Hi all,
AP configuration works. I am able to remove & add the AP's.
AP's are recognized and shown as active.
I can see the traffic between AP & XGS Port 2712.
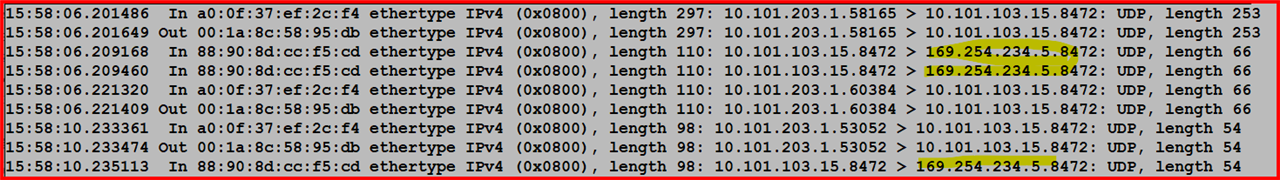
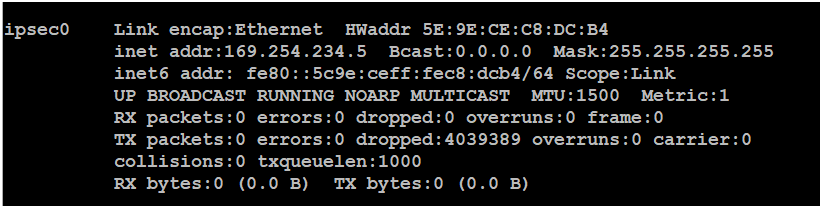
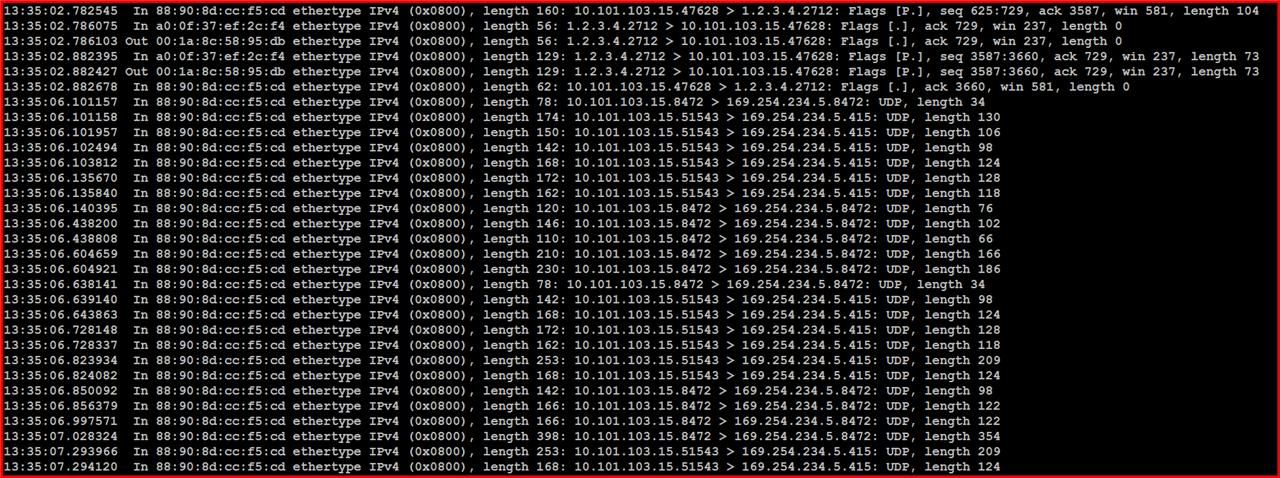
Traffic to port 8472 from firewall to AP is not answered, but i see packets from AP to APIPA-address.
SSID's with "bridge to AP-Lan" or "bridge to VLAN" are working.
With "separate zone" there is no traffic from/to the client.
AP's connected directly to XGS or placed behind RED are working.
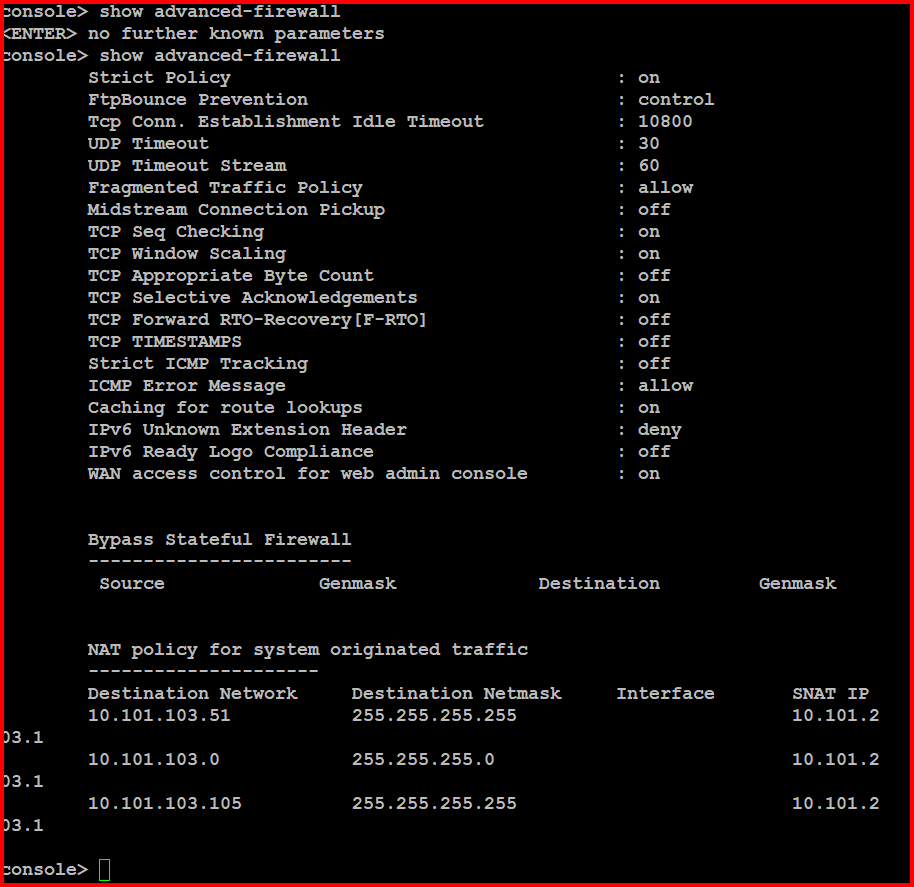
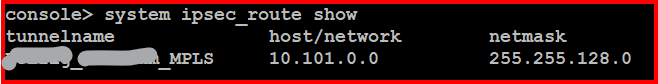
Network:
AP --- SG-UTM --------- IPSec -------- XGS --- ClientVLan
AP: 10.101.103.15
XGS-Interface at ClientVLAN 10.101.203.1
XGS-Version: SFOS 19.0.5
Packet Capture from SG-UTM:
Greetings,
Dirk
Added TAGs
[edited by: Erick Jan at 12:27 PM (GMT -7) on 26 Aug 2024]