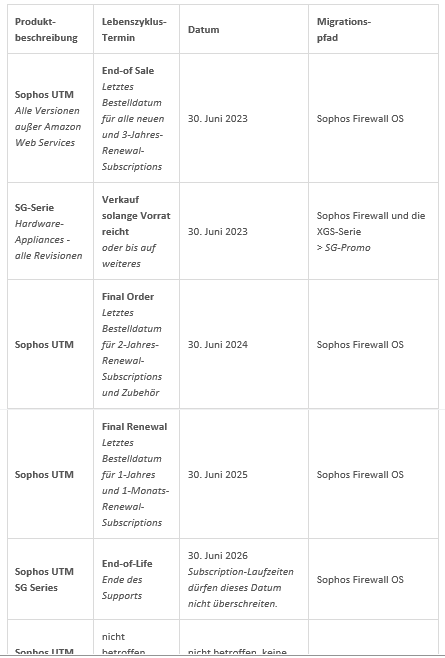
Finally, Sophos announced the EOL of UTM. Interestingly, the EOL does not apply to Sophos UTM AWS....
This thread was automatically locked due to age.
Well I finally transitioned to the XG. Got it all configured and working just right. UTM was nice but nothing lasts forever. Goodbye, UTM
Some things I will miss from the UTM:
Seeing right from the dashboard what modules are active/inactive without having to inspect the firewall rules.
Portscan detection with email alerts, (even though it is useless).
How simple it is to convert DHCP leases into static hosts definitions.
How much faster it boots compared to the XG.
The ability to drag-and-drop service and network definitions into firewall and NAT rules
Realtime logs for every component. XG is supposed to have them but you still have to hit the refresh button.
Easy click and enable IPS rules.
Look at the roadmap of XG, it seems to be planned out with business/corporate features in mind, with no new features planned that home users can even take advantage of. Therefore the XG could be considered like a final product already that is good enough for a home environment and has enough feature parity to the UTM that it has no real issues besides the learning curve.
The only real thing I am concerned about is the EOL of the access points in December that will need to be managed through the Sophos Central Wireless when using the XG, which I cannot get my AP15 to synchronize with. If worse comes to worse I will still have my copy of UTM that I can use just in case that will still be able to manage the APs.
I just wish Sophos would include UEFI bios support and a newer kernel in the next version of XG but who knows.....
Same here. 3 years is a huge time frame in IT. Given how the world did look out 3 years ago (the time before corona) changes are huge and mostly not expected (at least not by me).
If in 3 years such a thing like on-premise endpoint security is still a viable part of corporate infrastructure, XG will certainly be among the options to evaluate. For now we stick to UTM.
Same here. 3 years is a huge time frame in IT. Given how the world did look out 3 years ago (the time before corona) changes are huge and mostly not expected (at least not by me).
If in 3 years such a thing like on-premise endpoint security is still a viable part of corporate infrastructure, XG will certainly be among the options to evaluate. For now we stick to UTM.
I tried to stick with the UTM but a few issues with the DDNS updater not working has made me decide to migrate.
There are simply more features in the XG to enhance security, such as MFA and support for TLS 1.3 decryptions. I doubt any of these features will be added to the UTM. Do you think sophos will sell the UTM to another developer the way Astaro sold it to sophos, or is it pretty much dead?
alan weir Depending who your domain registrar is, it may be possible to handle ddns directly from the server in question using an API. I use cloudflare as my domain registrar and name server. They offer api access to update dns records. When I was on cable, a script ran daily (maybe twice a day) to verify public facing IP then update server.domain.com's A record if changed.
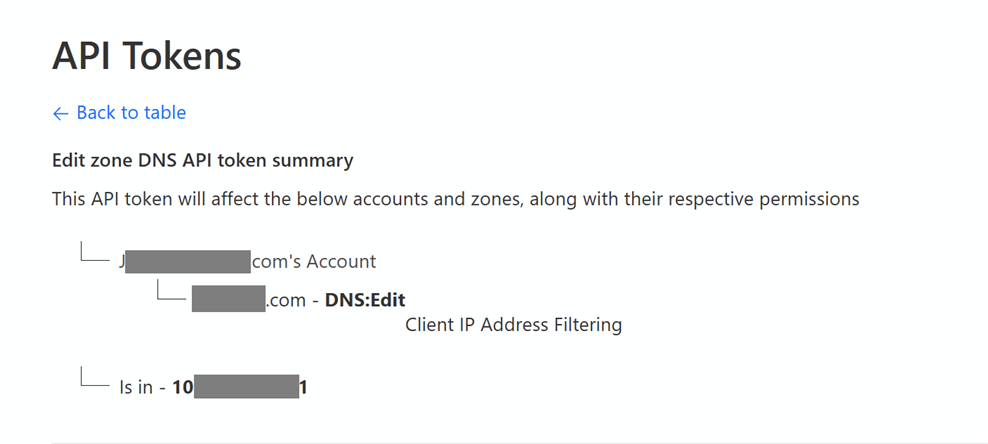
This api token allows only dns editing for requests coming from a particular ip (my ip only).
This worked quite well at the time. Realistically the only time it changed was when the mac presented to the modem changed. Since switching to fiber my IP hasn't changed in 5 years so it's not off much importance any more.
Re web filter/tls, it may make some sense to run xg in parallel with the firewall of choice (ie pfsense) to proxy such traffic¿?
Open source or resell UTM would be nice options. It could use a proper update. Selling it to someone else? Doubtful, that would help a competitor. Why would a business want to create competition to itself....
I did use no-ip but you have to log in and reactivate every now and then to keep your DDNS active. freedns is one of the only ones that let you create a DDNS and you never have to worry about it expiring or get solicited to upgrade when you visit the website.
Actually it's the other way around for me in UTM. The UTM won't keep the IP active for FreeDNS and I still have to log in to the site to refresh it. I even contacted Josh there (admin) about UTM and connectivity. He had no idea about the software, what it was or how to make it work (obviously). I have three DDNS names I use for different applications and I always got the e-mail notification about close to expiration.
It's in XG at least, we'll see if it actually works.
OPNSense 64-bit | Intel Xeon 4-core v3 1225 3.20Ghz
16GB Memory | 500GB SSD HDD | ATT Fiber 1GB
(Former Sophos UTM Veteran, Former XG Rookie)
At one point the DDNS updated when using freeDNS but only on first setting it up in the UTM. So I tried both methods:
1.) Web service IPv4
2.) External interface
Both didn't seem to work, with the UTM always saying "no update has been attempted" in the DDNS settings. I'm sure I could do a TCP dump SSH and see what's going on, but maybe paying $2 a month for No-IP would be worth it since it's a caliber or two above freeDNS.
UTM doesn't allow cron jobs for obvious reasons. Sure there are plenty of alternatives of updating FreeDNS but it should work on the UTM if it works on the XG.
I'm back on the XG again. There's a few issues I need to iron out first but the dynamic DNS works and there's no need anymore to have another method.
The XG actually updates the DDNS every 5 minutes instead of waiting for the IP to change. When I booted into the UTM last time I checked the dyndns page and it showed updated successfully, but for whatever reason it was not updating everytime my IP address changed and therefore I could not access the VPN until I ran my DDNS updater on one of the devices on my LAN..
Anyways about the web filter, it could be described as complicated to set up, especially with the various ways of accomplishing the same thing. Devices on the LAN can bypass SSL/TLS scanning in about 3 different ways. Firewall rules, the SSL/TLS inspection rules, and in the Webfilter exceptions.
alan weir Before I could even consider XG even in testing, I need to figure out how to add wpa_supplicant package to it. It's not worth the time or trouble hooking up the att gateway box in path (ONT --> gateway box --> XG) if I can't bypass it later.
I've been using the wpa bypass since ~2019 with 0 issues. The att gateway box sits in its original box collecting dust. Exactly where it should be.
So far I've been looking at *sense. While better in some ways, worse in others. Albeit, both do support the above package.