Hello,
I have a problem I cannot solve on my own:
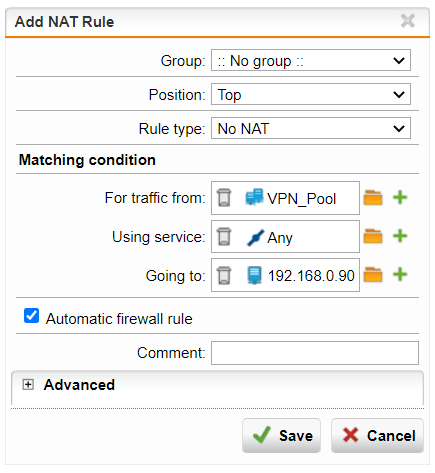
I need a IPSec VPN access to our network (192.168.0.0/24 ) behind our Sophos UTM (192.168.0.10). On our Network I need to access a certain server (192.168.0.90) with a fixed IP Address originating in this network (e.g. 192.168.0.111). This is due to the used protocols (DICOM) and a fixed configuration of the server and cannot be changed.
I defined a VPN Pool inside this network 192.168.0.111/32; the VPN Tunnel works and the connecting client says it got the IP Address as assigned, so far so good.
When accessing the server (192.168.0.90) as planed, the server gets the request from the IP Address of the UTM (192.168.0.10) and not from 192.168.0.111 as it should be. Without getting the request from 192.168.0.111 the server cannot answer to the request and it has to see the assigned address (192.168.0.111) and not the one from the UTM (192.168.0.10).
How can I change the behaviour of the firewall not to interpose itself in the communication?
Thanks a lot in advance for pointing me in the right direction!
This thread was automatically locked due to age.