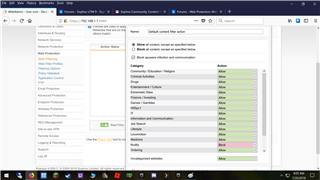
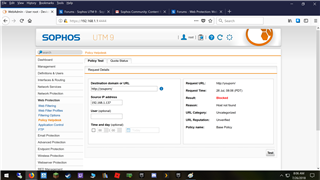
I adjusted Default Content Filter action to prevent Nudity sites from being accessible with success a couple years ago. However, I checked the other day, and even though my setting are still intact, I am able to access Nudity sites. If I use the policy test option, it says "blocked" as it should. But, again, I am able to open a browser and access Nudity sites. This feature was working perfectly last year. Not sure when it stopped. Suggestions?
This thread was automatically locked due to age.