I'm trying to run Sophos UTM in Full Transparent mode using a bridged network connection, however web filtering is not working. These forums have a lot of information but I still haven't been able to solve this. If anyone can spot the issue or any other tips I'd really appreciate it!
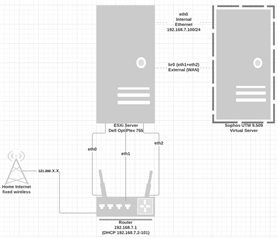
The network is physically connected as:
ISP modem <-> Sophos UTM <-> Router #1 <-> Router #2
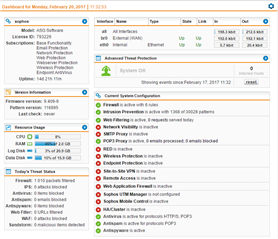
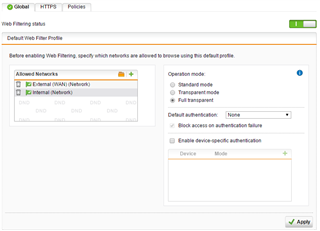
Internet traffic flows through fine, but the Dashboard always says "Web Filtering is active, 0 requests served today" whether I browse the web through Router #1 or Router #2.
Sophos UTM 9.409 has been installed based on these instructions:
http://www.fastvue.co/sophos/blog/easily-evaluate-sophos-utm-9-3-using-full-transparent-mode/
Sophos UTM was installed as a VM on ESXi 6.0 Update 2. ESXi is running on a Dell Optiplex 755 with a 2- NIC network card installed for the bridged interface, and the onboard NIC is used for management.
The management port and the LAN port are plugged into Router #1, while the WAN port is plugged into the ISP modem.
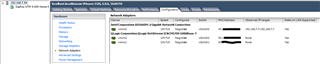
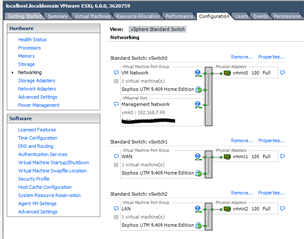
vSphere Client > 192.168.7.99 > Configuration > Networking:
- vmnic0
- Management network
- 192.168.7.99
- vmnic1
- WAN
- Promiscuous mode turned on
- vmnic2
- LAN
- Promiscuous mode turned on
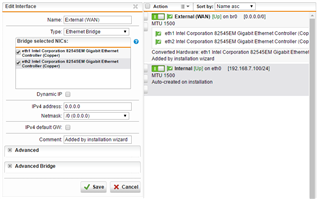
Sophos UTM web admin > Interfaces & Routing > Interfaces:
- eth0
- "Internal"
- Dynamic IP: unchecked
- 168.7.100/24
- br0
- "External (WAN)"
- Dynamic IP: unchecked
- 0.0.0/0
- IPv4 default GW: unchecked
Router #1:
- 192.168.7.1
- DHCP enabled (192.168.7.2 to 101)
- DHCP reservations for:
- 192.168.7.2 (Router #2)
- 192.168.7.99 (ESXi server)
Router #2:
- 192.168.7.2
- OpenWRT running as access point
I added the Any / Any / Any firewall rule as noted in the instructions.
Sophos UTM > Support > Tools > Ping Check always returns "Ping check did not deliver a result, because of a probably non-existing ip address / hostname." whether I use the "Internal" or "External (WAN)" interface.
This thread was automatically locked due to age.