Hallo zusammen,
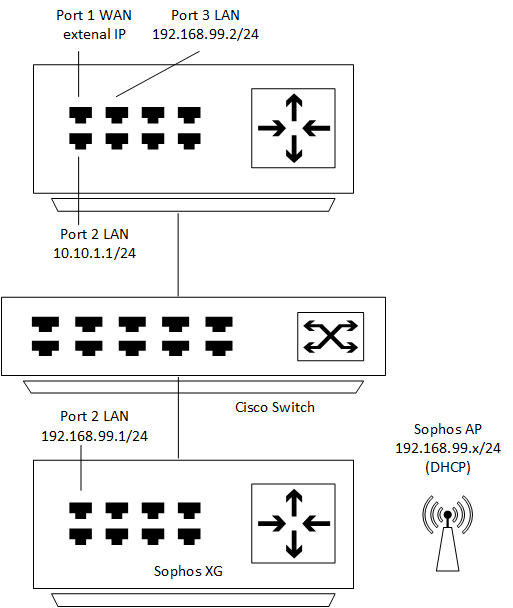
ich habe vor kurzem eine WatchGuard Firewall installiert und die zuvor bestehende Sophos XG als Management Gerät für die AccessPoints an das alte Subnetz angeschlossen.
Zuvor war nur die Sophos als Hauptfirewall an dem Standort, nun ist die WatchGuard die Hauptfirewall und die Sophos dient nur für die Verbindung für die Sophos AccessPoints.
Aktuell ist es so, dass die WLAN Clients und die Sophos keine Internetverbindung über die WatchGuard aufbauen können. Daher möchte ich eine Route auf der WatchGuard und auf der Sophos erstellen, sodass die Sophos APs und die WLAN Clients über die WatchGuard auch eine Verbindung untereinander haben.
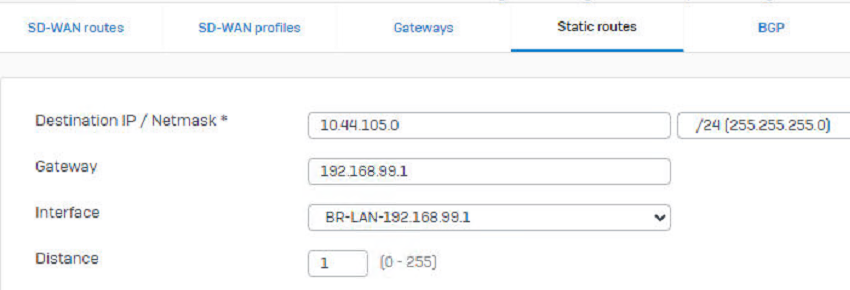
Wie muss ich den die Route auf der Sophos und der Watchguard konfigurieren, damit das 192.168.99.x Netz auch über den WAN Port der WatchGuard raus ins Internet könnnen?
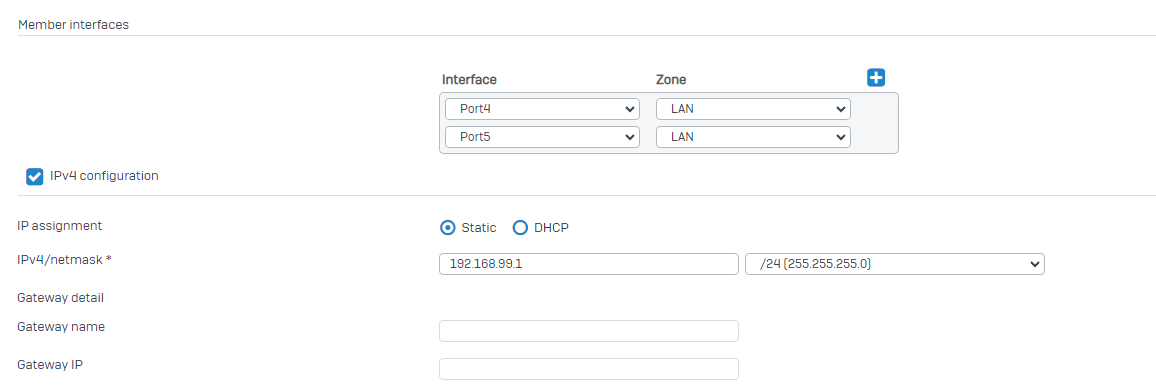
Zudem möchte ich das bestehende Netz 192.168.99.x/24 für Gäste Wlan getrennt vom produktiven Netz 10.10.1.x/24 bestehend lassen und eine zweite SSID Verbindung für das produktive Netz 10.10.1.x erstellen.
Wie muss hier die Konfiguration auf beiden Firewalls eingerichtet werden damit dies funktioniert?
Muss ich eine standard Route auf beiden Firewalls erstellen und dann noch eine Firewall Regel auf beiden Seiten. Wie genau sieht hier die Konfiguration aus?
Besten Dank vorab für die Unterstützung.
Grüsse
This thread was automatically locked due to age.