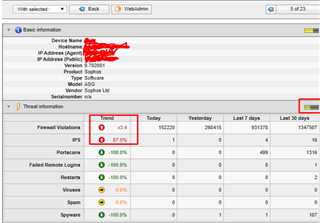
Hello! I just integrated Sophos Alert with my Service Desk software to open tickets regarding high risk alerts with Intrusion Prevention and Advanced Threat Protect.
Fortunately most of them are alerts of temporary files, cache or even false positivos and they disappear in next day or few days. However there are some that need attention if they persist.
So I created a scheduled ticket every week to check SUM and see if there are any major threats. Regarding only security level (Threat), what risk level should I take an action in this print: 
Thank you!
This thread was automatically locked due to age.