Hi,
I'm using a home licence (XG 18.0.0 GA-Build354) on my own hardware and I'm trying to configure a simple web server to be externally available via a WAF rule.
Setup:
Example:
WAN - 11.22.33.44 (www.my-site.uk)
LAN - 10.1.1.50 (caton-edge)
The setup for the most part is simple, I have a host within my LAN that's running Nginx within a container.
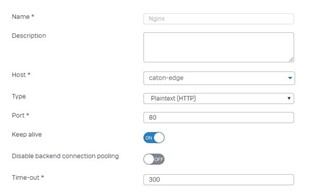
The host that is running Nginx has been configured as a web service within Sophos:
I can access the Nginx page internally on port 80 (http://10.1.1.50) without issue.
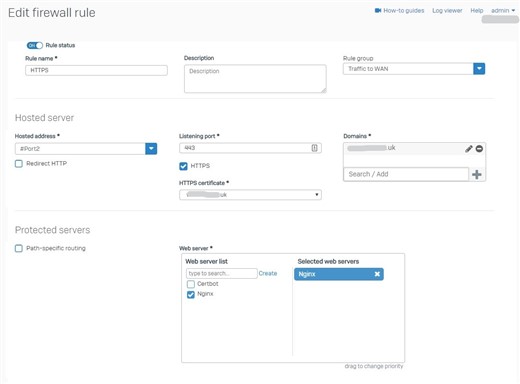
My WAF rule looks like so:
For the WAF rule I have HTTPS certs from Lets Encrypt that I would like to use.
So the cert is the cert generated by the certbot.
Issue:
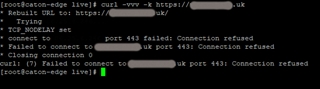
Once the WAF rule is running, I'm unable to access the site via it's configured (external) DNS name e.g. 11.22.33.44 (https:/.../www.my-site.uk) from either the WAN or LAN interface,
The response received is that the connection is refused:
Troubleshooting:
After reading around on the Sophos site I see that the Web Portal runs on port 443 (although internal only), but to ensure that there is no port conflict I have disabled this via:
Administration > Device Access > User Portal (uncheck WAN)
And I have changed the port number of the User portal to something other than 443.
To ensure the above is effective, I have rebooted the device as a belt and braces approach.
With the above in place, I still get the same (no) response.
What I have found to work, is changing the HTTPS port in the WAF rule, so that the external port is e.g. 445
When accessing https://www.my-site.uk:445 the site loads as expected - the same is also true when configuring the WAF rule as HTTP rather than HTTPS
However, when returning back to the default of 443, the same connection refused error is presented.
I have looked through both the Web server protection logs and IPS logs, and nothing is logged upon failure, only when the above steps are taken to change the port number are records logged (also tail -f /log/reverseproxy.log on the advanced shell).
Thanks in advance, any help will be appreciated.
This thread was automatically locked due to age.