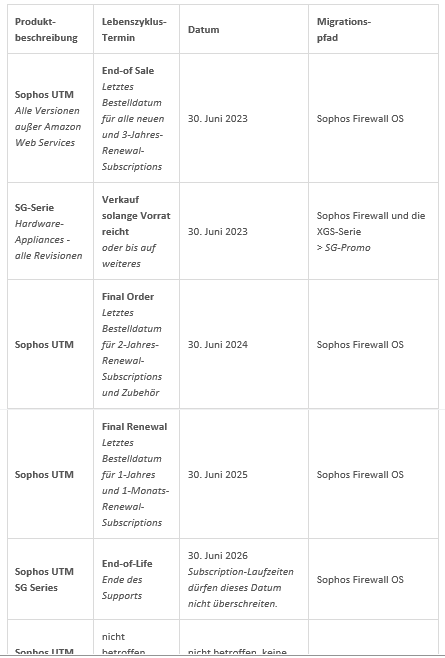
Finally, Sophos announced the EOL of UTM. Interestingly, the EOL does not apply to Sophos UTM AWS....
This thread was automatically locked due to age.
I did use no-ip but you have to log in and reactivate every now and then to keep your DDNS active. freedns is one of the only ones that let you create a DDNS and you never have to worry about it expiring or get solicited to upgrade when you visit the website.
Actually it's the other way around for me in UTM. The UTM won't keep the IP active for FreeDNS and I still have to log in to the site to refresh it. I even contacted Josh there (admin) about UTM and connectivity. He had no idea about the software, what it was or how to make it work (obviously). I have three DDNS names I use for different applications and I always got the e-mail notification about close to expiration.
It's in XG at least, we'll see if it actually works.
OPNSense 64-bit | Intel Xeon 4-core v3 1225 3.20Ghz
16GB Memory | 500GB SSD HDD | ATT Fiber 1GB
(Former Sophos UTM Veteran, Former XG Rookie)
At one point the DDNS updated when using freeDNS but only on first setting it up in the UTM. So I tried both methods:
1.) Web service IPv4
2.) External interface
Both didn't seem to work, with the UTM always saying "no update has been attempted" in the DDNS settings. I'm sure I could do a TCP dump SSH and see what's going on, but maybe paying $2 a month for No-IP would be worth it since it's a caliber or two above freeDNS.
UTM doesn't allow cron jobs for obvious reasons. Sure there are plenty of alternatives of updating FreeDNS but it should work on the UTM if it works on the XG.
As you could easily integrate this via a Script, you could do LE still on SFOS. Even with a Wildcard LE Certificate, which would replace the need of using individual certificates per domain. This is possible via API in DNS and i am using this for years on multiple SFOS firewalls.
__________________________________________________________________________________________________________________
I'm back on the XG again. There's a few issues I need to iron out first but the dynamic DNS works and there's no need anymore to have another method.
The XG actually updates the DDNS every 5 minutes instead of waiting for the IP to change. When I booted into the UTM last time I checked the dyndns page and it showed updated successfully, but for whatever reason it was not updating everytime my IP address changed and therefore I could not access the VPN until I ran my DDNS updater on one of the devices on my LAN..
Anyways about the web filter, it could be described as complicated to set up, especially with the various ways of accomplishing the same thing. Devices on the LAN can bypass SSL/TLS scanning in about 3 different ways. Firewall rules, the SSL/TLS inspection rules, and in the Webfilter exceptions.
alan weir Before I could even consider XG even in testing, I need to figure out how to add wpa_supplicant package to it. It's not worth the time or trouble hooking up the att gateway box in path (ONT --> gateway box --> XG) if I can't bypass it later.
I've been using the wpa bypass since ~2019 with 0 issues. The att gateway box sits in its original box collecting dust. Exactly where it should be.
So far I've been looking at *sense. While better in some ways, worse in others. Albeit, both do support the above package.
I'm back on the UTM again. I tried to get the SSL VPN to work on the XG and I just couldn't seem to be able to connect to any of my devices on the LAN despite having the firewall and NAT rules to allow VPN to access the LAN. But it works flawlessly on the UTM. The VPN is the the only thing holding me back at this point. I will have to follow the guide again and see what happens. PCAP just tells me it is some sort of "SSL Violation". Full tunnel works fine as I can tunnel back out into the internet, but accessing devices on the LAN is for some reason being blocked at the firewall.
You should create own Threads about your issues on SFOS, otherwise this could get confusing quite quickly. About your issue: Likely you are facing this one: SSL VPN "IPv4 lease range" changes OR global settings update gives error "You must enter a network IP address." in SFOS v19.
__________________________________________________________________________________________________________________