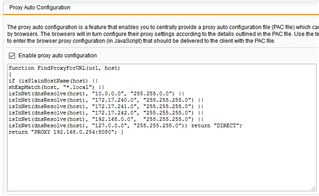
Hello
We are using an SG210 running 9.411-3.
The UTM is already the default gateway for all of our servers. I intend to use AD groups for SSO. Is it necessary for me to publish a GPO to each user or server saying it's web proxy is the UTM?
Many thanks
This thread was automatically locked due to age.