Hi All,
We have a question in Full tunnel site to site IPsec VPN.
When we create a local 192.168.183.50/32 to remote Any site to site IPsec VPN.
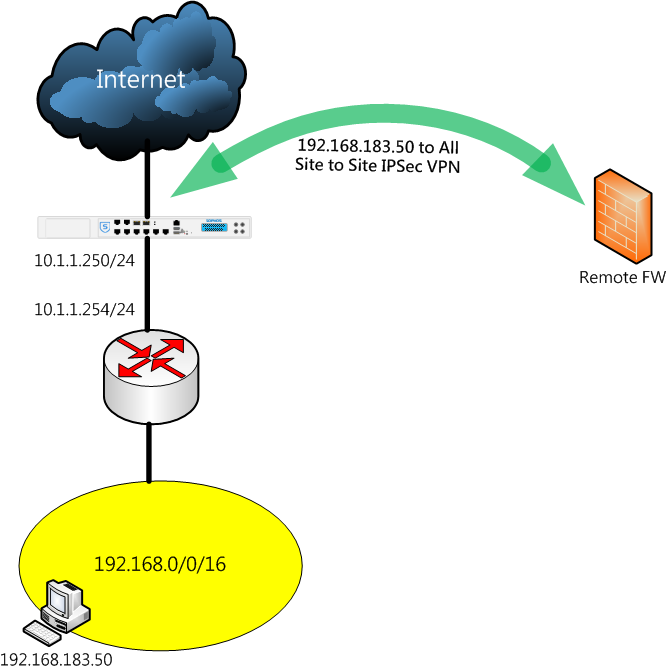
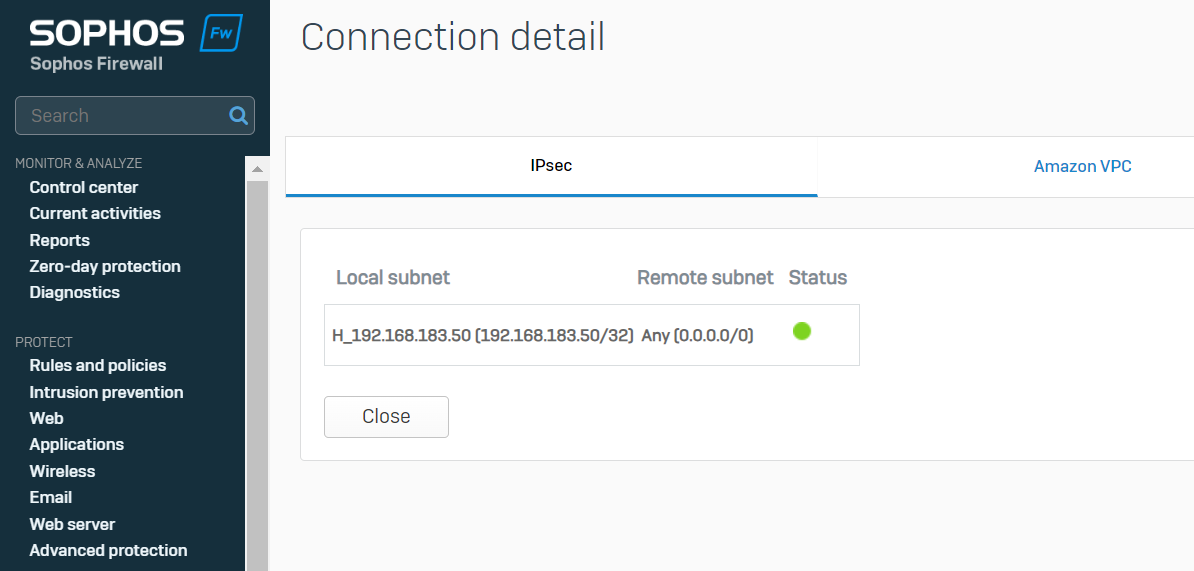
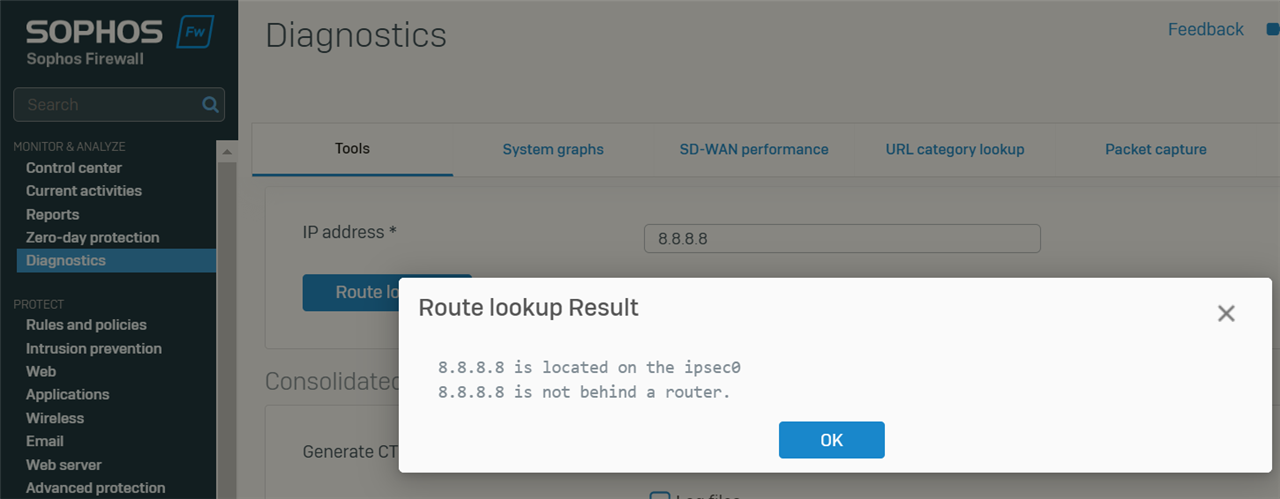
We found that XG's own routing will also be carried out through this VPN tunnel.
There is a similar discussion in the forum, link as below.
I have tried 17.5.14 and 19.0.3, and both of them have the same bug.
Does anyone know which version of firmware this bug is resolved in?
This thread was automatically locked due to age.


