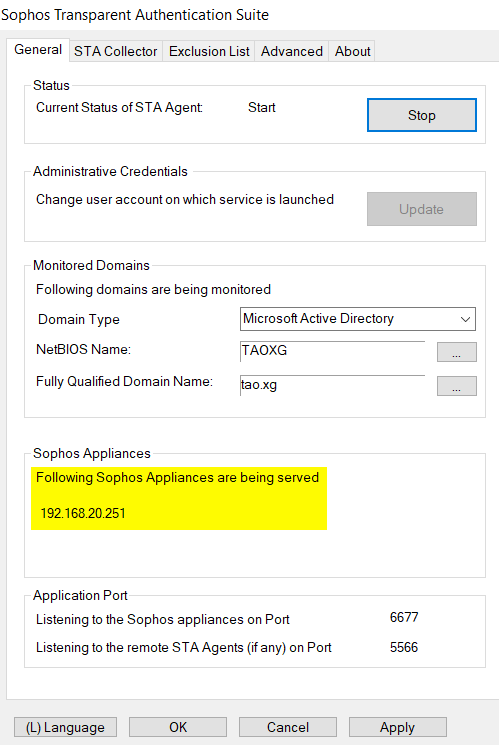
Once STAS and Sophos Firewall establishe communication, the IP address of the Sophos Firewall is displayed on the "General" tab, as below
Sometimes, STAS service might fail to be started, with the error "Failed: Cannot start service: STAS". Please refer to section "8. Troubleshooting > g) STAS service did not start due to a logon failure" for solution.
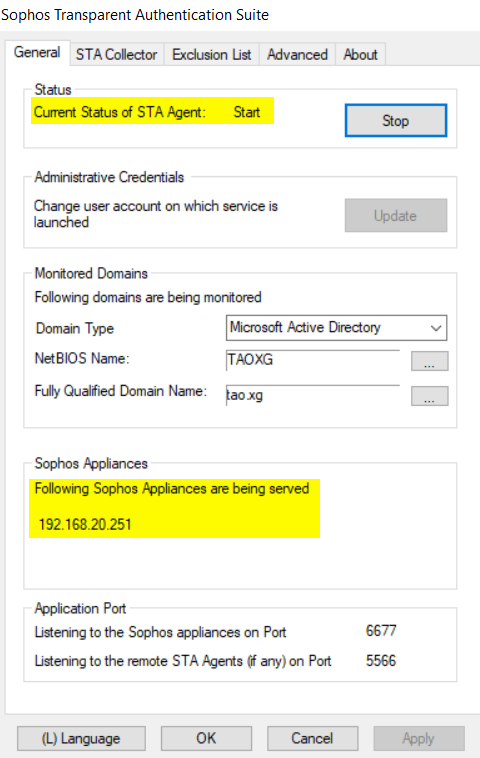
Note:
- When there are multiple STA Collectors in the same collector group, Sophos Firewall only communicates with the STA Collector on the top of list, and only that STA Collector can establish communication with Sophos Firewall, and only that STA Collector can dispaly IP address of Sophos Firewall in General tab.
- To find out which STA Collector is communicating with Sophos Firewall,
- go to STAS > General tab, check if it has Sophos Firewall IP address displayed. If yes, it is the STA Collector communicating with Sophos Firewall, or
- check backend logs in Sophos Firewall SSH terminal,
SSH to Sophos Firewall as admin, and go to 5. Device Management > 3. Advanced Shell, and run the following command
The sample output below shows Sophos Firewall has been communicating with STA Collector 192.168.20.5 since 16:00 8 Feb
grep "CTA LIVE Received from\|sending CTA_IS_ACTIVE" /log/access_server.log | tail
SFVUNL_SO01_SFOS 18.0.4 MR-4# grep "CTA LIVE Received from\|sending CTA_IS_ACTIVE" /log/access_server.log | tail
DEBUG Feb 08 16:00:36.719168 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:01:06.733092 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:01:36.748435 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:02:06.753870 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:02:36.754746 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:03:06.770399 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:03:36.784307 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
DEBUG Feb 08 16:04:06.799499 [access_server]: process_cta_live: CTA LIVE Received from 192.168.20.5
MESSAGE Feb 09 11:01:29.423157 [access_server]: process_cta_live: sending CTA_IS_ACTIVE 192.168.20.5
MESSAGE Feb 09 11:08:30.094186 [access_server]: process_cta_live: sending CTA_IS_ACTIVE 192.168.20.5
SFVUNL_SO01_SFOS 18.0.4 MR-4#
g) Create Windows Firewall rules to allow STAS traffic
If STA Collector and STA Agent are installed on different servers,
- create Windows Firewall rules on STA Collector, to allow
- inbound traffic on TCP port 5566, UDP port 6677, and UDP port 50001
- outbound traffic to UDP port 6060
- create Windows Firewall rules on STA Agent, to allow
- inbound traffic on UDP port 50001
- outbound traffic to TCP port 5566 and UDP port 50001
If STA Collector and STA Agent are installed on the same Windows server, create Windows Firewall rules on the Windows server, to allow
- inbound traffic to TCP port 5566, and UDP port 6677
- outbound traffic to UDP port 6060
Ports needed by STAS is described in section "1. How STAS works > d) Summary of ports"
Windows Firewall rules are applied on network profile (Domain, Private, Public). Make sure above Windows Firewall rules are applied to correct network profile.
h) Verify workstation poll method
To make STAS works without problem, STA Collector has to communicate with all workstations via the workstation poll method.
In above configuration, we configured STA Collector to use WMI as workstation polling method.
We need verify STA Collector can communicate with any AD workstation via WMI:
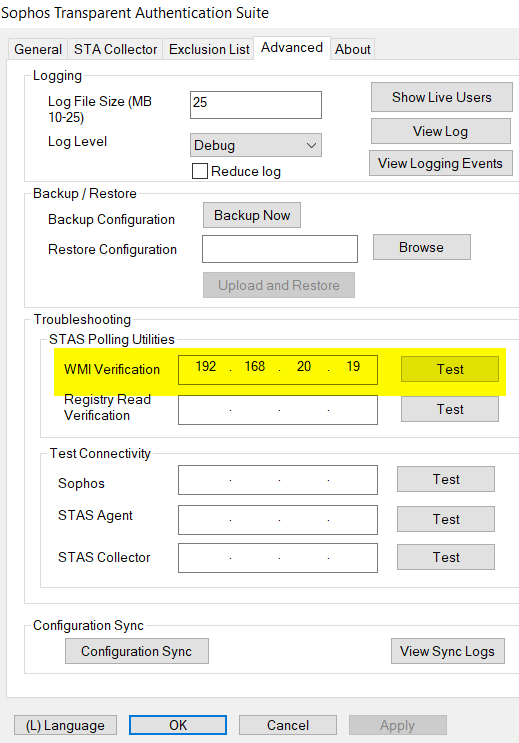
- Go to member server installed with STA Collector,
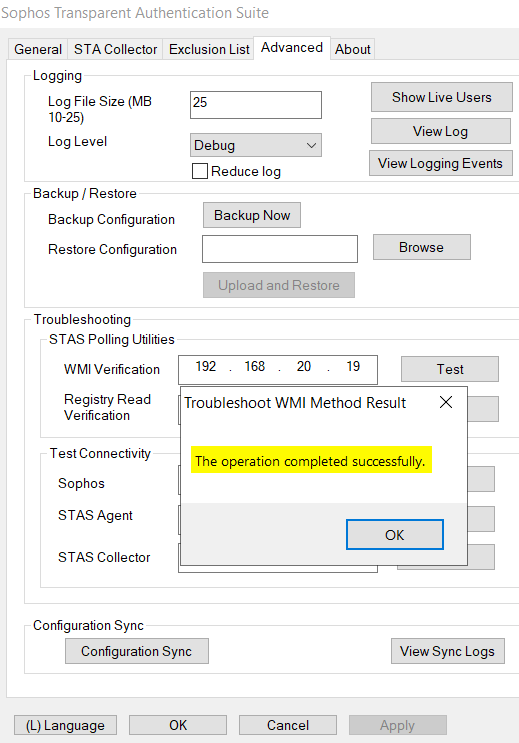
- Open STAS, go to Advanced > Troubleshooting > STAS Polling Utilities > WMI Verification, enter IP address of a workstation, and test
It should be successful. Otherwise, please check Windows GPO configuration for wmi in section "5. Configure Windows AD GPO > b) Allow inbound WMI on AD computers"
To troubleshoot wmi issue, please refer to
- Sophos Firewall: Configure user sign off detection in STAS using WMI
- Microsoft KBA: Setting up a Remote WMI Connection
7. Verify STAS is working
a) check STAS live users
user1 re-logged on AD workstation 192.168.20.19 after STAS was setup
On STA collector, open STAS, go to Advanced > Show Live Users, there was the live user.
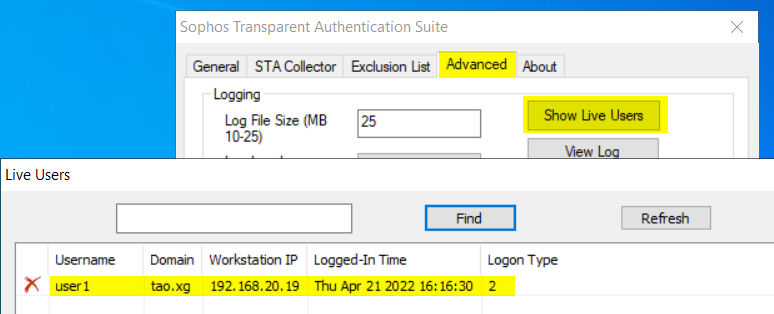
On Sophos Firewall webadmin, Current Activity > Live Users also showed the live user
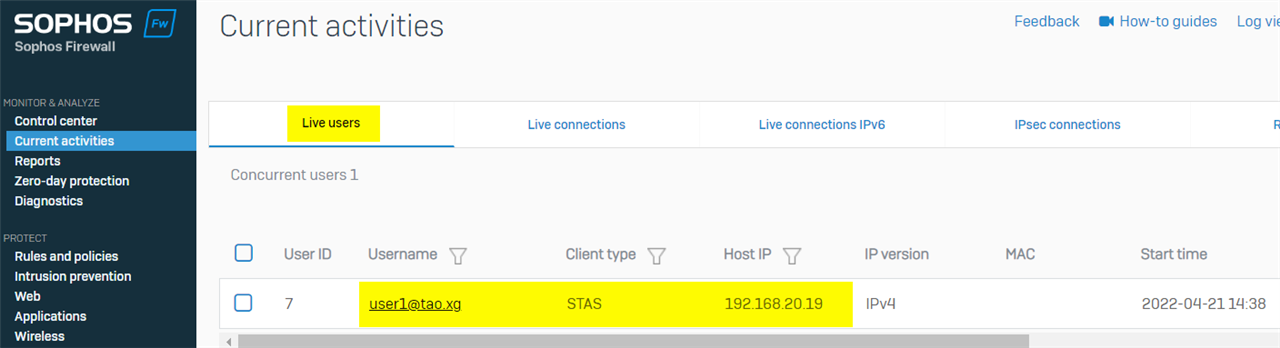
b) create a firewall rule for user group
Create a firewall rule to allow users in IT group to access Internet
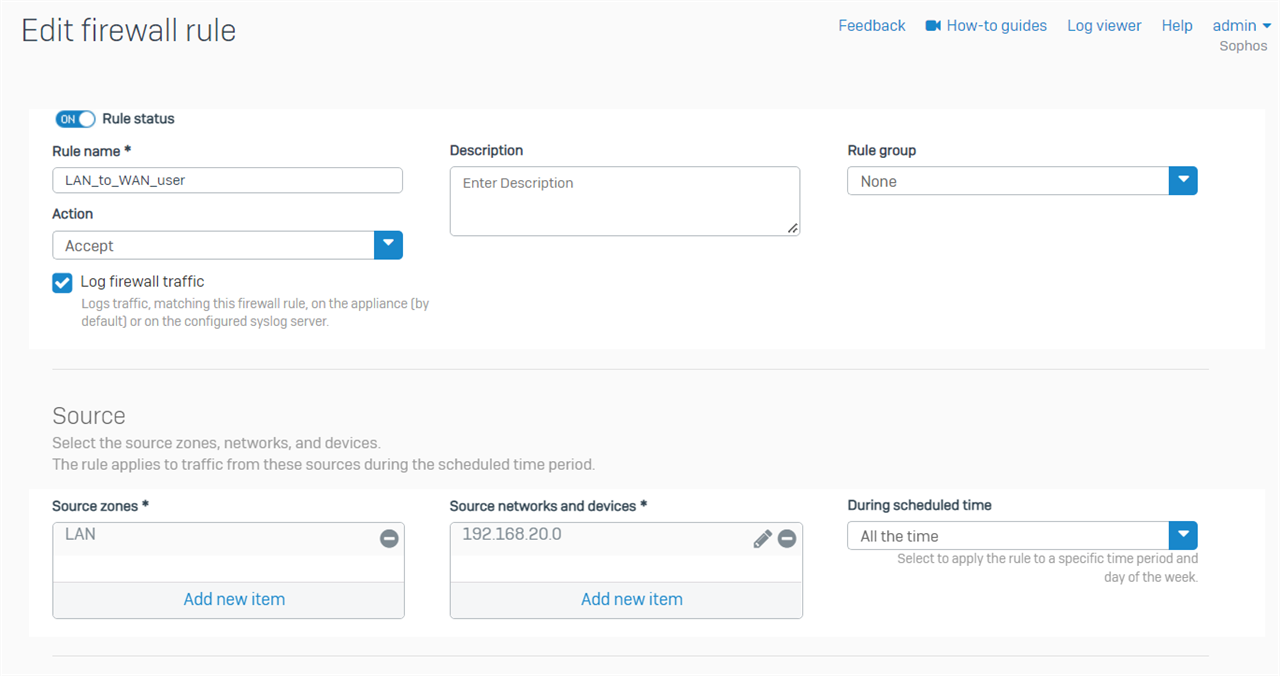
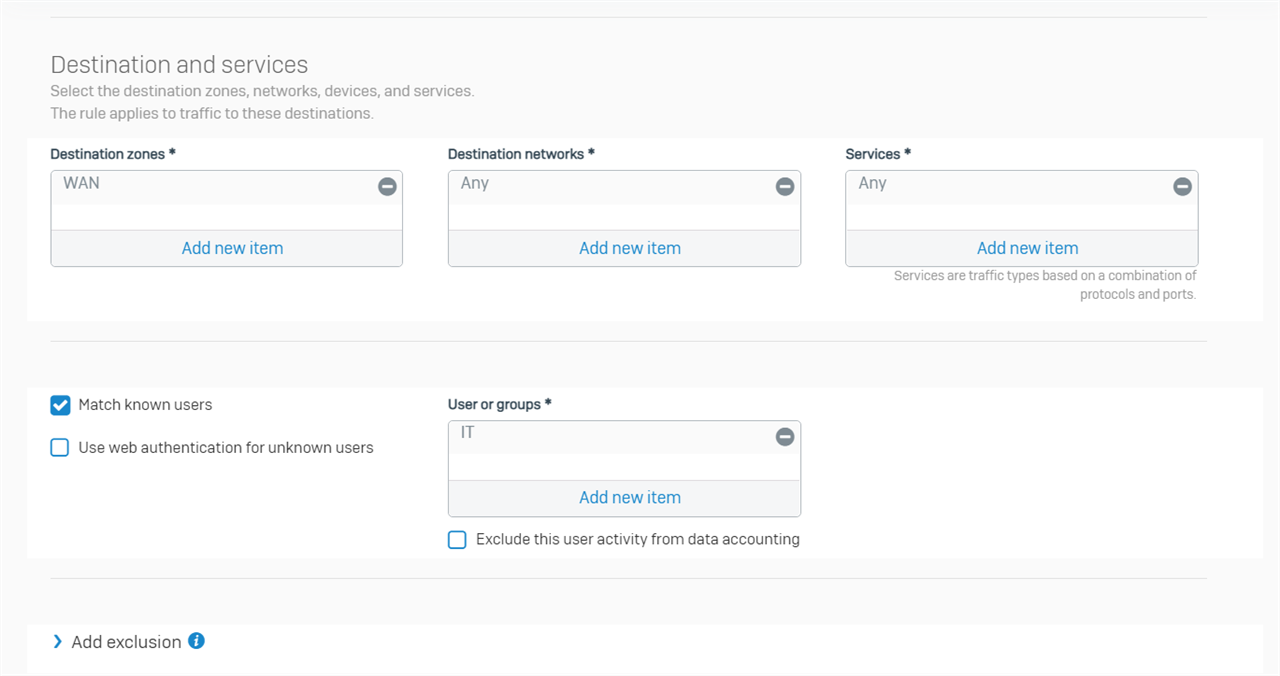
Now, 192.168.20.19 can access Internet
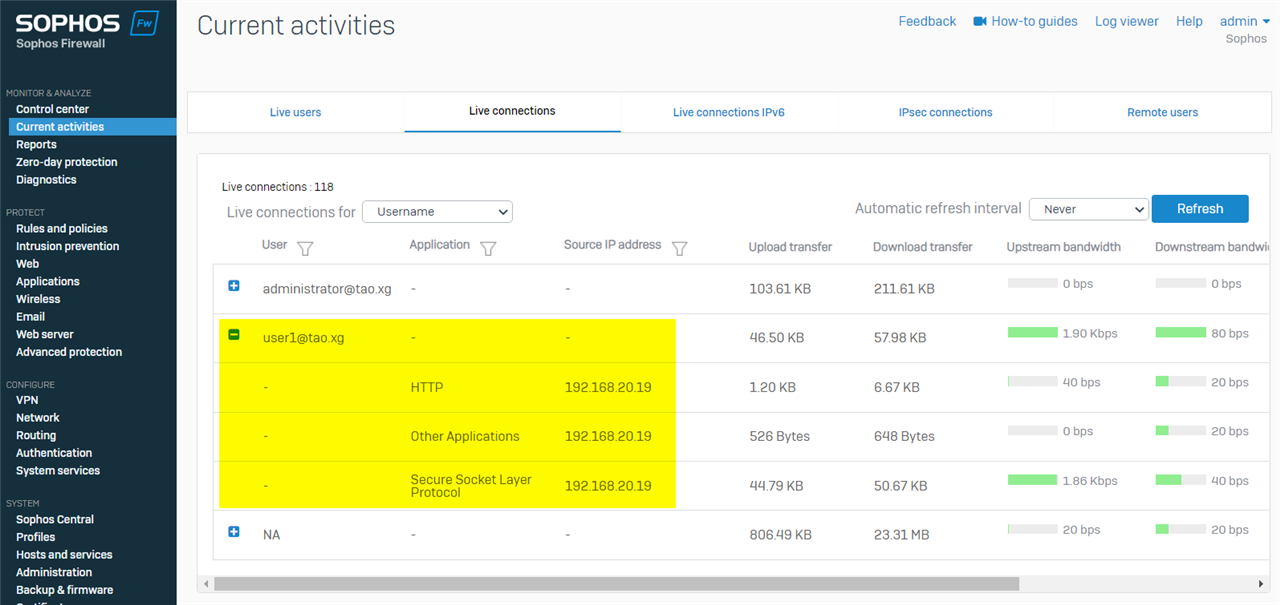
Sophos Firewall webadmin > Current activities > Live connections > Live connections for: Username shows live connection of user1@tao.xg
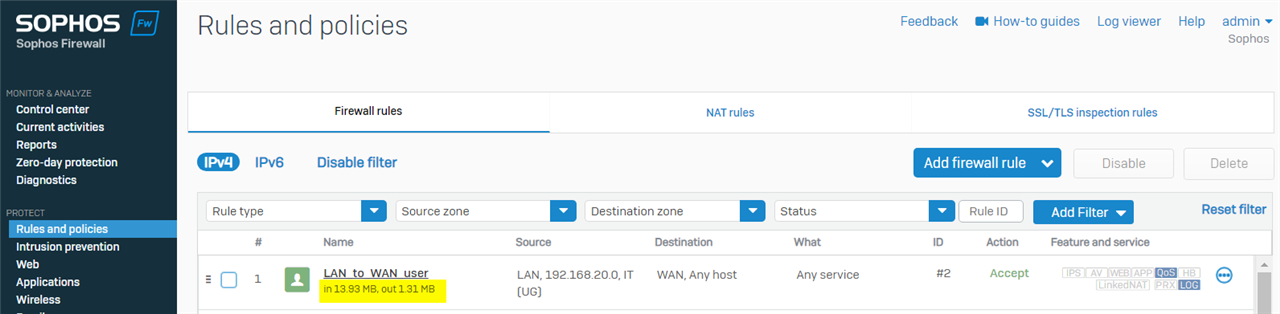
Firewall rule traffic stats also confirmed traffic from 192.168.20.19 was generated by the user in the IT group and hit the firewall rule.
8. Troubleshooting
a) STA Collector shows no Sophos Firewall IP address
When STA Collector cannot communicate with Sophos Firewall, STAS "General" tab doesn't show the Sophos Firewall IP address.
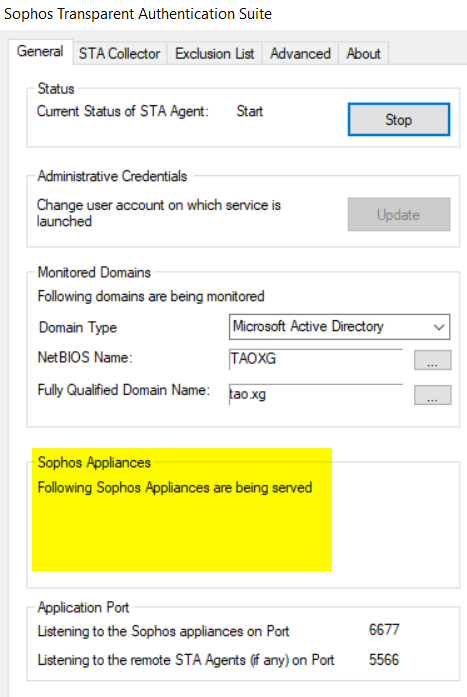
Make sure
- Sophos Firewall webadmin > Device Access has "Client Authentication" enabled on the zone where STA Collector is located.
- Windows Firewall on STA Collector allows traffic from/to Sophos Firewall. Details in the section " Install and configure STAS > f) Create Windows Firewall rules to allow STAS traffic"
c) STA Collector shows no live user
In case STA Collector doesn't detect any live user
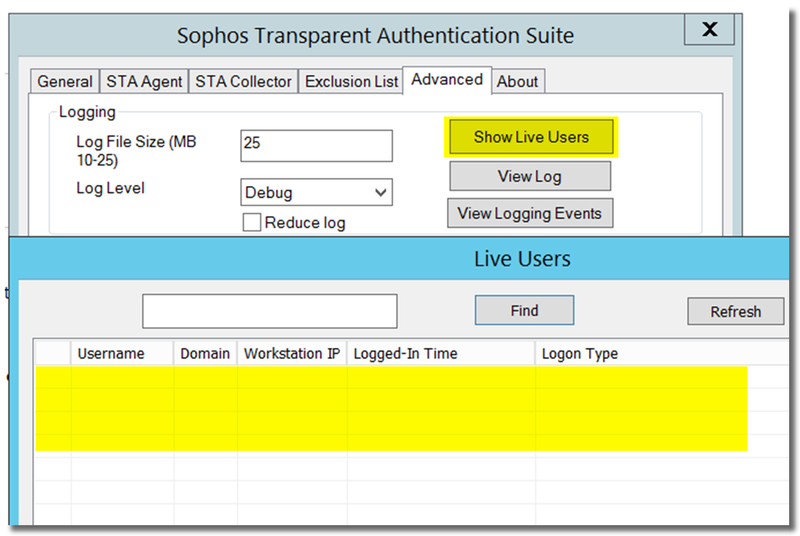
Make sure
- STAS service is started on both STA agent and STA collector
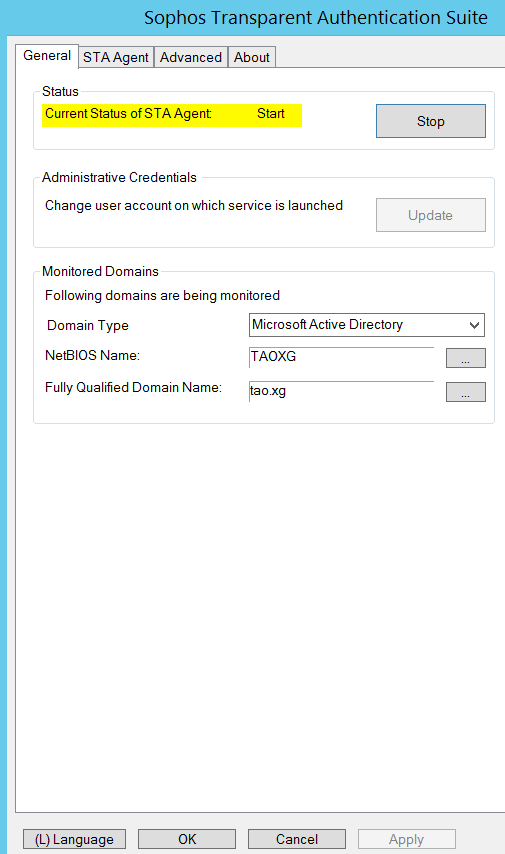
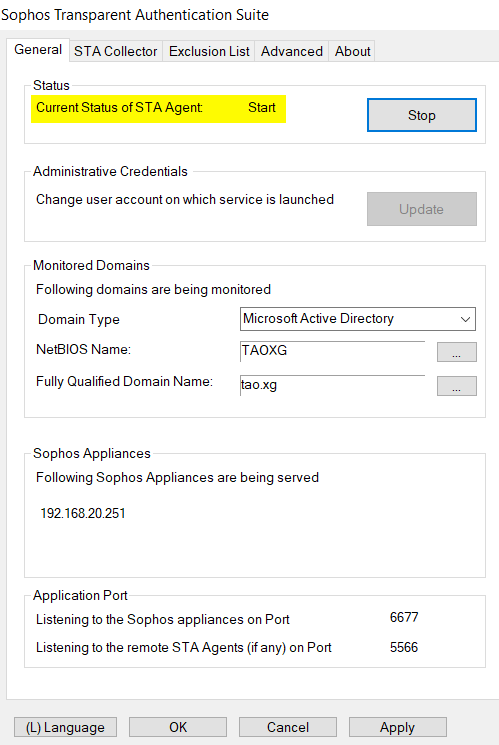
- STA Collector and Sophos Firewall established communication
- STA Collector can communicate with AD workstation via workstation polling method. Details in the section " Install and configure STAS > h) Verify workstation poll method"
- Event ID 4768 is generated in Windows Event Viewer when an AD user logs on an AD workstation. Details in section "5. Configure Windows AD GPO > e) Verify event ID 4768 was generated for user logon"
- STAS was installed by right click on installation file > Run as administrator
c) Sophos Firewall has no STAS live user, although STA Collector has them
If Sophos Firewall doesn't show any live user, but STAS shows live users, make sure
- Windows Firewall rule on STAS server is configured properly, as per section " Install and configure STAS > f) Create Windows Firewall rules to allow STAS traffic"
- Sophos Firewall has "Client Authentication" enabled on the zone where the STA Collector and AD workstation are located.
- Authentication service on Sophos Firewall is running. It can be verified onable Sophos Transparent Authenticationn Sophos Firewall webadmin > System services > Services, as below
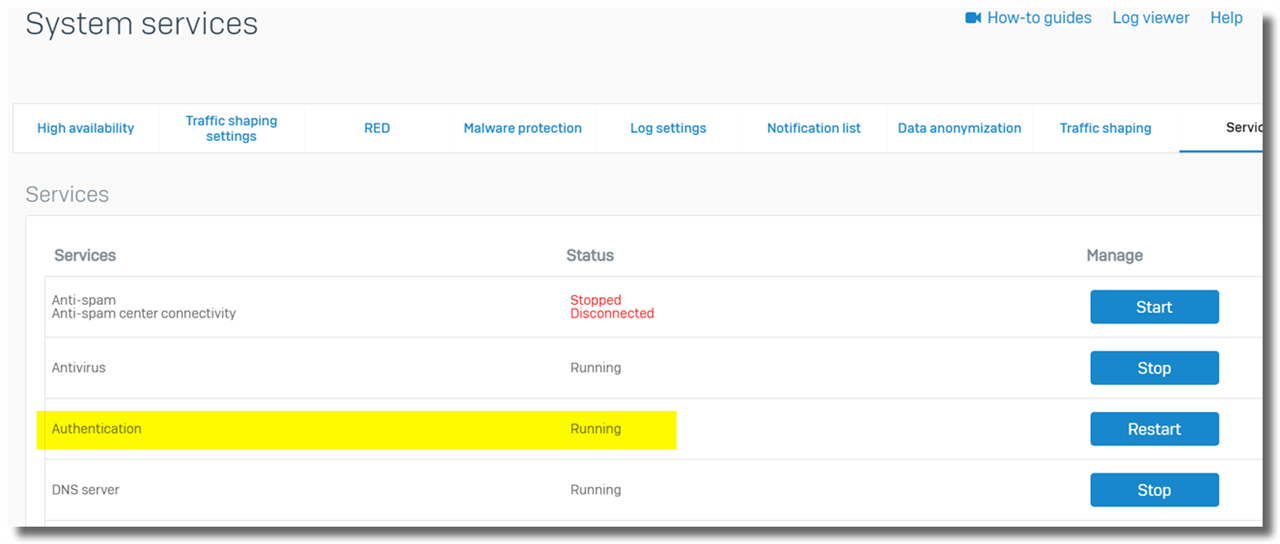
- Check if Sophos Firewall reaches STAS server via static route. Details in section "9. Known issues"
d) STA Collector keeps removing live user
STAS can detect live user on AD workstation, however, it removes live user after a while.
Make sure
- STAS can communicate with AD computers via the workstation poll method. Details in the section " Install and configure STAS > h) Verify workstation poll method"
- all background service accounts on AD computers have been added into STAS > "Login User Exclusion List". Details in the section " Install and configure STAS > d) Configure Exclusion List"
e) Sophos Firewall has some STAS live users missing
Firewall webadmin GUI > Current Activity > Live Users show some STAS live users, but not all of them. Some STAS live users are missed on Sophos Firewall.
Make sure
- STA Collector can communicate with AD computers via the workstation poll method. Details in the section " Install and configure STAS > h) Verify workstation poll method "
- all background service accounts on AD computers have been added into STAS > "Login User Exclusion List". Details in the section " Install and configure STAS > d) Configure Exclusion List"
Please also check if Sophos Firewall reaches STAS server via static route. Details in section "9. Known issues".
f) Group policy of audit logon events is not updated on AD computer
- Make sure NIC on AD computer connected to AD DC belongs to Domain network.
Here is the Microsoft Technet post about how to change network profile of a NIC. https://social.technet.microsoft.com/Forums/en-US/1a948231-a6ef-4bd1-9676-2b565d572762/domain-network-turns-to-public?forum=win10itpronetworking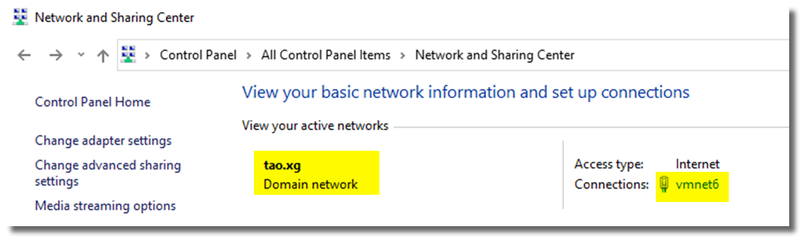
- On AD workstation, try to disable Windows Firewall on all NIC, and enable it later once GPO is updated.
- If the above doesn't solve the issue, please contact Microsoft technical support.
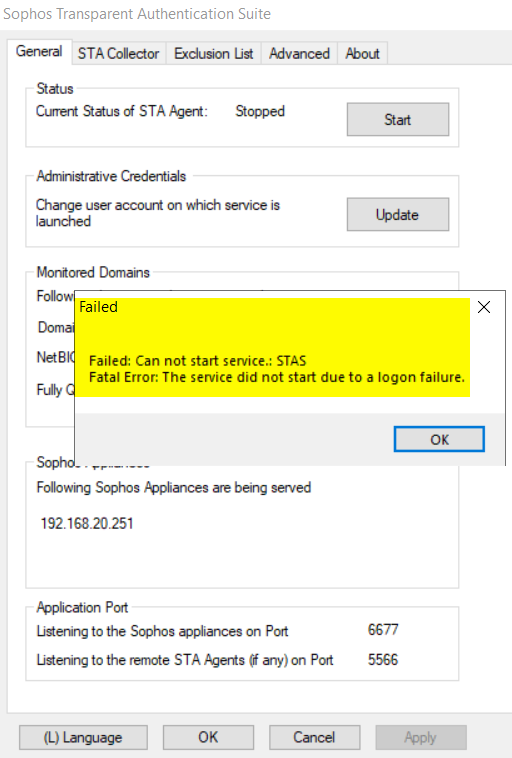
g) STAS service did not start due to a logon failure
If STAS service fails to start with "Fatal Error: The service did not start due to a logon failure.", make sure the account for STAS is a member of AD group "Domain Admins".
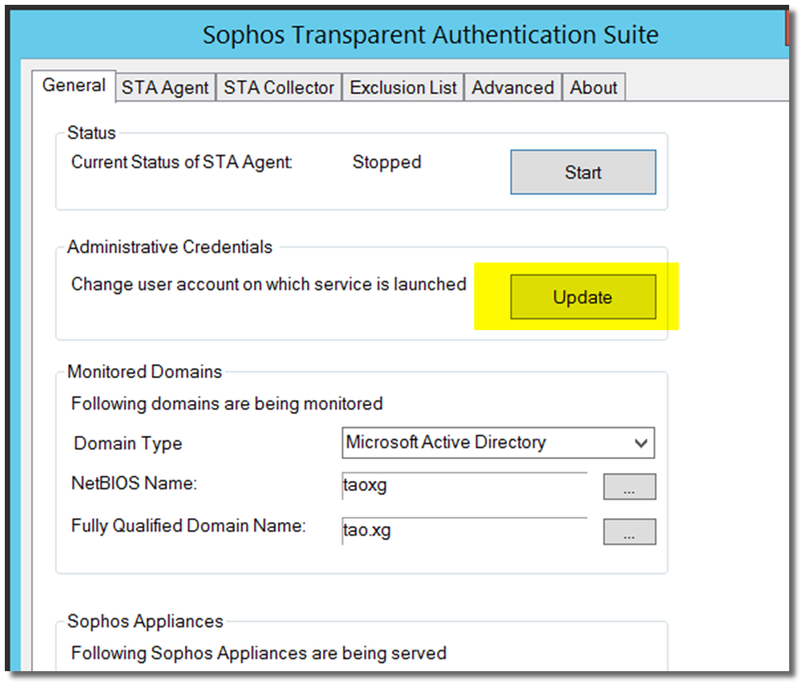
You can update the account for STAS in the "General" tab, as below
If the above doesn't fix the issue, please try the following:
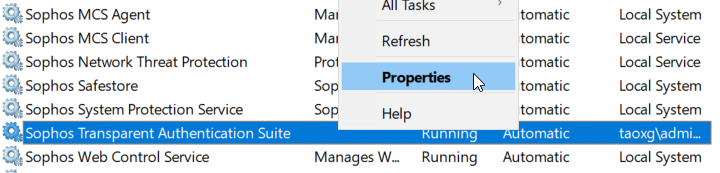
1) Go to Windows Service, find "Sophos Transparent Authentication Suite". Right click on it, and click on "Properties"
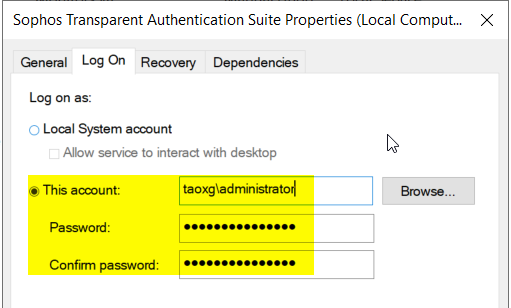
2) Go to "Log On" tab, and enter AD Domain admin account and password again.
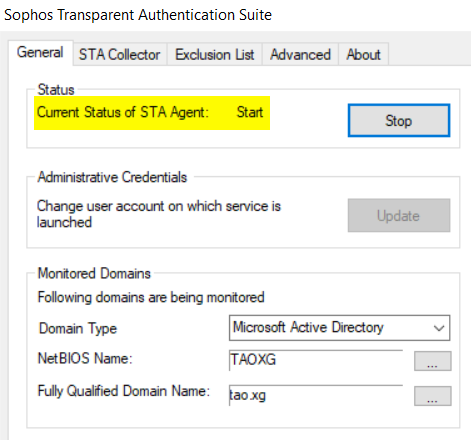
3) Go back to STAS, click on "Start" button, and now STAS should Start.
9. Known issues
a) Dead entry timeout: must be 0, otherwise STAS stops working (applies to STAS v2.5.1.0 and earlier)
b) When Sophos Firewall reaches STAS server via a static route, Sophos Firewall cannot communicate with STAS server after reboot/boot-up.
Symptom: Sophos Firewall doesn't send packets to STAS server UDP port 6677 to actively query live user on workstations. Sophos Firewall can only passively receive live user information from STAS server.
Workaround: Manually restart authentication service after firewall reboot/boot-up.
- in Advanced Shell, please run the command "service access_server:restart -ds nosync", or
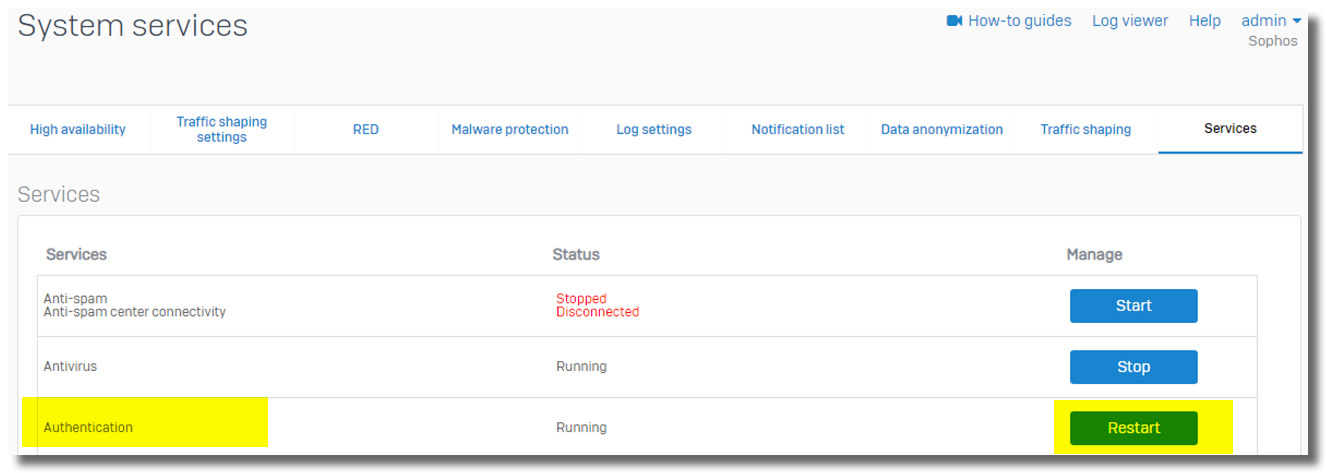
- in webadmin GUI, go to "System service" > "Services", and then Restart "Authentication" service, as below
[ Note: This bug (NC-84910) will be fixed in Sophos Firewall OS v18.5 MR5. ]
10. Appendix
a) Enable SSL on Windows LDAP service
Note: If you need technical support to enable SSL on Windows LDAP service, please seek help from Microsoft.
In Server Manager, Add Roles and Features
Select "Role-based or feature-based installation"
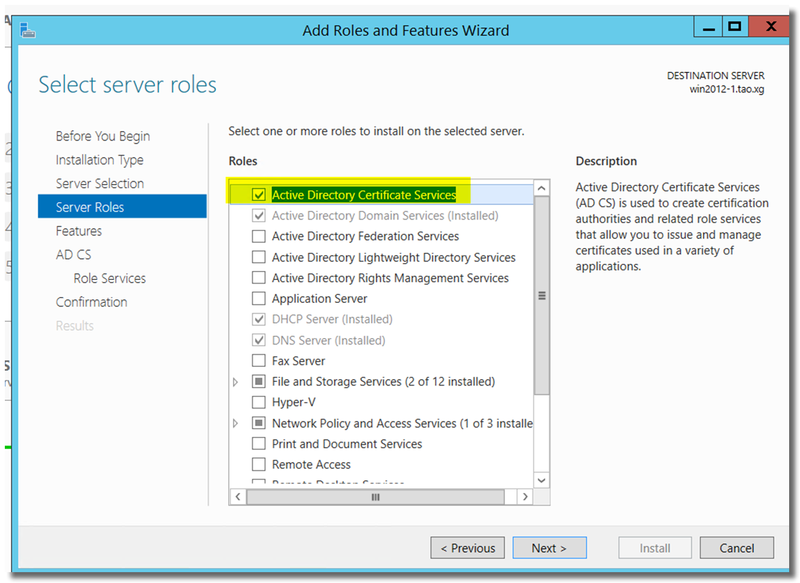
Add role of "Active Directory Certificate Services"
Click on "Next", install "Certificate Authority"
Install
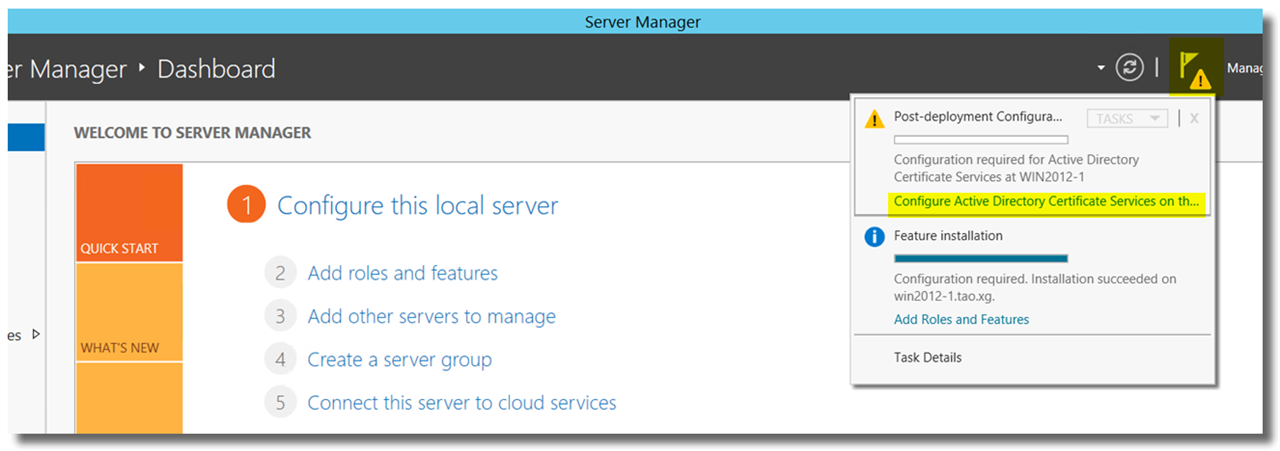
Once the installation is complete, in Server Manager, click on "Notifications" > Post-deployment Configuration > Configure Active Directory Certificate Services
In "AD CS Configuration", click Next to continue
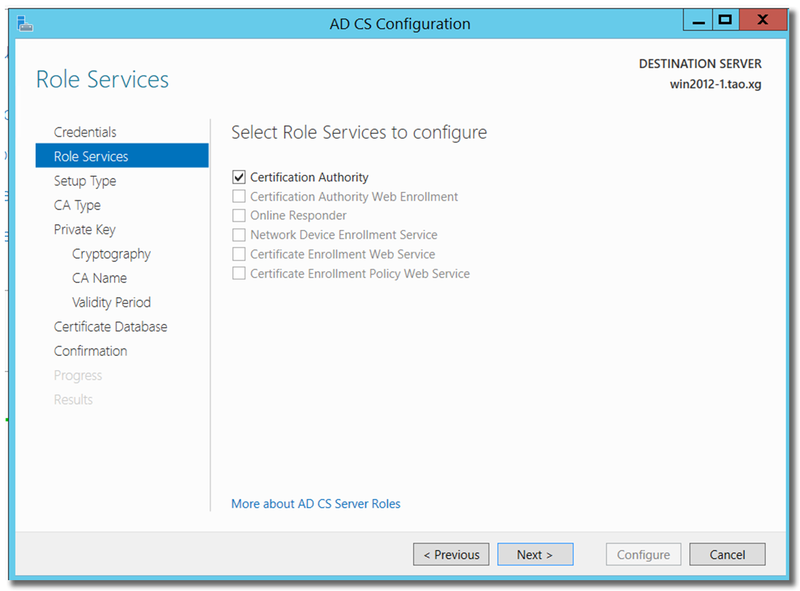
Choose "Enterprise CA"
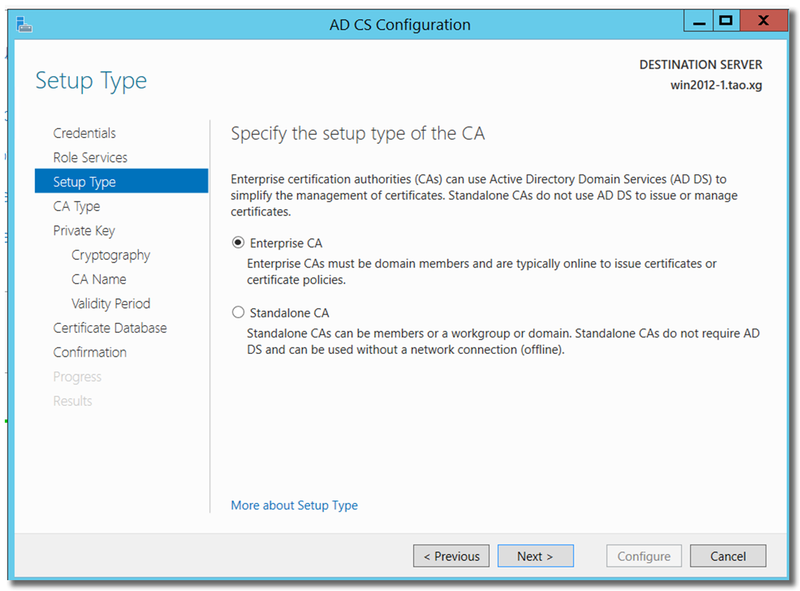
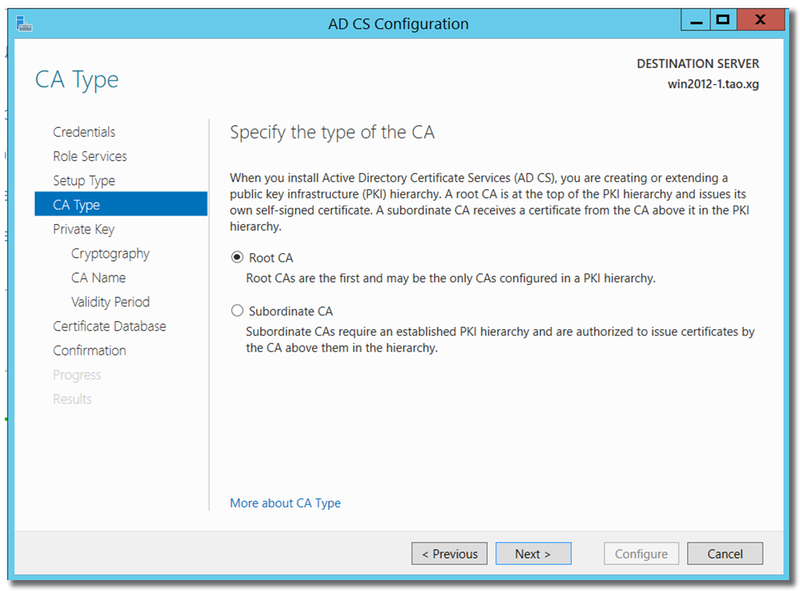
Choose "Root CA"
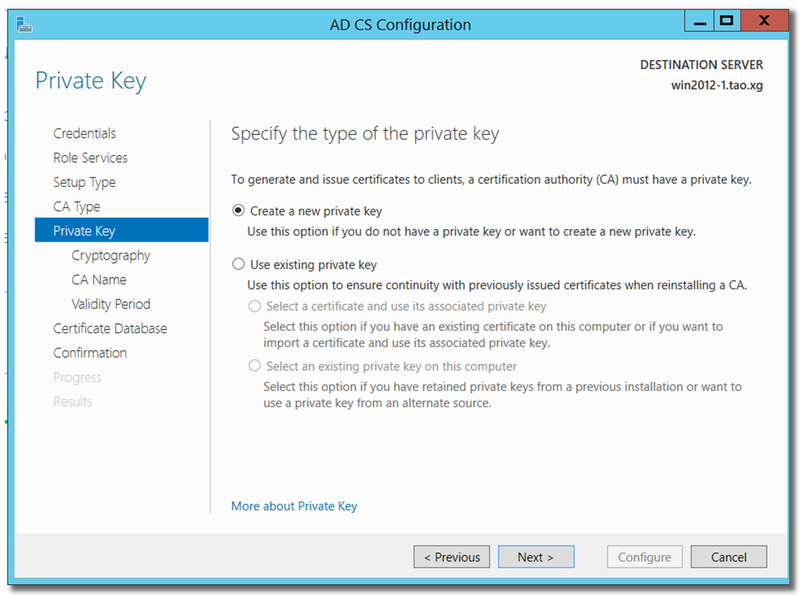
"Create a new private key"
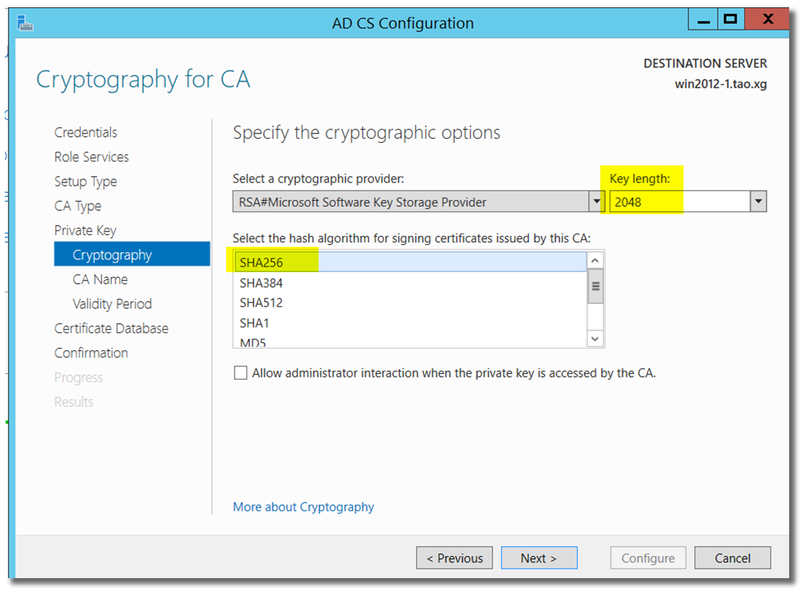
Key length: at least 2048
Hash algorithm: SHA256 or higher, don't choose SHA1/MD5...
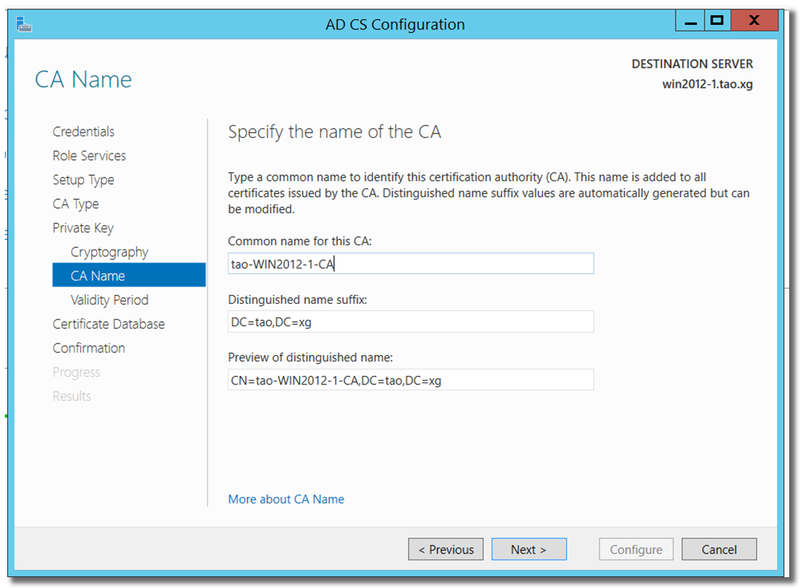
Input essential information for the CA
Click on "Configure" to generate root CA.
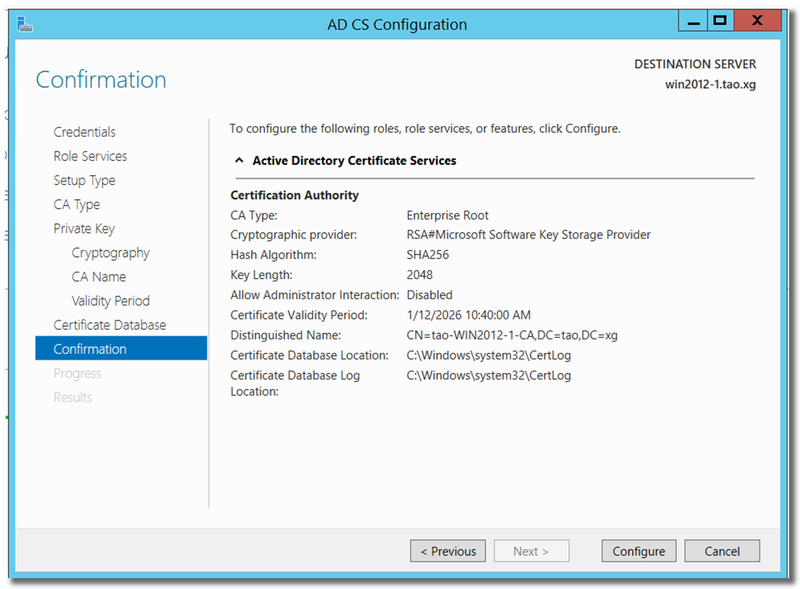
Now, restart the DC, and Windows automatically enables SSL on LDAP service.
11. Edition History
2022-08-10, updated section "2. Limitation" with "d) Windows server core edition is not supported". Thanks to Kevin Kuphal.
2022-07-18, updated section "2. Limitation" with "c) NAT is not supported". Thanks to David Raj Suntharesan.
2022-05-04, major updates:
- provided details about STAS logon type1 and 2
- improved STAS deployment - STA Collector is not recommended to run on DC, as it generates a high volume of traffic, according to Sophos Firewall Online Help.
2021-10-06, minor change, renamed "XG firewall" to "Sophos Firewall"
2021-08-13, updated section "Configure Exclusion List"
2021-07-23, added section "9. Known issues"
2021-02-10
- added section "1. How STAS works > c) Deployment example"
- updated section "6. Install and configure STAS > c) Configure STA Collector"
- updated section "6. Install and configure STAS > g) Start STAS"
- added section "8. Troubleshooting > e) Sophos Firewall has one more STAS live users missing"
- updated ToC
2021-01-29, updated ToC.
2021-01-25, converted from PDF to HTML by emmosophos. Thank you.
2021-01-19
- updated section "3. Test environment > a) Network Topology"
- added section "7. Verify STAS is working > b. create firewall rule for user group "
- updated section "8. Troubleshooting "
2021-01-15, first edition
Added TAG
[edited by: Erick Jan at 3:01 AM (GMT -7) on 28 Oct 2024]