Hello all,
Hope everyone is staying safe in these times. Warning I'm a "newb" to Sophos items still and intermediate in networking, but I learn fast. :) )
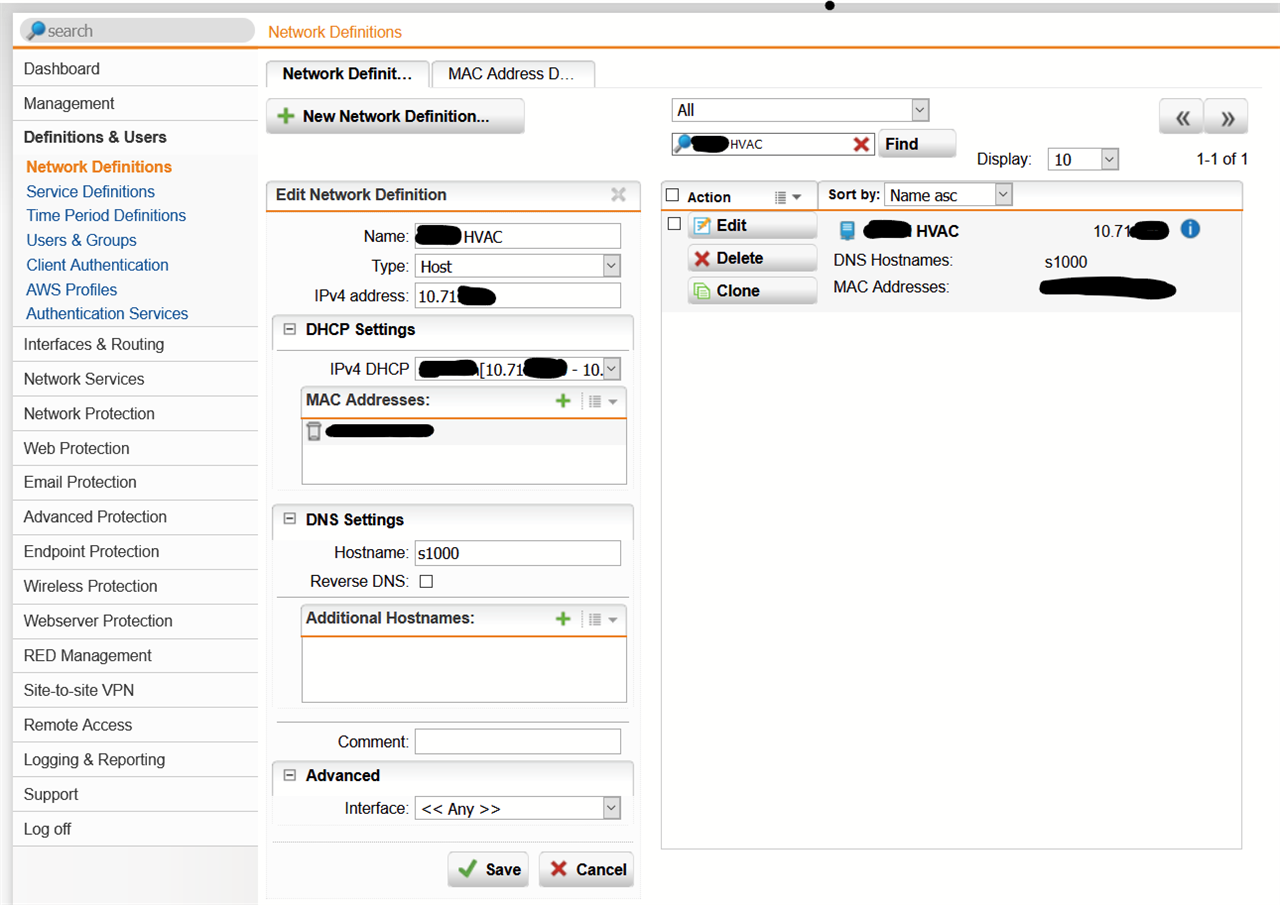
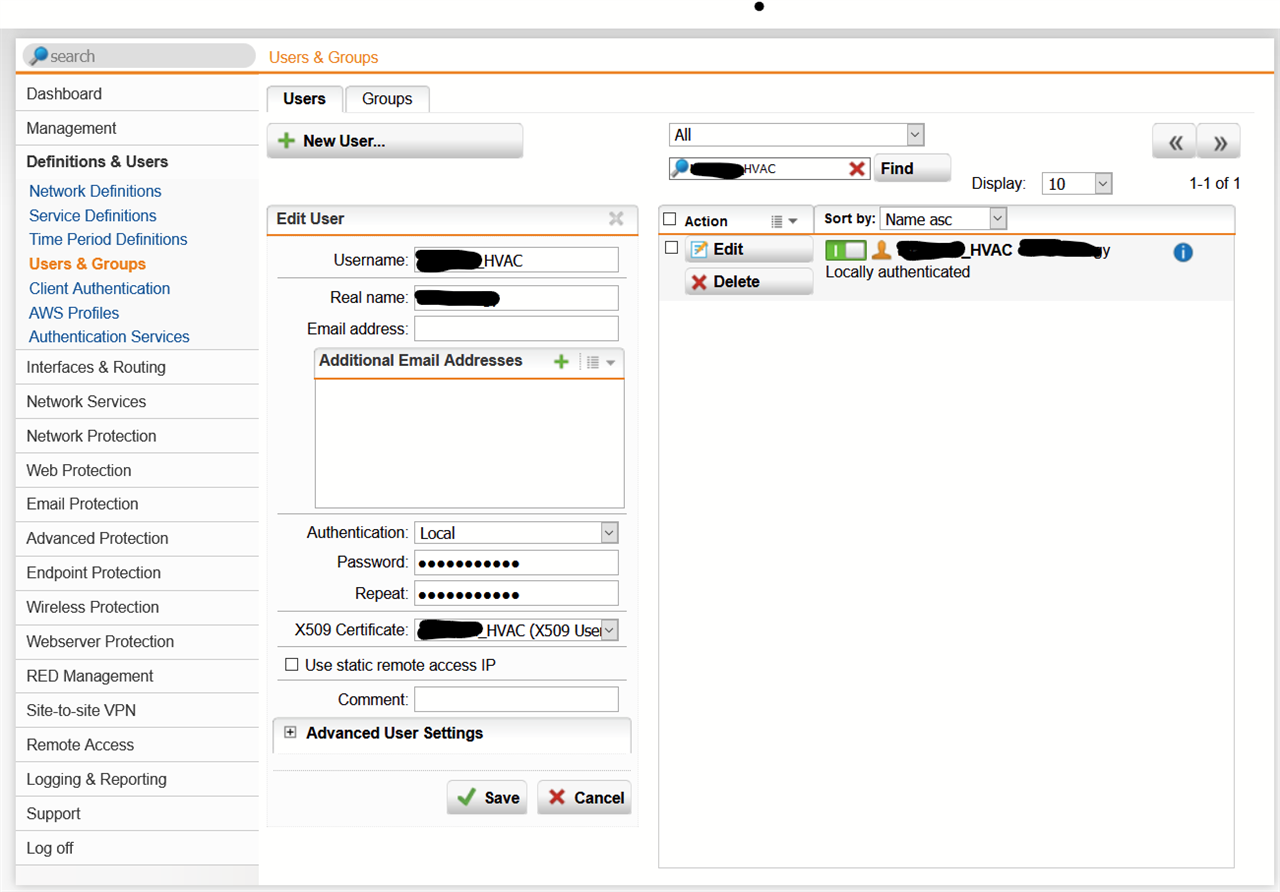
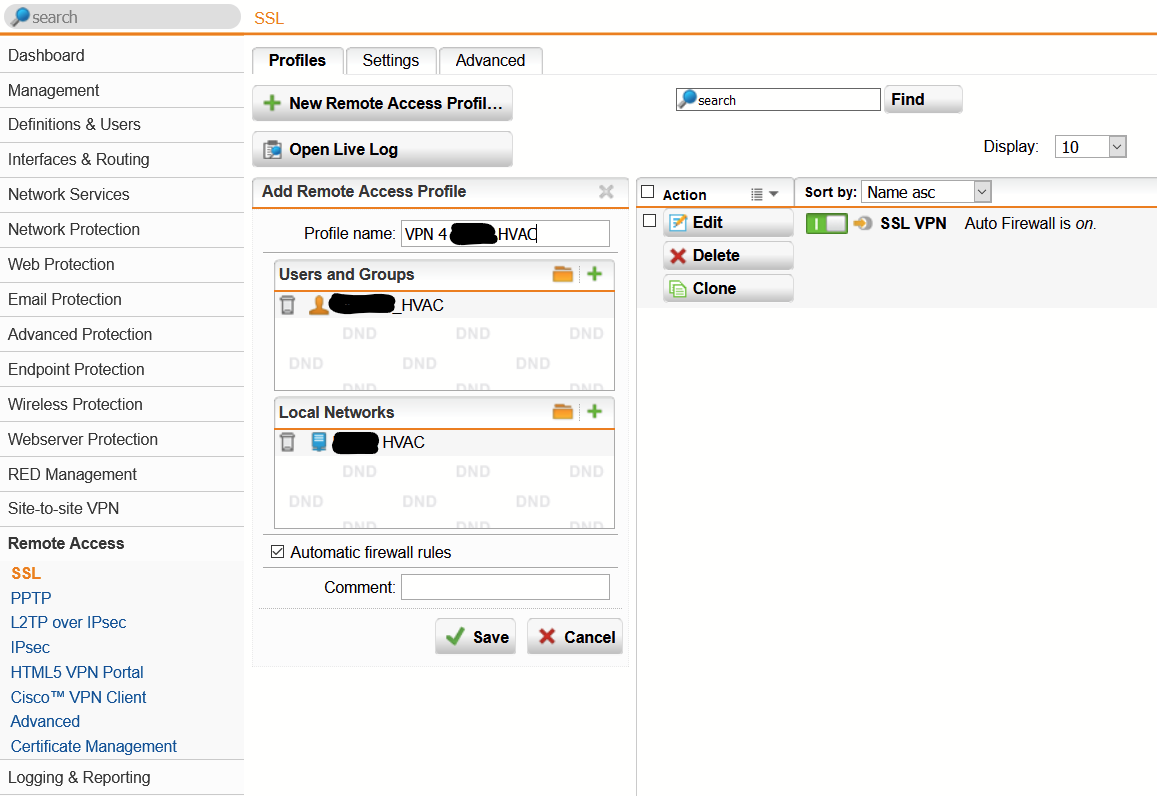
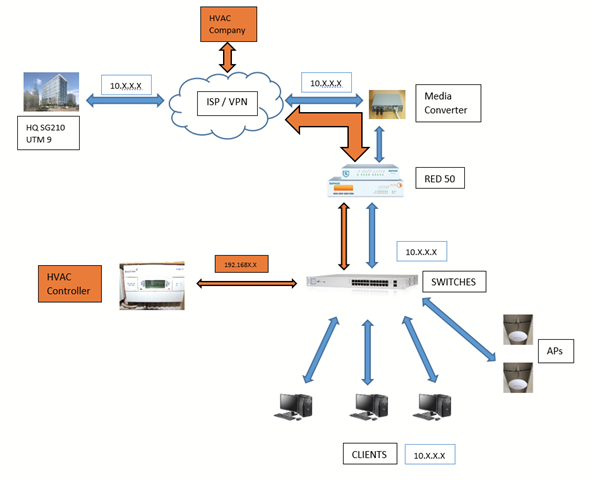
We have a remote building that uses a RED50 to tunnel back to us here at HQ. Our builder requires access to the HVAC system via VPN to their controller. Presently the RED is configured in Standard / Unified. We have 3 Static Public IPs available for the site and I was looking at providing access to their HVAC Controller via the RED50 using one of these IPs. Can this be done and if so I assume the RED would have to be configured to Standard / SPLIT? I want to split out all of our sites anyhow, now that we are going to be using Exchange/Office Online.
This thread was automatically locked due to age.