Hi everyone!
We are using a Sophos XGS2300 (SFOS 19.0.1 MR-1).
We uploaded a pfx-certificate to the WAF which specifically included only the webserver certificate itself and its intermediate certificate.
But, when we check the site with a tool like https://www.ssllabs.com/ssltest/ we see that the server (e.g. the Sophos Firewall) also sends the root certificate. Which is not what we want and which we don't see when we check sites like microsoft.com.
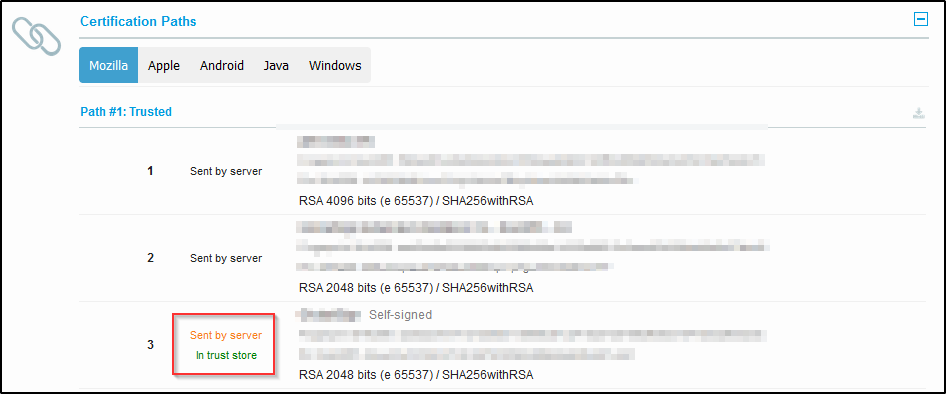
Are we correct to assume that this is done by the XGS? Is that intentional? Is there a way to circumvent this?
Thanks!
Best regards,
Markus
This thread was automatically locked due to age.


