Hello everyone,
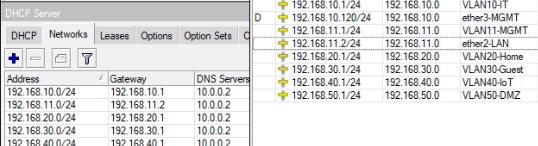
I’ve included my home network diagram and Sophos configuration below. After setting up Sophos Home (on ESXi) in bridge mode with VLANs, I assigned a static IP address of 192.168.11.10 to the bridge port. However, this IP address cannot ping the gateway (192.168.11.1), although I can access the web administrator interface from a VM using this IP.
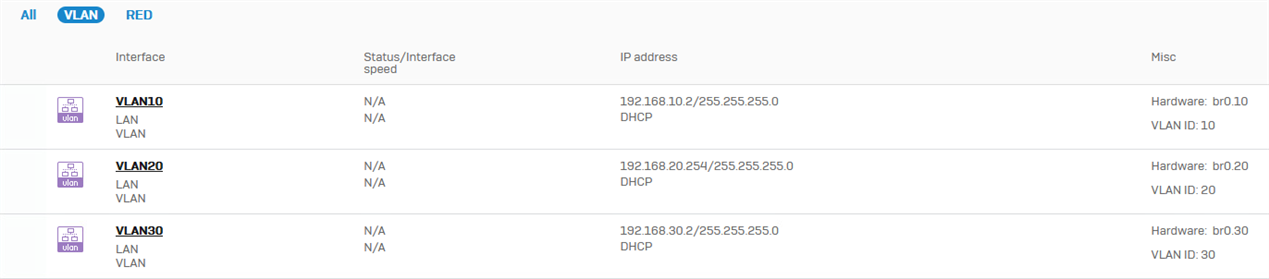
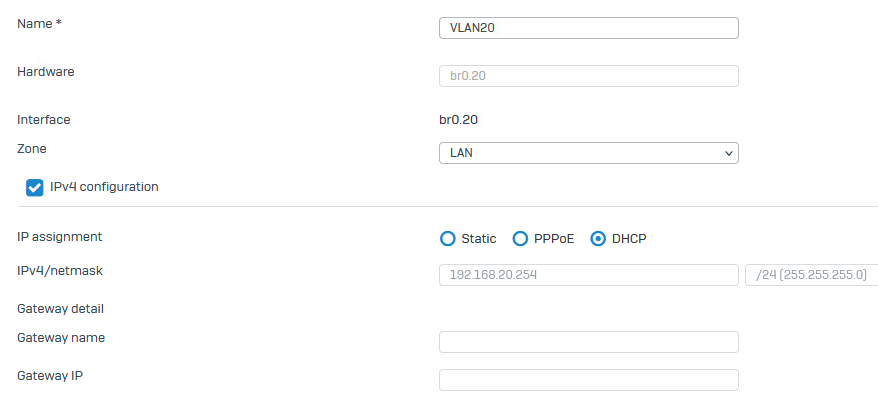
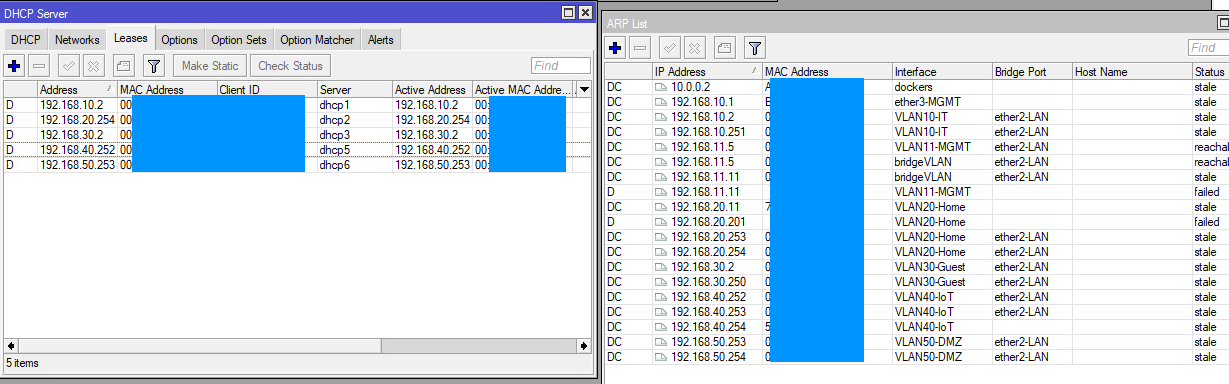
I proceeded to set up the VLAN interfaces. If I use static IPs, my router (RouterOS CHR) cannot detect them or ping the gateways. I can only use DHCP. However, clients (servers, PCs, phones, etc.) can access the internet using either static IP or DHCP, and they can ping the gateway without issues (except for the management VM, cannot ping the gateway).
What could be wrong or missing in my configuration?
I’m a newbie with Sophos and not a professional in networking, so I would greatly appreciate any help you can provide. Thank you very much!
Network diagram:
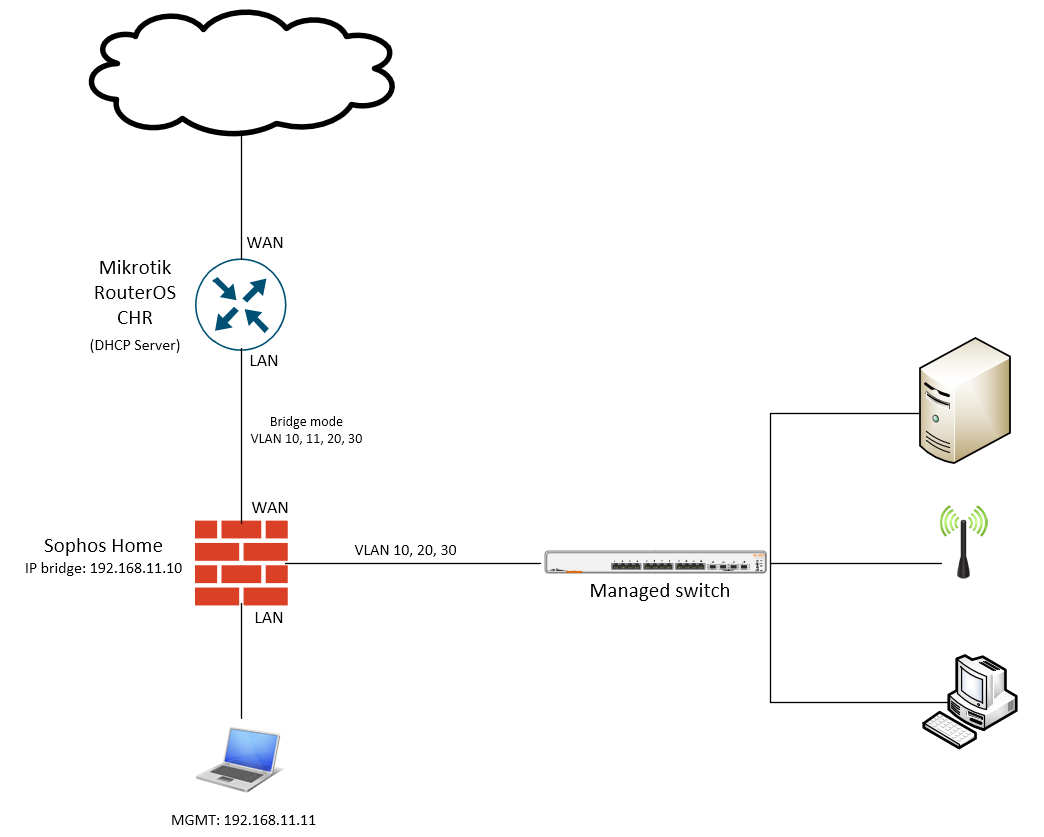
Bridge interface:
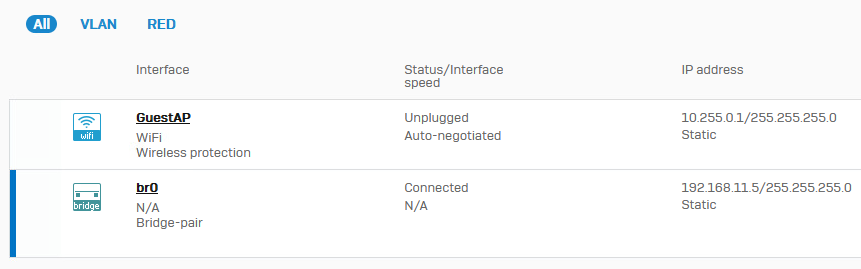
VLAN interfaces:
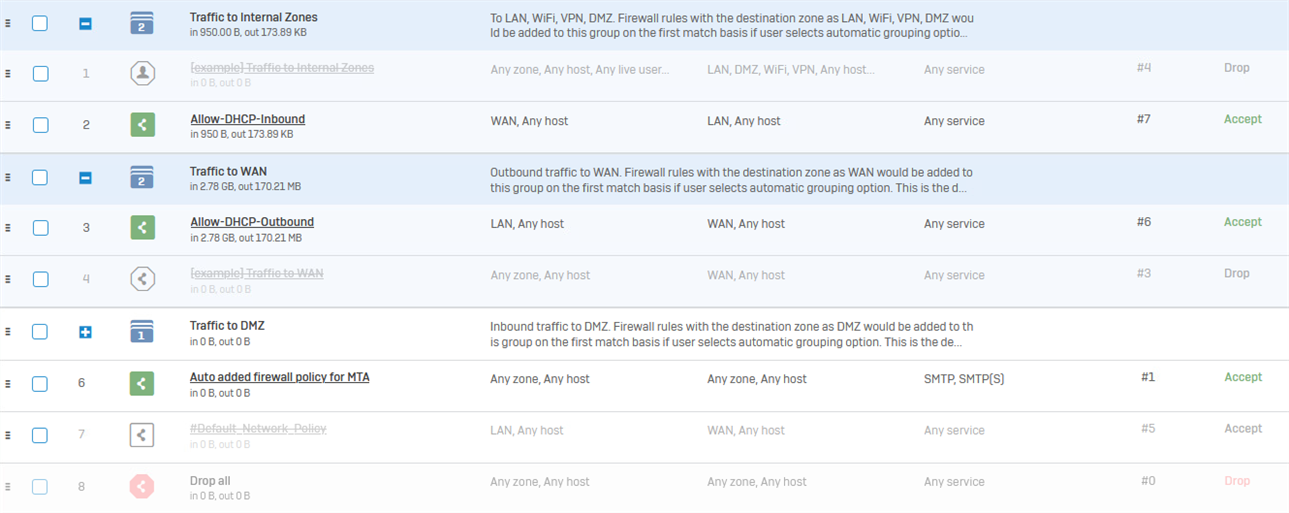
Rules config:
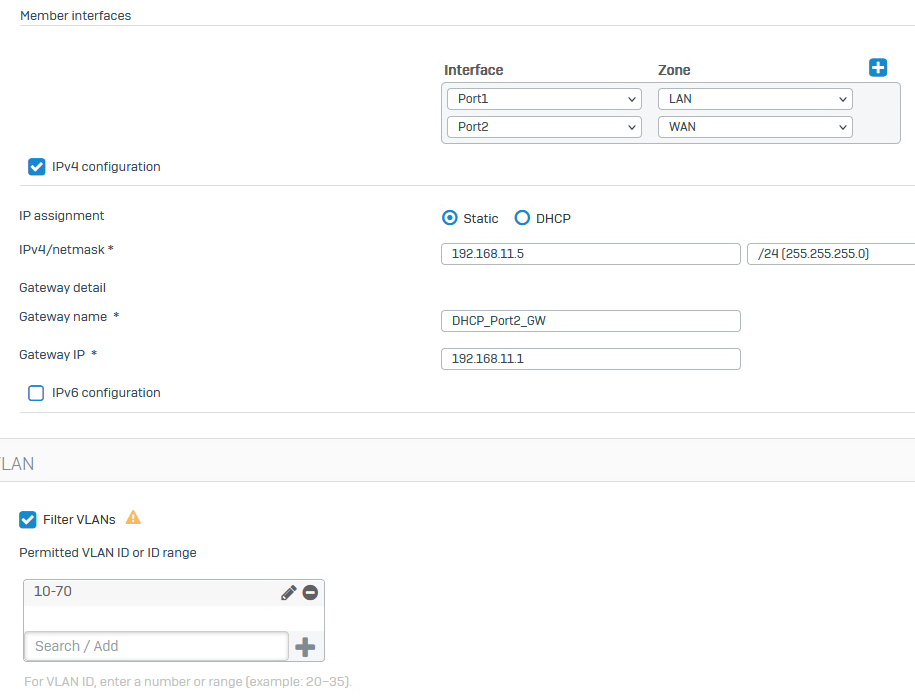
RouterOS DHCP and ARP table:
Added V20.0 MR2
[edited by: Erick Jan at 3:50 PM (GMT -7) on 2 Sep 2024]