This was from a different thread ( community.sophos.com/.../73266 that was abandoned:
I run a core/full transparent utm/border configuration. This works entirely until I turn on the web filter, at which point HTTP and HTTPS traffic fails to traverse. So, the routing is correct--I'm using that link presently to post this.
However, when I toggle on the web filter, I don't even see any entries hitting it. All other protocols traverse.
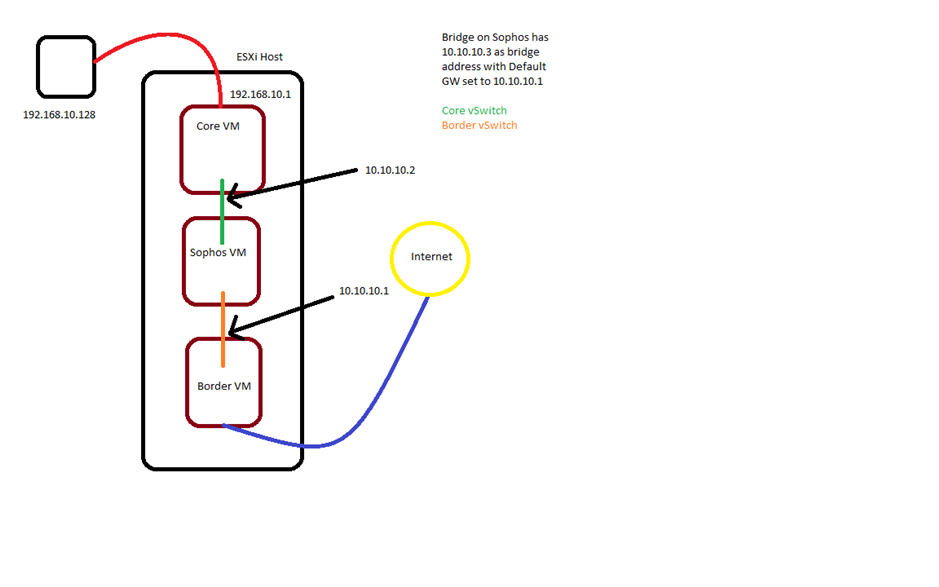
This is an ESXi environment--a trunk comes in from my internal network to the core router. The core and UTM both share a vswitch, and the border and the UTM both share a vswitch. Promiscuous mode is on those vswitches.
These were the last steps I undertook:
I rebuilt Sophos from the ground up. Fresh install, assign interfaces, create bridge and management, assign proper gateway to bridge, create any/any/any firewall rule, toggle on firewall rule, assign DNS, get Sophos up-to-date, test the bridge successfully (full normal connectivity), turn on Web Filter and immediately lose web browsing by HTTP or HTTPS. All other protocols still work. Turn web filter off and all connectivity resumes.
Everything tests fine--DNS test from Sophos and my internal nets and core are great, routing is all fine, the bridge works and passes traffic from core to border. It just refuses to transparently proxy when I toggle it on.
Does anyone have any ideas? I'm going to throw a VM on that core-UTM vswitch to see if I can find anything amiss and will report back. But I'm pretty puzzled at this point.
This thread was automatically locked due to age.