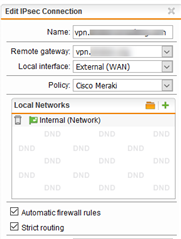
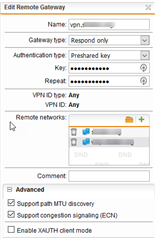
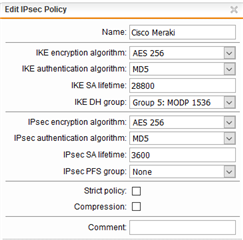
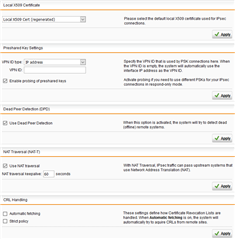
Our IPSec VPN connection between a Sophos UTM (server) and Cisco Meraki MX (client) used to work just fine, but we didn't use it for a few weeks while testing a security appliance. Now, when have switched it back on, it keep "disconnecting" every 12 hours or so. Well, I am not sure if I should actually say "disconnecting" because both appliances claim that the connection is up. However, it is not possible to ping any devices.
Here is a copy of the UTM log:
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: initiating Main Mode to replace #23
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: received Vendor ID payload [XAUTH]
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: ignoring Vendor ID payload [Cisco-Unity]
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: received Vendor ID payload [RFC 3947]
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: received Vendor ID payload [Dead Peer Detection]
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: enabling possible NAT-traversal with method 3
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: NAT-Traversal: Result using RFC 3947: no NAT detected
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: received Vendor ID payload [Dead Peer Detection]
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: Peer ID is ID_IPV4_ADDR: '108.xxx.xxx.xxx'
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: Dead Peer Detection (RFC 3706) enabled
2017:12:17-17:58:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #30: ISAKMP SA established
2017:12:17-22:51:17 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #31: responding to Quick Mode
2017:12:17-22:51:17 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #31: IPsec SA established {ESP=>0x054606b6 <0x1aeff575 DPD}
2017:12:17-22:51:33 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #32: responding to Quick Mode
2017:12:17-22:51:33 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #32: IPsec SA established {ESP=>0x0a623787 <0x6836e0ac DPD}
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: initiating Main Mode to replace #27
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: received Vendor ID payload [XAUTH]
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: ignoring Vendor ID payload [Cisco-Unity]
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: received Vendor ID payload [RFC 3947]
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: received Vendor ID payload [Dead Peer Detection]
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: enabling possible NAT-traversal with method 3
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: NAT-Traversal: Result using RFC 3947: no NAT detected
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: received Vendor ID payload [Dead Peer Detection]
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: Peer ID is ID_IPV4_ADDR: '108.xxx.xxx.xxx'
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: Dead Peer Detection (RFC 3706) enabled
2017:12:18-00:22:46 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #33: ISAKMP SA established
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: initiating Main Mode to replace #30
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: received Vendor ID payload [XAUTH]
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: ignoring Vendor ID payload [Cisco-Unity]
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: received Vendor ID payload [RFC 3947]
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: received Vendor ID payload [Dead Peer Detection]
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: enabling possible NAT-traversal with method 3
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: NAT-Traversal: Result using RFC 3947: no NAT detected
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: received Vendor ID payload [Dead Peer Detection]
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: Peer ID is ID_IPV4_ADDR: '108.xxx.xxx.xxx'
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: Dead Peer Detection (RFC 3706) enabled
2017:12:18-01:48:30 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #34: ISAKMP SA established
2017:12:18-05:15:17 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #35: responding to Quick Mode
2017:12:18-05:15:17 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #35: IPsec SA established {ESP=>0x008ba779 <0x8549f156 DPD}
2017:12:18-05:15:33 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #36: responding to Quick Mode
2017:12:18-05:15:33 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_1"[2] 108.xxx.xxx.xxx:4500 #36: IPsec SA established {ESP=>0x00aef0e8 <0xfc15c757 DPD}
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: initiating Main Mode to replace #33
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: received Vendor ID payload [XAUTH]
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: ignoring Vendor ID payload [Cisco-Unity]
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: received Vendor ID payload [RFC 3947]
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: received Vendor ID payload [Dead Peer Detection]
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: enabling possible NAT-traversal with method 3
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: NAT-Traversal: Result using RFC 3947: no NAT detected
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: received Vendor ID payload [Dead Peer Detection]
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: Peer ID is ID_IPV4_ADDR: '108.xxx.xxx.xxx'
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: Dead Peer Detection (RFC 3706) enabled
2017:12:18-08:12:32 vpn pluto[5639]: "S_REF_IpsSitHomeOffice_0"[2] 108.xxx.xxx.xxx:4500 #37: ISAKMP SA established
I have reset the connection at 8:12:32 in the morning.
And, here is a copy of the Cisco Meraki log (newest first):
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=3954588980(0xebb63d34)"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=158523040(0x972dea0)"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=2089720425(0x7c8e9a69)"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=230688225(0xdc005e1)"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:b9b1494c9a66dc21:b9e76dfea26a140f"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: initiate new phase 1 negotiation: 108.xxx.xxx.xxx[500]<=>192.198.xxx.xxx[500]"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: phase1 negotiation failed due to time up. 3336d6acd6937d2d:ad0171cbc22a8d42"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: ignore information because ISAKMP-SA has not been established yet."
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: phase2 negotiation failed due to time up waiting for phase1. ESP 192.198.xxx.xxx[0]->108.xxx.xxx.xxx[0]"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: phase2 negotiation failed due to time up waiting for phase1. ESP 192.198.xxx.xxx[0]->108.xxx.xxx.xxx[0]"
12/18/2017 8:46 Non-Meraki / Client VPN negotiation "msg: ignore information because ISAKMP-SA has not been established yet."
12/18/2017 8:45 Non-Meraki / Client VPN negotiation "msg: ignore information because ISAKMP-SA has not been established yet."
12/18/2017 8:45 Non-Meraki / Client VPN negotiation "msg: ignore information because ISAKMP-SA has not been established yet."
12/18/2017 8:45 Non-Meraki / Client VPN negotiation "msg: ignore information because ISAKMP-SA has not been established yet."
12/18/2017 8:45 Non-Meraki / Client VPN negotiation "msg: initiate new phase 1 negotiation: 108.xxx.xxx.xxx[500]<=>192.198.xxx.xxx[500]"
12/18/2017 8:12 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:cd6c36d9a4ec966d:ff844b42146d879d"
12/18/2017 8:12 Non-Meraki / Client VPN negotiation "msg: renegotiating phase1 to 192.198.xxx.xxx due to active phase2"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-MESSAGE-ID received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-ID-INFORMATION received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-MESSAGE-ID received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-ID-INFORMATION received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-ID-INFORMATION received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-MESSAGE-ID received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: notification INVALID-ID-INFORMATION received in informational exchange."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=1886330414(0x706f1e2e)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=196593425(0xbb7c711)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:11289a46c91f56ad:68c1afbe3f149b5d"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 1 negotiation: 108.xxx.xxx.xxx[500]<=>192.198.xxx.xxx[500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: unknown Informational exchange received."
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=1591540275(0x5edcfa33)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=64989369(0x3dfa8b9)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:2f8a3f6d7df722ba:9e6d4db19d5d7a93"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 1 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=1953692317(0x7472fa9d)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=244177405(0xe8dd9fd)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=2887914446(0xac2213ce)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=165247522(0x9d97a22)"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:ba6541d4081a4f69:88e40ba2a7b47420"
12/18/2017 6:52 Non-Meraki / Client VPN negotiation "msg: initiate new phase 1 negotiation: 108.xxx.xxx.xxx[500]<=>192.198.xxx.xxx[500]"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=4229285719(0xfc15c757)"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=11464936(0xaef0e8)"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=2236215638(0x8549f156)"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=9152377(0x8ba779)"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 5:15 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/18/2017 1:58 Non-Meraki / Client VPN negotiation "msg: unknown Informational exchange received."
12/18/2017 1:48 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:ba0ebeb3c0c3ae8a:ac8ee5db5decf03d"
12/18/2017 0:22 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:9b462bd8c9c55256:91e498e64f896fcf"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=1748426924(0x6836e0ac)"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=174208903(0xa623787)"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=451933557(0x1aeff575)"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: IPsec-SA established: ESP/Tunnel 108.xxx.xxx.xxx[4500]->192.198.xxx.xxx[4500] spi=88475318(0x54606b6)"
12/17/2017 22:51 Non-Meraki / Client VPN negotiation "msg: initiate new phase 2 negotiation: 108.xxx.xxx.xxx[4500]<=>192.198.xxx.xxx[4500]"
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 21:19 Non-Meraki / Client VPN negotiation "msg: Invalid exchange type 243 from 197.158.83.166[500]."
12/17/2017 17:58 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:38f2d760483fb829:098f10d365f71d2e"
12/17/2017 17:58 Non-Meraki / Client VPN negotiation "msg: ISAKMP-SA established 108.xxx.xxx.xxx[4500]-192.198.xxx.xxx[4500] spi:38f2d760483fb829:098f10d365f71d2e"
Based on a log entry in our PBX system, the local phones got "disconnected" starting 10:52 pm on 12/17, but I don't see any unusual messages in the log except the ones with IPs that don't belong to me.
Any help is appreciated!
This thread was automatically locked due to age.