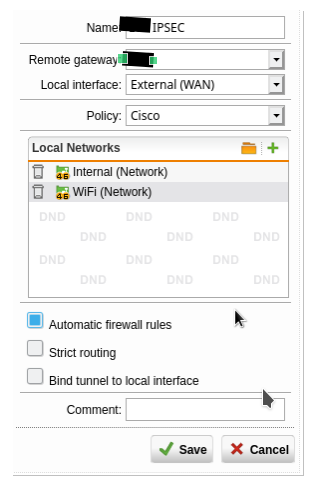
I have a UTM version 9.705-3 with two subnets, LAN 192.168.100.0/24 on eth0 and WIFI 192.168.200.0/24 on eth2 that are connecting via IPSEC site-to-site VPN to a FortiGate appliance with hundreds of subnets. so I've configured the remote network on the UTM as 10.0.0.0/8.
Here's a text network map
LAN (eth0) 192.168.100.0/24 10.1.0.0/16
UTM <-> IPSEC VPN <-> FortiGate 10.2.0.0/16
WIFI (eth2) 192.168.200.0/24 ...
10.201.0.0/24
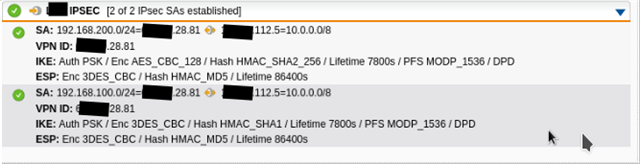
Everything works normally from the LAN network on the UTM. But the WIFI network on the UTM cannot communicate over the VPN. I have both local subnets in the VPN SA. When I ping any host on the remote network from the WIFI network I can see the ping go out and the reply come back in using tcpdump on the UTM console but the reply comes in on the LAN interface eth0 and not the WIFI interface eth2. The packet is never routed to the WIFI network and the host where I started the ping gets a connection timeout. What am I doing wrong?
Here's my IPSEC VPN status
And my settings
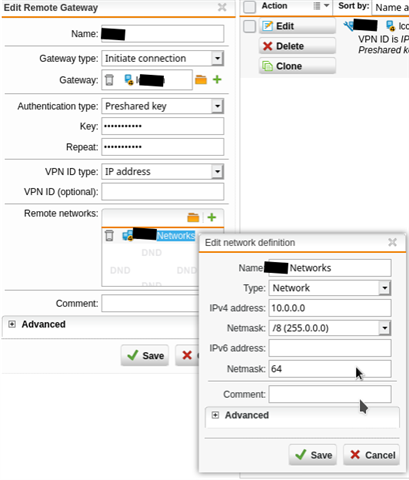
This thread was automatically locked due to age.


