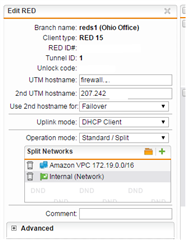
I have an SG220 with one office using a RED15, and an Amazon VPC connection via IPSEC. Network layout is:
SG220 LAN: 172.21.0.0/16
RED: 172.22.2.0/24
IPSEC to Amazon VPC: 172.19.0.0/16
Goal: permit traffic between the Amazon VPC and RED networks.
I have set up the following:
- Added Amazon VPC network to the Split Networks list on the RED connection.
- Added RED network to the Local Networks on the IPSEC connection.
- On the Amazon VPC side, VPN Connection, added the RED subnet as a Static Route.
- Verified the Amazon VPC Route table contains the RED subnet as a route to the gateway, just like the SG LAN
I can actually see the packets get all the way to the Amazon VPC, but no traffic goes back from Amazon to the RED network. Firewall rules seem fine (auto-created everywhere applicable).
Anything I missed?
This thread was automatically locked due to age.