I've had a working site-to-site IPsec VPN working for years but a few days ago a blackout took out one of the Sophos UTMs and so I find myself configuring it from scratch and I have been at it for a day with no progress.
Two Sophos UTMs -- connecting a 192.168.2.0 network with a 10.1.1.0 network
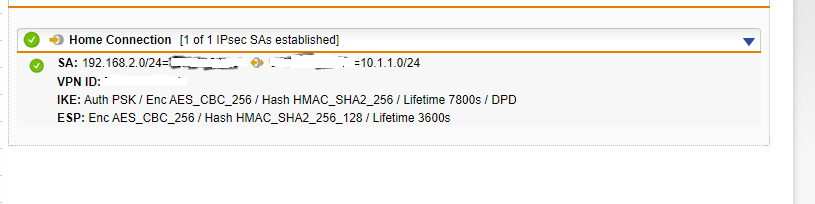
The connection has a green dot and when I look at the details it has
192.168.2.0/24=the ip addess for the internet connection at the location of the 192.168.2.0 network <an icon> ip for the 10.1.1.0 network = 10.1.1.0/24
I have disabled everything else in an effort to debug and the only rule in the firewall is local network -- any - any on both machines.
The machine that did not need recreating had a masquerading rule of the remote network to the local network I've tried adding the opposite to the reconstructed UTM and I have tried without any masquerading rules since none of the online guides mention a need and the same results for both ways.
The connection seems to be good but I can't access shares or sites on the other network.
Any suggestions?
This thread was automatically locked due to age.



 Thank you for the assistance
Thank you for the assistance