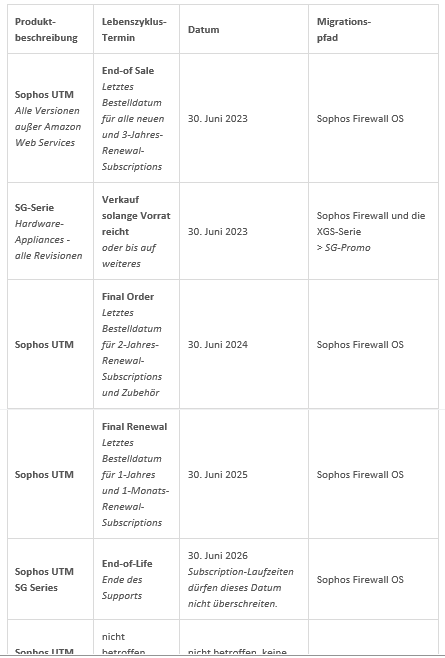
Finally, Sophos announced the EOL of UTM. Interestingly, the EOL does not apply to Sophos UTM AWS....
This thread was automatically locked due to age.
For my opinion - not a smart move.
We (me and the other sys admin) are using both - UTM and XGS.
He use XGS and consider stop working with it, and I'm using UTM and love it (we have two different networks which each one response).
The UTM is rock solid, and VGS suffers from a lot of issues.
Seeing what he is going thru, when the time will come, I'm not sure if i will move to XGS or maybe look for another brand.
The XGS is usable so far as we can say (if you do not migrate from UTM to XGS it´s definitely a good solution for the money (also compared to other vendors).
BUT Sophos is more and more mikling customers than just bring useful UTM features also to XGS or making things much laborious on XGS...
Examples:
no ntp server
no Let´s Encrypt
matching pattern IDs of WAF(for exceptions) only visible in XGS shell log not in GUI
missing S/MIME in E-Mail Protection
NO QUARANTINE for blocked extensions/MIME Types in E-Mail Protection -> blocked attachements will be cutted of the e-mail! You should use Central Mail Protection instead of XGS E-Mail Protection -> Sure...this is x 10 expensiver than XGS Mail Protection Licence - of course at the moment there is a 60% promo but the renewal after 3 years...?
regards
To me, the XG is just a more complete product given that the access points integrate with it and with Sophos Central
Complete is subjective. Considering XG doesn't even have all the features that utm had, it's hard to call it complete. However, if it meets *your* needs, more power to you.
pfBlockerNG is not available on opnsense, it's a pf exclusive.
As for updates, it's a double edged sword. Too frequent updates are just as bad as too few. Somewhere in the middle is preferred. As with any update, there's a process to go through; one of which is to wait for the update to be in the wild for a few weeks-months before applying to make sure there's nothing severely wrong with it. I apply the same strategy to UTM.
Part of the appeal of pf was getting the ear of one of the devs to code a patch for wpa_supplicant to listen on vlan0 (https://reviews.freebsd.org/D40442) for eapol traffic. This is needed on att fiber when bypassing the gateway. All I got from the opnsense dev (franco) was noise and ego. So pass.
Hi. I wouldn't go for open source.
It's nice for home users but not for a big commercial system.
Few more things to consider out of the obvious:
Hi Goldy,
open source systems are cheaper, you can choose you own preferred hardware, most of them also have great hardware support (10G SFP+ is no problem) and there are many companies which offer commercial support. For sure they have less big bugs (just compare the big exploits in the last 2-3 years on Sophos, Fortinet and PAN).
bye Josef
BERGMANN engineering & consulting GmbH, Wien/Austria
PFSense is based off NetGate firewall software, so it's not like Billy Bob and his inbred cousins created it from a moonshine apparatus, lol.
Frankly, I'll take the learning curve now after experiencing the dumpster runoff of XG - after all of the troubles I've had with it just this week alone, I've had enough, and I'd gladly go to an open-source solution or other product altogether. The attitudes of a particular couple of Sophos staff that interact with us can be atrocious at times. I've been using this product most likely longer than they've been employed at Sophos, and it's just... mind boggling.
I said something in another post, but this will be my last week most likely posting help here. My new access points came in this afternoon, and I will be removing everything I have that is Sophos.
o7.
OPNSense 64-bit | Intel Xeon 4-core v3 1225 3.20Ghz
16GB Memory | 500GB SSD HDD | ATT Fiber 1GB
(Former Sophos UTM Veteran, Former XG Rookie)
As Jay Jay suggest, yesterday I decided to have a look at pfSense.
I installed it on a VM and started playing around with it.
At first I was not impressed, but then I realized I can add many packages (Snort, Squid, pfBlockerNG, Web proxy…).
The interface is great and in no time I felt at home and familiar with it.
It has many of what you can expect from a NGFW, and it's a software version, which for me is a big advantage. Quite impressive.
Saying that, it lacks some functions that are essential for me.
Also, after all, it's a standard NGFW. (Very flexible and VERY user friendly - but still...)
Of course, since it's open source, the price will be a fraction of what I would pay for an equivalent NGFW.
Moving from Sophos UTM, I would like some extra benefit.
I didn't rule out this option though.
Hi Jay jay
Application control for example, WAF, Email protection, good Threat Protection...
I also had a look at Opesense. Very nice also, but since I have quite big internal net and about 1500 devices, and since all the good plugins (Zenarmor...) cost money, in the end it's not that far from commercials Brands.
Also, not sure if I can have a good reliable (I don't mind pay for it) support.
My needs:
I still have time, but it's nice to look around
Application control equivalent - ?
WAF - HAProxy
Email protection - ?
There's suricata for IPS
If you need all of those functions, pf may not be the best AIO package for your needs.
With that many users, is this not being used in a commercial environment?
It's going to be expensive to get that with any other product. For example, if you went with Untangle NG, an unlimited device subscription....is (wait for it..) $5,400 a year.
Zenarmor starts at $50 per month but you have to contact their sales team to get a quote for for the 2,000+ users plan.
The closest thing to application control that might be free is the OpenAppID plugin for Snort.
It's going to be expensive to get that with any other product. For example, if you went with Untangle NG, an unlimited device subscription....is (wait for it..) $5,400 a year.
Zenarmor starts at $50 per month but you have to contact their sales team to get a quote for for the 2,000+ users plan.
The closest thing to application control that might be free is the OpenAppID plugin for Snort.
I'm pretty sure the latest version of snort 3.0 has it built-in. I never used that or pfSense so I'm just going by what the snort blog says.
Yeah, $5,400 is probably a good price for a business with unlimited users. Who knows how much Sophos is a year, but at least Untangle/Arista is transparent about their pricing and you can use your own hardware and not tied to an appliance.